Public WiFi hotspots can usually be found in abundance wherever we go. So much so that many of us are now frustrated when there is no WiFi for us to use. If you're at a coffee shop, hotel, bar, restaurant or even a non-stationary location like a train, you can scan for WiFi hotspots and most of the time strike it lucky. But just how safe is it to use a WiFi hotspot and what are the risks involved with using a network when you don't know who's lurking nearby?
Introduction
Just yesterday, Europol's Cybercrime chief, Troels Oerting, issued a warning about using public WiFi networks. He highlighted the growing number of attacks taking place on these networks and how easy it is for an attacker to carry them out. Even the European parliament recently shut down their own public WiFi network after they found it was being used to launch attacks, it could just as easily happen anywhere else. To highlight how widespread the usage of WiFi networks is, I refer to August 2011 when the Office for National Statistics (ONS) published a statistical bulletin titled "Internet Access - Households and Individuals". One of the key points of the bulletin is that in the 12 months from August 2010 to August 2011 the use of WiFi hotspots had almost doubled from 2.6 million people to 4.9 million people. Assuming a similar level of growth from 2011 until the time of writing this article, that would mean that 17.2 million of us regularly use a WiFi hotspot. Given the proliferation of smartphones, tablets, notebooks, netbooks and laptops, it's not a huge leap to expect that that kind of growth could have been maintained. With the integration of services like email and social media into our everyday lives and the convenience of reading the news or watching our favourite tv show on the go, it's easy to see where such an expectation of free or cheap access to fast and reliable Internet access stemmed from.

How WiFi works
The term WiFi is short for Wireless Fidelity and was coined by the WiFi Alliance. The WiFi Alliance is a trade body that certifies products as conforming to their standards of interoperability. This means that no matter what brand of router, access point or wireless card you're using, they will all 'play nice and get along'. Perfect for those busy coffee shops where everyone has different devices.
The explosive rise of WiFi networks can be attributed to the cable free nature of network access. Traditional wired networks historically offered slightly faster speeds, but for almost all uses WiFi is now capable of offering a comparable level of service, without the need to be tethered by a cable. Instead of sending electrical signals down a copper wire, a WiFi capable device will transmit your information as radio waves through the air. The convenience of wire free Internet access on your device is now so widespread that almost any household with an Internet connection will most likely have a WiFi network to go with it.
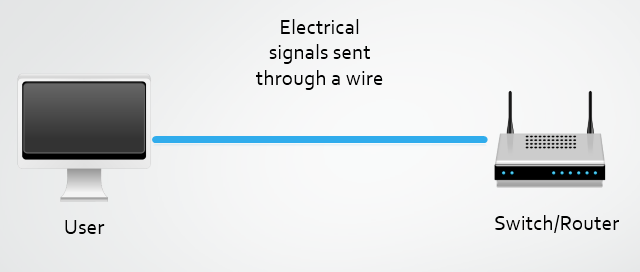

The problem
To do harm, an attacker needs to be able to gain access to your network traffic. Once they have access, they can spy on you to see what it is that you're doing, or, get a little more creative and effect a Man in The Middle (MiTM) attack. They could hijack your sessions like this or this to gain access to your accounts, inject code into websites you visit to steal usernames and password like this or they can even make you visit websites that you didn't intend to like this. What's more frightening is that we're talking about the tip of the iceberg. To do this on a wired network an attacker needs physical access to the network. Because all of your traffic is sent as electrical signals down a cable, they need to be able to connect to the cable or some form of network equipment like a switch. This usually entails some form of physical intrusion into a building or property, which is commonly the first line of defense on a wired network.
