Let's Encrypt have announced that on July 8th, 2019 they will begin issuing new certificates from their own intermediate CA and not their current cross-signed intermediate. Here's what that means and what action, if any, site operators need to take.
Let's Encrypt
I've spoken extensively about Let's Encrypt on my blog and I'm a huge supporter of theirs. Not only do they give out free certificates, but their process can be easily automated, leading to a huge increase in adoption of HTTPS across the web. Today they made an announcement that they plan to make a change on July 8th, 2019. Here's what that change means and what you need to do about it.

Cross-signing
Like all new CAs, Let's Encrypt began life with a cross-signature. Cross-signing is a trick that CAs can use to avoid the years long process of becoming a root CA. It genuinely does take many years to go through this process and Let's Encrypt wouldn't have been able to issue any certificates over the last 3+ years without a cross-sign.
Cross-signing essentially makes you a CA by using the trust placed in another CA. I don't want to go too far into the technical details of that process here, instead I want to focus on what it means for site operators and the action they need to take, if any. If you'd really like the technical details, it might be worth attending "The Best TLS Training in the World", where the topics of cross-signing, subordinate CAs and much more are covered in great detail!
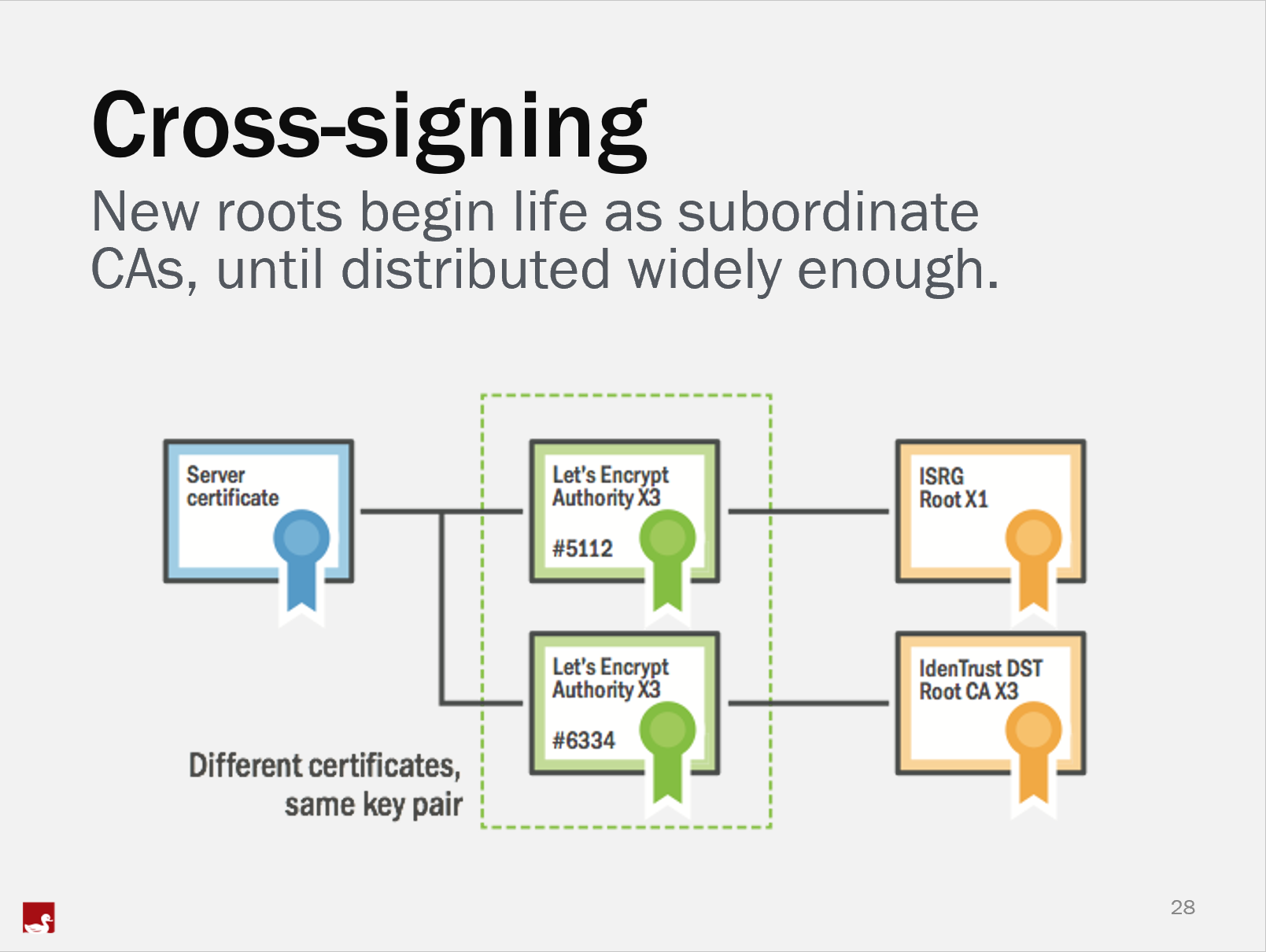
In short, Let's Encrypt currently issue from their cross-signed intermediate, which is issued to them by IdenTrust. IdenTrust have been a CA for many years and even old, legacy clients recognise them as a CA. When you get a certificate from Let's Encrypt right now it is issued by the cross-signed X3 intermediate which chains to the IdenTrust root. Now that Let's Encrypt's ISRG root is widely trusted, they can instead switch to issuing from their own X3 intermediate instead of the cross-signed one. This is a big step forwards for them and will likely not mean anything to the vast majority of their users. There are a few considerations though.
