Those that know me or have followed me online will know I'm a massive advocate of encryption on the web. One of my goals is to help encrypt as much of the web as I can by sharing knowledge and information, building tools and services, speaking at conferences and countless other things. I see this blog post as part of that mission.
The rise of encryption
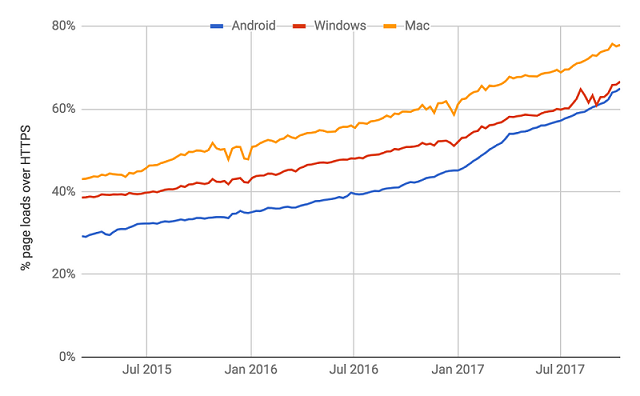
Right now we're seeing encryption adopted across the web faster than at any point in history, we are making truly amazing progress. Every 6 months I publish a report on the top 1 million sites on the web and in the latest edition from Feb 2018 you can see the amazing progress being made.
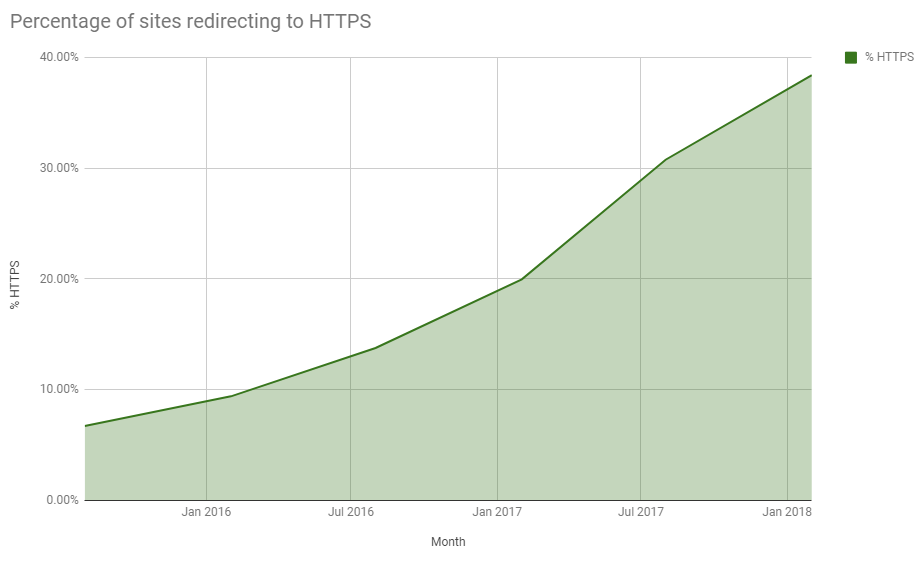
It's not just me making these claims though, we're seeing this trend confirmed by people and companies across the industry.
.@Mozilla telemetry shows more than 50% of page loads were HTTPS yesterday. First time that has ever happened. pic.twitter.com/FE0FcIGPju
— Josh Aas (@0xjosh) October 14, 2016
Even Google have come out and published data about their Chrome browser.
The point is that encryption is here to stay and we are well on our way to a world where encryption will eventually become the default and not the exception.
CAs play a vital role
A Certificate Authority issues you a certificate to install on your website. The certificate serves one vital role in the whole process and that is authentication. If you type scotthelme.co.uk into the address bar and hit enter, when the page loads you can be sure that you have loaded the page from scotthelme.co.uk and that no one is trying to impersonate me. The browser validates the certificate it receives to make sure it's a genuine certificate and not a forged one, that it was issued by a trusted CA and that the document was issued to scotthelme.co.uk. This is the very first step the browser performs when setting up the secure connection and if this fails, nothing further is allowed to happen. That, however, is all that the certificate does. Once the browser has done those few checks right at the start of the connection, the certificate can be tossed away, it serves no further purpose.