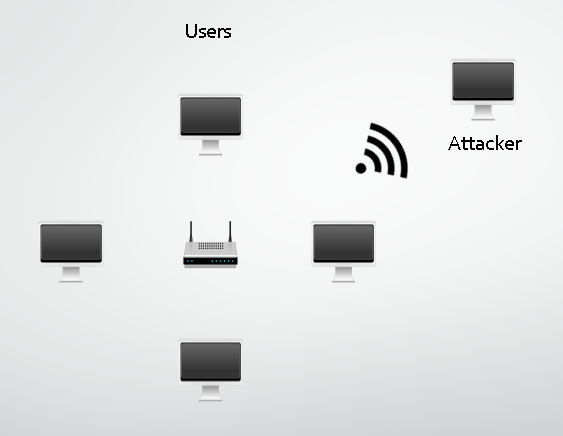
 When using a WiFi network you're broadcasting your network traffic through the air, literally shouting it out loud enough to ensure the access point hears you. Unfortunately, that also means that anyone else close by can hear your traffic too. Many diagrams, including mine above, typically visualise WiFi signals as being directed towards the access point, but in actual fact WiFi signals are omnidirectional.They are transmitted in every direction equally as loud.
When using a WiFi network you're broadcasting your network traffic through the air, literally shouting it out loud enough to ensure the access point hears you. Unfortunately, that also means that anyone else close by can hear your traffic too. Many diagrams, including mine above, typically visualise WiFi signals as being directed towards the access point, but in actual fact WiFi signals are omnidirectional.They are transmitted in every direction equally as loud.

This represents quite a considerable problem because you can't prevent your signals from breaching the physical boundaries of your property and becoming available to those outside. Consider living in a row of terraced houses or apartments where an attacker could easily be less than 30 feet from you at any time. This security concern was addressed with the creation of encryption protocols like WEP and WPA. Because the traffic between your WiFi device and the access point is encrypted, those on the outside can listen in but everything is encrypted and is thus useless to an attacker.
Open WiFi hotspots
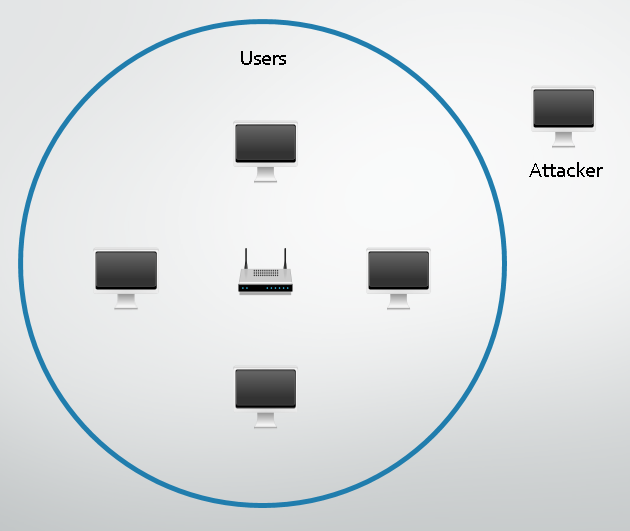
On open WiFi hotspots there is no password required, you simply select the network, connect and start browsing. These pose the highest level of risk to a user because your traffic is being sent through the air without any encryption whatsoever. Anyone within range can utilise tools freely available online to listen in to your network traffic and see exactly what it is that you're doing. Even if you are taken to a login page after joining the network, this will not protect you from eavesdropping, this is usually just to monitor and track access to the WiFi service. The only protection that you have is dependant upon the website to use Transport Layer Security (TLS) to encrypt your traffic. Even this isn't a foolproof option and an attacker still has the option of using SSL stripping attacks, to circumvent the security of browsing a site using https:// by connecting to the network.
Password protected WiFi hotspots
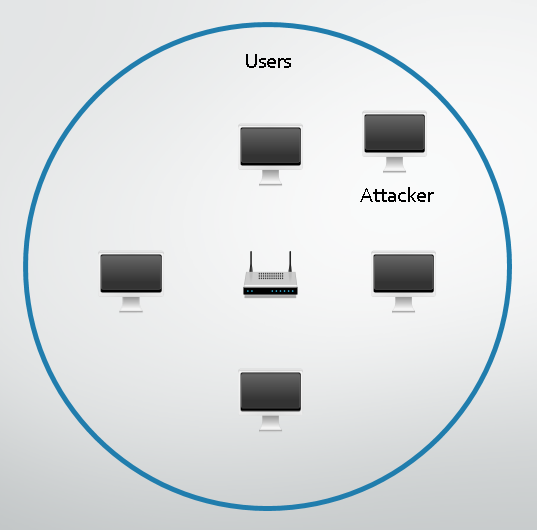
Even if the WiFi hotspot you're using has a password to connect to it, it still doesn't offer any real protection in a public scenario. Yes, the traffic between you and the access point is now encrypted but everyone is using the same password and encryption. If the password is on a poster at the end of the counter for everyone to see, there is nothing to stop an attacker having access to the password too. Once they have that they can gain access to your traffic and do anything that they could do as if it were an open WiFi hotspot. The password is a trust mechanism. You set up the security to protect yourself and your network and then only give out the password to those people you trust and want to have access. Unfortunately it's a common misconception that a network with a password is more secure than an open network, but if the password is public knowledge it doesn't change a thing.