Legacy clients
Yep, we just can't get away from them! As the ISRG root has only recently been recognised by all of the major platforms, there is a small consideration for clients. Let's say that the ISRG root was recognised by Microsoft in Aug 2018. That means a Windows device would need to have done a Windows update since then to have been updated with that new information. If the device hasn't done a Windows update, then it can't know about this fancy, new ISRG root CA. This means that particular device would not recognise the certificates issued by the ISRG root as trusted. That's exactly the reason we have the cross-sign. By issuing from the cross-signed X3 intermediate, the client will recognise the IdenTrust root CA as trusted and thus recognise the intermediate and leaf certificate as trusted. The IdenTrust root was distributed many years ago and there is a good chance that the client has been updated in that time to know about it. Here lies the problem with the change of intermediate. Do your clients have the ISRG root in their trust store? That's the $1,000,000 question.
Let's Encrypt have setup a test site so you can see if a particular client can access it and know that they will be ok with your new certificates come July when the switch happens. This is the chain that is built by my install of Chrome on Windows, both fully updated.
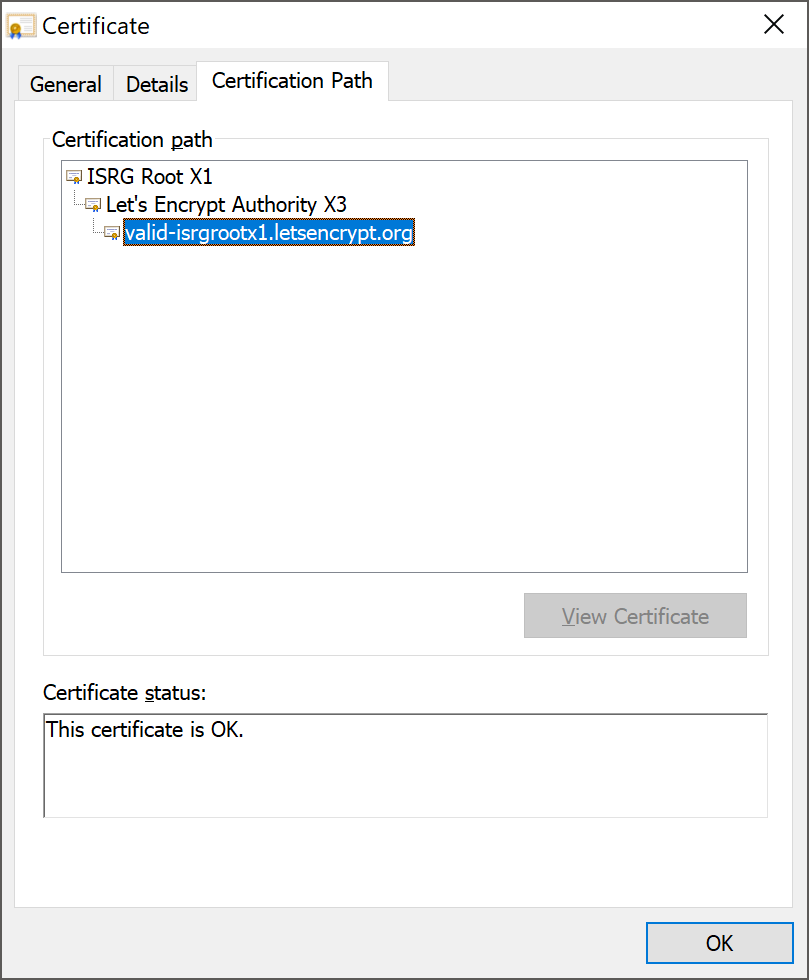
If my client didn't have the ISRG root in the trust store then this connection would fail as there was no trusted root to anchor the chain on. If you access this test site and your client doesn't work, you have a problem that you need to (and can) solve.