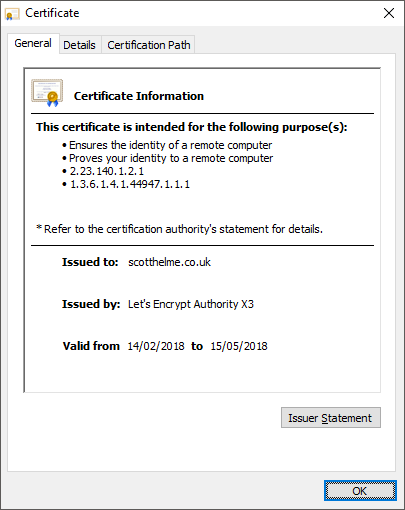
The difference between free and expensive certificates
For the purpose of this blog post I'm going to be talking specifically about Domain Validation, or DV, certificates. I've spoken about Extended Validation certificates and hopefully made my views on those clear in my blog post Are EV certificates worth the paper they're written on? so check that out if you're interested. There's an interesting battle going on with DV certs right now and that's largely due to Let's Encrypt. CAs used to sell DV certificates for a healthy amount of money but over the years the cost was a race to the bottom, until Let's Encrypt came along and started issuing them for free almost 2 years ago. Let's Encrypt have faced a lot of scrutiny and even hostility from the wider community, I guess that was to be expected if you kill someone's business model, but I don't want to look at or focus on any of that. I'm going to be talking purely about provable, technical facts on the differences between free certificates and certificates that you pay for.
All certificates issued by a CA must be issued in accordance with a document called the Baseline Requirements set out by the CA/Browser Forum. This document details everything that a CA must do to validate the owner of the domain, how long certificates can be valid for and countless other restrictions that any CA must adhere to during issuance. Conformance is not optional and there is absolutely no mention of or difference between certificates that are issued for a fee or certificates that are issued for free. All publicly trusted certificates must meet the requirements, period.
Outside of the industry requirements set out by the CA/Browser Forum, which control the process and policies around certificate issuance, we also have to consider the standards too. All X.509 certificates must be issued in accordance with the specification, otherwise they're simply not going to work! The appropriate RFC is RFC 5280 which provides the X.509v3 Certificate Profile that all issued certificates must conform to. Again, there is no mention of whether or not a certificate was issued for a fee or for free, all certificates must conform to the standard.
Better Encryption
Another really common thing that I see mentioned is that certificates somehow have an impact on the encryption of data transmitted over a connection. Let me clear this up and be as absolutely crystal clear as I can be; Certificates have nothing to do with the encryption of data you transmit. Looking around at a few CA websites though, you'd be forgiven for thinking that they somehow do, here's just a selection.
The encryption of data is handled by server configuration and not the certificate. Let's take a look at a few cipher suites to prove the point though. Let's say we have a 2048 bit RSA key and we obtain a certificate, you're going to see a cipher suite that looks something like this in production.
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
Let's quickly break this down so we understand each of the components.
- TLS - The protocol being used.
- ECHDE - The Elliptic Curve Diffie-Hellman Ephemeral key exchange, supports Forward Secrecy.
- RSA - The key used for authentication, in this case our 2,048 bit RSA key.
- AES - Advanced Encryption Standard, the symmetric encryption algorithm used for encrypting data.
- 128 - The symmetric key size.
- GCM - Galois/Counter Mode, we're using authenticated encryption (AEAD).
- SHA256 - The Message Authentication Code used for integrity checking.
Looking at that list, the only component that a certificate has any bearing on is the key used for authentication. In the example above we're using a 2,048 bit RSA key but we don't even list the size of the key in the cipher suite, just the key algorithm. The particular cipher suite above is using AES with a 128 bit key but if we wanted to increase that to AES with a 256 bit key, we'd simply change our configuration to use a different suite.
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA256
Now we're using 256 bit encryption and we didn't change anything to do with the certificate, we could still be using exactly the same certificate. In fact, different clients may negotiate either one of these two cipher suites depending on their capabilities. We can even change our authentication key and get an ECDSA certificate, but they're still nothing to do with the encryption, we just update the cipher suites again.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA256
Talking about the strength of encryption you can use when purchasing or obtaining a certificate is a bit like talking about whether or not your site can have responsive design when purchasing or obtaining a certificate. It has nothing to do with the CA or the certificate and is entirely down to the site to configure and control.
Commercial CAs also do free certificates
This one is a bit of an interesting twist, what do we do when a "commercial CA" offers free certificates? Is their free offering somehow worse than their paid certificates or are free certificates from a commercial CA somehow better because they're a commercial CA? Probably the biggest and most widely known source of free certificates is Let's Encrypt, and I've talked about them extensively on my blog. They aren't the only CA to give out free certificates though, and they actually weren't the first either.
StartCom was issuing free DV certificates long before Let's Encrypt existed but they have recently ceased operating as a CA and can't be used any more. Looking at the more 'commercial' CAs though, Comodo offer free 90 certificates just like Let's Encrypt do.