How do I protect myself?
The easiest and best way to protect yourself when using any public WiFi hotspot is to use a Virtual Private Network (VPN). I wrote an article explaining what a VPN is for; they create a secure, encrypted tunnel through whatever network it is that you may be connected to. It does this by connecting your device to your VPN provider and encrypting all your traffic before it gets sent there. Your VPN provider then forwards all your traffic on to its intended destination. Likewise, traffic heading back to your device gets sent to your VPN provider first, who then encrypts it and sends it back to you. When using a VPN it doesn't matter what kind of WiFi hotspot you're connected to, password protected or not, nobody on the network will be able to access or view your traffic. As an additional layer of security you should always browse sites using https:// where possible. If the address bar does not display https:// you can always try typing it in manually to see if the site has a https:// option available. There are also plugins that you can get for your browser that will do this for you automatically.
Is it worth the trouble?
This really depends on how much you use public WiFi hotspots and what you do when you're on them. A good VPN service can cost as little as £2 ($4 USD) a month and you can use them 24/7/365 to protect your traffic. That's not just on public WiFi hotspots, you can use them all the time. If you're just browsing news sites or checking out cat videos on YouTube then you possibly don't need to use a VPN if you don't mind people snooping on what you're doing, but I'd still recommend it. As soon as you start logging in to services like email, Facebook, Twitter or anything that needs a username and password for that matter, it's definitely time to start using a VPN. Transmitting your user credentials across a network where you can't be assured of the trust of the owner, or know who might be lurking in dark corners nearby, isn't really a risk worth taking.
WiFi Survey