When Let's Encrypt switch to issuing from their own X3 intermediate, if you want to support legacy clients that don't have the ISRG root in their trust store, there is a simple fix for you. All you need to do is continue to serve the old, cross-signed intermediate in the TLS handshake instead of the new one provided via ACME. Because both of the X3 intermediates use the same key pair, either of the intermediates can be used to validate a chain, regardless of which of the intermediates actually issued the leaf certificate. Essentially what this means is that if you need your clients to keep building a chain down to the IdenTrust root instead of the ISRG root, you simply need to update your server to continue serving the old intermediate instead of the new one, and everything will work just fine (* for now, keep reading).
Sites that hard-coded the old intermediate
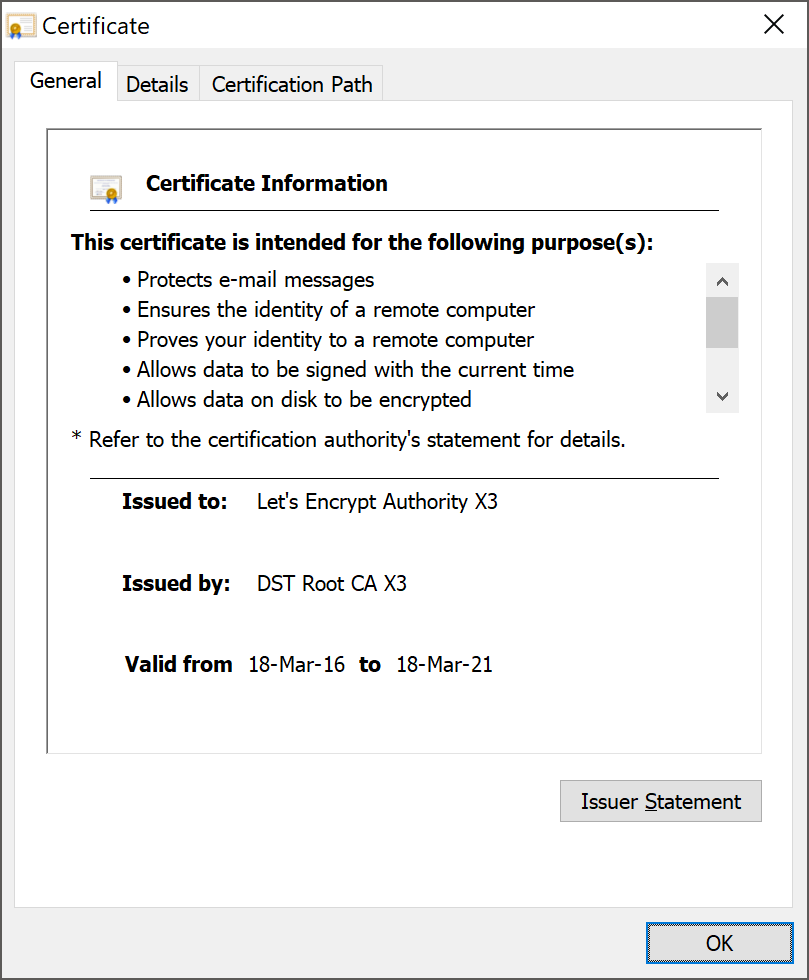
Tecnically speaking, the intermediate certificate is as dynamic as the leaf certificate. Every time you get a new leaf certificate you may need to use a new intermediate certificate. Now, 99.999999% of the time that's not the case and intermediates are very long lived certificates, but here we are at the 0.000001% of the time when they can, and do, change. On July 8th, 2019 your new Let's Encrypt certificate will be issued from the X3 intermediate that chains to the ISRG root, but your site/service might continue to serve the cross-signed X3 intermediate during the TLS handshake. It is possible for a change like this to break your certificate chain, and thus the connection to your site, but for the reasons mentioned above, it won't.
If you get a new certificate issued from the X3 intermediate that chains to the ISRG root, but you serve the old, cross-signed X3 intermediate in the TLS handshake, the connection will still work (* for now, keep reading). This is because both of the intermediates are using the same key pair and as I said above, a certificate issued from either of the X3 intermediates can be validated using either of the X3 intermediates. This is a nifty trick to prevent breakage and Let's Encrypt have likely done this exactly for this reason, to look after their users when this time came.