One of the other really interesting points from that Comodo image is that not only are free certs and paid certs exactly the same, as shown above, and not only do they have no impact in the encryption of data, Comodo issue them both from the same infrastructure. The free certificates and the paid certificates both chain down to the same root certificate meaning there is, quite literally, absolutely no difference between them except how long they're valid for. After Comodo we have AlwaysOnSSL who are another free and automated CA and there are offerings from major CDNs like Cloudflare to consider too. When you sign up for Cloudflare and have them proxy your traffic they issue a certificate to do that securely through their Universal SSL program.

Given that Cloudflare are perhaps one of the largest CDN providers in the world, proxying traffic for some pretty substantial websites, there is little objection to them giving away free certificates. I also can't find any mention of a warranty or insurance for the certificates that Cloudflare issue and use either.
Free CAs don't try to restrict you
You'd think having paid for your new certificate that you'd be able to do whatever you like with it, right? Maybe you only have 2 servers now but as you grow you might need 3 or even 30 servers! That's ok, we have a certificate and it will work on multiple servers, so we're good. Maybe not...

Yep, that's right, your certificate isn't really your certificate I guess, you're not allowed to use it on more than 1 server unless you pay for that privilege. Not only is there no technical reason for this, it could actually be quite hard in a cloud environment with elastic scale to even keep track of this, or, in a serverless environment, even determine what a 'physical server' is. Whilst Symantec and other 'commercial' CAs seem to have such limitations, Let's Encrypt do not. Hopefully we will see the last few cases of restrictions die off as organisations realise how futile they are.
Warranties and Insurance
Yes, some certificates really do come with warranties and no, they really aren't that useful. You should read my other post that covered warranties: Do SSL warranties protect you? As much as rocks keep tigers away...
Who says free certificates are bad anyway?
This is almost a rhetorical question but I'm going to answer it anyway. When searching around on Google for information on whether or not I should use a free certificate, there's a lot of information on why I shouldn't use one. Interestingly, yet unsurprisingly, all of this information seems to come from CAs themselves or resellers, those that stand to make money by selling you certificates. The accuracy of the information ranges from 'a bit of a stretch' right through to 'complete bullshit' and the answer to all of the problems is, of course, buy one of the certificates that we will sell you.
Let's take Volusion and their blog on 5 Reasons You Should Beware of Free SSL Certificates.
- They set off browsers' security alarms
- They make websites look fraudulent
- They weren't meant for ecommerce
- They have more points where they could be compromised
- They can hurt your customer trust
Of course, the answer to all of these problems is...
Same from Combell in their blog on Should you go for a free Let’s Encrypt certificate or a premium SSL certificate?, one of the main headings on the page:
Let’s Encrypt or an established Certificate Authority?
I'm not sure how Let's Encrypt are any more or less established than any other CA, but the language here is designed to imply that they aren't, and of course if you want to buy a certificate from an established CA, further down the same page:
Namecheap are a pretty big domain registrar and they also have services for SSL certificates. Their blog post Why paid certificates are better? is a little more direct in the title but again, it's the same story.
What do they sell?
Then we have SSL Dragon who take things a little further in Free vs. Paid SSL Certificates.

They state the following:
Unsuitable for e-commerce
May hurt your customers’ trust
Tardy customer support
I think you're starting to see the trend here, what do they sell?
I can see how and why this happened of course, free certificates are cutting into their profits because customers can get things for free that they used to buy from these companies. Those companies now need to convince users to continue paying them for certificates instead of using free ones. Let me be clear, I'm not saying free certificates are perfect for everyone, and maybe you do want to use paid certificates for whatever reason, but you should always be careful when trying to make the decision. The main point that I want to make here is not what's being said, but rather who's saying it. Of course a CA or reseller will tell you that paid certificates are the answer to [insert problem], just verify what they're saying from other sources, other sources that don't have a vested financial interest in telling you what they're telling you.
Certificates have binary state
When you look at a certificate the only thing we really care about is whether or not the browser is going to accept it, we care if the certificate is valid. To be valid there are various technical criteria outlined above regarding it's format, the fields it contains and the data inside them that must be met. There's also criteria around how it was issued that the CA must adhere to and all of this plays a part in the ultimate determination made by the browser about the certificate itself. Whether or not anyone handed over some hard-earned cash to purchase the certificate simply does not matter one bit. The browser doesn't even have knowledge of whether that happened and there'd be no way and no need for it to do so. There's absolutely no difference between a free certificate and one that you had to shell out some cash for.