Wanting to look at some first hand data I created a survey using SurveyMonkey and collected 100 responses at random. I wanted to see for myself just what the level of WiFi hotspot usage is and how aware people are of the risks with using them. I've included the graphs of the results below and would like to thank everyone who took part.
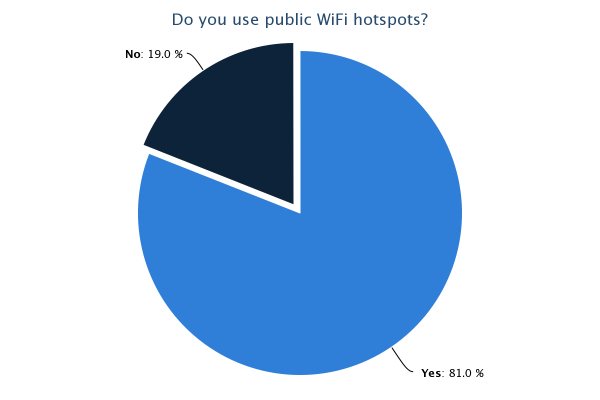
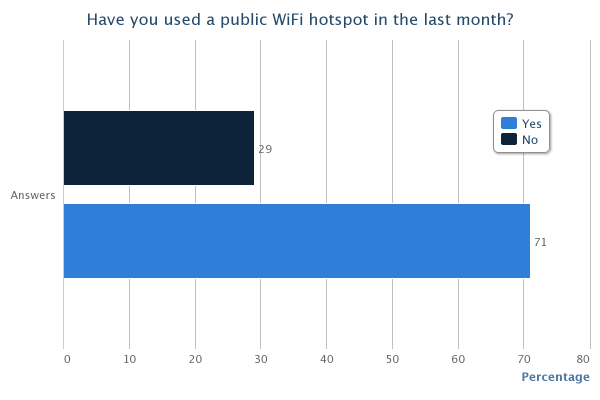
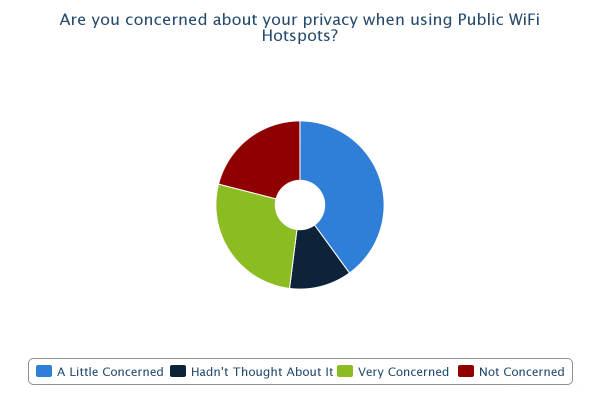
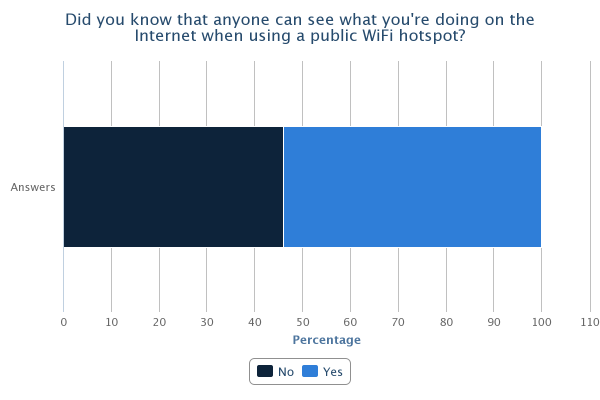
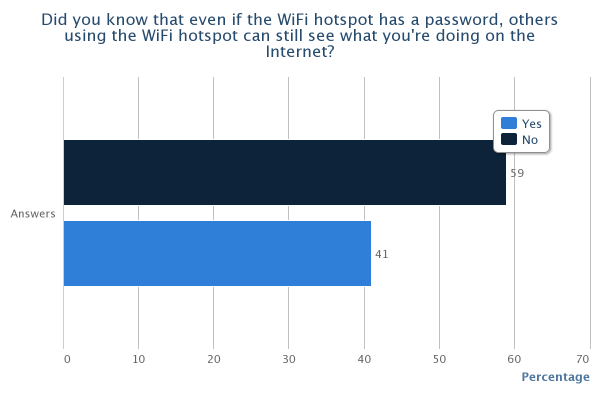
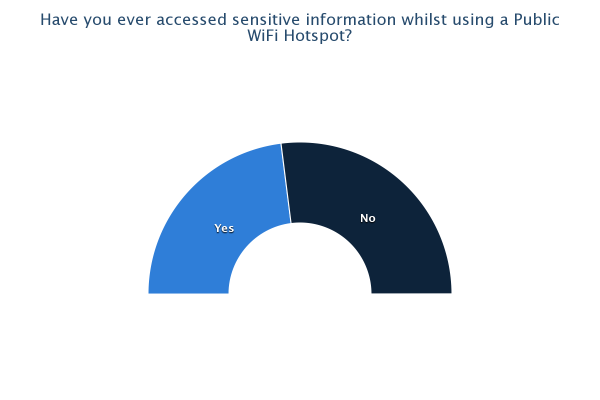
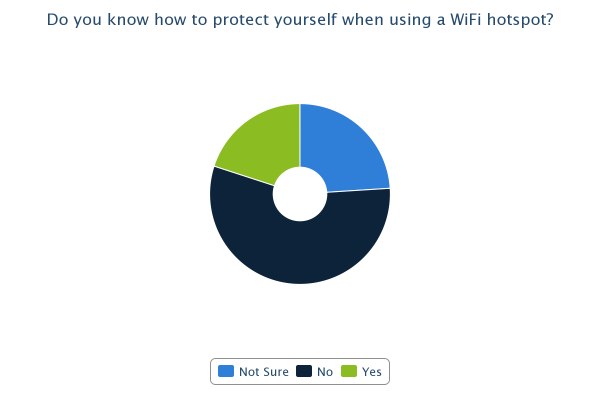
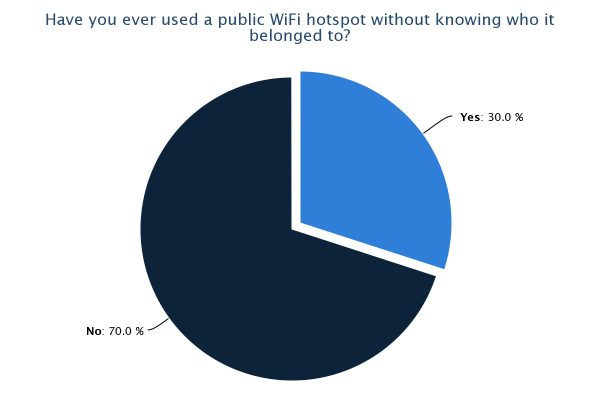

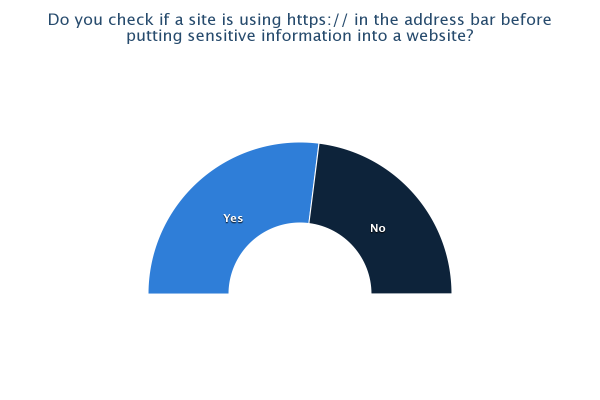
As can be seen from the results of the survey, there are some quite prominent trends that leap out, most of which are a cause for concern. 81% of us admit to using public WiFi hotspots with 71% having used one in the last month. Only 27% of those questioned were very concerned about the privacy of their data when using these hotspots with the remainder being only a little concerned (40%), not concerned (21%) or they hadn't even thought about it (12%). With it being so easy to access the data of other users on a WiFi hotspot, I think this highlights that a lot of users simply aren't aware of just how much risk there is. Only 54% knew that others could access your data when using a WiFi hotspot and this figure falls to 41% when the hotspot has a password. 13% believed that the hotspot having a password to access it would protect them from an attacker. Almost half of the respondents admit they have accessed private or sensitive data on a public WiFi hotspot yet 80% either didn't know or weren't sure how to protect themselves. Add to that the 48% of people who don't check a site is using https:// or don't know what it is and we're starting to paint a very worrying picture. It seems that the explosive growth in the proliferation and use of WiFi hotspots hasn't been matched by even the smallest growth in