The cross-signed X3 is expiring
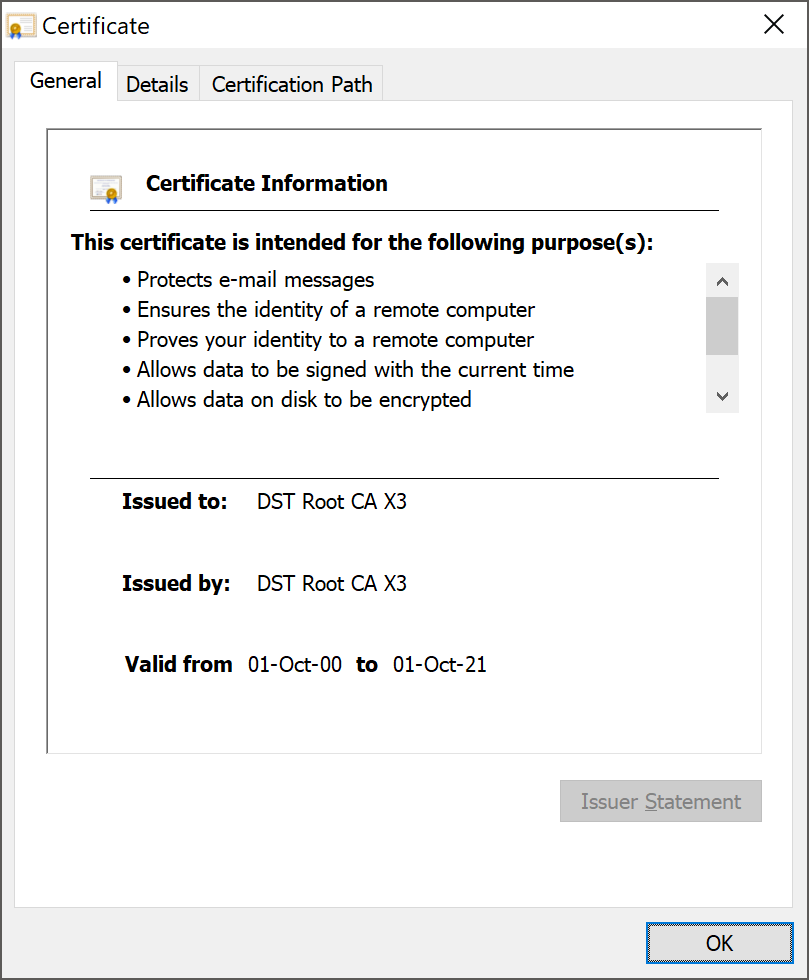
Certificates don't last forever and intermediates are no exception. The current, cross-signed X3 intermediate will expire on March 18th 2021 (or likely March 17th depending on time zone) and that means that's the last date at which you can use it.
If you're using this cross-signed intermediate for legacy client support, as I mentioned above, then you need to have a plan in place to take action before this date. Let's Encrypt are trying to help you out and they are obtaining a new intermediate that will be valid until September 29th 2021, giving you an extra few months. All you'd need to do is obtain a copy of this new cross-signed intermediate and serve that in your TLS handshake with legacy clients instead of the current one. There is a valid reason they can only buy you a few extra moths of support though...
The IdenTrust root is expiring
The current cross-signed X3, and the new cross-signed X3, simply can't be valid past September 30th, 2021 as that's when the IdenTrust root certificate expires.
This is the final date by which everyone must have moved over to using a certificate chain that chains to the ISRG root certificate if you're going to continue to use Let's Encrypt certificates. The old cross-signed X3 and the new cross-signed X3 will have both expired by then and the chain is definitely useless once the root has expired. If you still have legacy client concerns by September 30th, 2021, these clients won't have been updated for over 4.5 years and you will need to convince them to update if they want to continue to be able to access your site/service.
A CA problem, not a Let's Encrypt problem
All certificates expire. All CAs start out life as a subordinate. None of the issues here are specific to Let's Encrypt, it's simply their turn to go through the process. All existing CAs will have either gone through this process or will have to go through this process at some point in the future. I just want to clarify that this action isn't necessary because you chose to use Let's Encrypt, it's necessary because of how CAs and the PKI ecosystem work. If you hang around long enough, you'll have to go through this process eventually no matter which CA you use.
Useful links and information
Let's Encrypt transition announcement: https://letsencrypt.org/2019/04/15/transitioning-to-isrg-root.html
Let's Encrypt ISRG root coverage: https://letsencrypt.org/2018/08/06/trusted-by-all-major-root-programs.html
The Best TLS Training in the World: https://www.feistyduck.com/training/the-best-ssl-and-tls-training-in-the-world