understanding of the risks involved with using them. It would seem that consumers of WiFi services need to be made aware of the risks, especially when you consider that, at some locations, users are paying a hefty premium for the privilege of using them. The situation is of course much worse when you start to think about accessing corporate data on the WiFi at your hotel... Many corporate IT departments provide VPN access to allow remote working for convenience and flexibility, a lot of times the security aspect of a VPN is completely overlooked. If you have access to a corporate VPN you should always use it when carrying out any work related business away from the office. An expensive hotel lobby or large conference would be a great place for a hacker to hang out and surf the WiFi to see what interesting emails or corporate secrets he could pick up. I'm sure your company wouldn't want their annual finances spreadsheet falling in to the wrong hands when it could have easily been prevented!
Conclusion
The conclusion is really quite simple. If you're using a WiFi network away from the home or office you should be using a VPN to protect sensitive traffic. They're cheap, easy to setup and could save you a nasty case of identity theft. Don't wait until the horse has bolted before you close the stable door. A lot of people have said that they only use public WiFi if they're reading the news or something non-sensitive and that it doesn't really matter. Whilst they're right in saying that they're not bothered about someone monitoring or intercepting the BBC headlines, it's what your device is doing in the background that's a concern. Most smartphones will regularly poll email and social media accounts in the background, presenting an attacker the opportunity to monitor or intercept credentials. If you're connected to the WiFi and a notification pops up about that email or social media message, it's already too late. The safest bet is to either not use public WiFi or take precautions like a VPN when using one.
