It's been common knowledge in the wider PKI community that Symantec, the Certificate Authority, is currently being distrusted and will soon cease to exist as a CA. My worry is that the wider community doesn't seem fully prepared for the distrust and the impact it will have.

Symantec
There's a whole, big (really big) back story to Symantec being distrusted by the browsers but it can be distilled down to the fact that they did some things that made the browsers lose faith in them, they issued certificates that they shouldn't have issued. You can read Chrome’s Plan to Distrust Symantec Certificates and the long thread on Mozilla's Dev Security Policy mailing list about exactly why, but one way or another Symantec will cease to exist as a CA. Despite sanctions like Google requiring Certificate Transparency compliance from Symantec ahead of the requirement for all other CAs, it seems there was no coming back and Symantec sold off it's entire CA business to DigiCert and will exit the market. This is a problem for site operators because they now need to find a new CA, which will hopefully be a lot easier now they can transition to DigiCert, but the bigger issue is that if you're using an existing Symantec certificate you need to replace it, and this is where things get interesting.
The deadlines
There are 2 deadlines by which sites need to take action and they depend on when you got your Symantec certificate. If the certificate was issued prior to 1st June 2016 it will stop working with the Chrome 66 release in April 2018 and if you have any other Symantec certificate it will stop working with the Chrome 70 release in October 2018. Prompted by other research I'd seen online I thought I'd put my crawler data to good use and see what further analysis I could do with it.
Who is still using Symantec certs
After creating a script to go through the certificates collected by my crawlers I can parse them all and see who is still using a Symantec cert that will be distrusted. I've broken the list down into 2 separate files; the sites using certificates that will be distrusted in m70 and the sites who will have their certificate distrusted in m66 who need to take more immediate action. You can see the code over on my GitHub repo and the two files that contain the lists of sites are m66.csv and m70.csv respectively.
The M66 distrust
I'm currently seeing 1,321 sites in the Alexa Top 1 Million that will have their current certificate distrusted in April. That's a pretty large number and with less than 2 months to go, I hope they're already underway with replacing the certs.
The M70 distrust
For M70 the numbers are slightly higher, as you'd expect, and I'm seeing 6,882 sites that will have their certificates stop working in September. That's a much more acceptable timeframe and I will track the numbers as we go.
A basic db query
The above numbers were acquired by parsing the certificates that were collected and looking for ones that chain to a blacklisted Symantec root. Another much more simple approach is to look for instances of 'Symantec' in the name of the CA.
SELECT ca, count(ca) FROM `results` WHERE ca LIKE '%Symantec%' GROUP BY ca ORDER BY count(ca) DESC
That gives me the following list.
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 Secure Server CA - G4
3884
C = US, O = Symantec Corporation, OU = Symantec Trust Network, OU = Domain Validated SSL, CN = Symantec Basic DV SSL CA - G2
2764
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 EV SSL CA - G3
2703
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 ECC 256 bit SSL CA - G2
499
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 Secure Server SHA256 SSL CA
401
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 Extended Validation SHA256 SSL CA
310
C = US, O = Symantec Corporation, OU = Symantec Trust Network, OU = Domain Validated SSL, CN = Symantec Basic DV SSL CA - G1
192
C = CN, O = "TrustAsia Technologies, Inc.", OU = Symantec Trust Network, OU = Domain Validated SSL, CN = TrustAsia DV SSL CA - G5
186
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 ECC 256 bit EV CA - G2
123
C = US, O = Wells Fargo, OU = Symantec Trust Network, CN = Wells Fargo Certificate Authority WS1
11
C = US, O = Oracle Corporation, OU = Symantec Trust Network, CN = Oracle SSL CA - G2
2
C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 EV SSL CA - G2
1
One way or another, that's still an awful lot of Symantec issued certs...
Check the lists
It'd be worth taking a look through the lists and seeing if your site is on there and if it is, make plans to remove it! As the script can be run against my daily crawl data it will be easy to keep this up to date and to monitor it as we get closer. Perhaps in the last week or two it might be worth reaching out to organisations publicly to see if they're aware of the impending change. To confirm if a site is affected you can visit it in the latest version of Chrome and check the console for an error message:
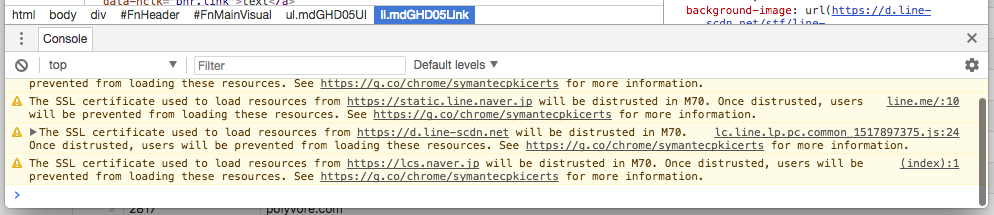
The other great thing to note from that example is that my scans only hit the apex domain on http and follow redirects to completion, meaning there will be many more sites that have a Symantec cert that will be affected but don't currently redirect to it. I also won't pick up resources on the page loaded from subdomains or other 3rd party domains that are impacted by this distrust. I guess the point is that this is only the tip of the iceberg and there are a lot more sites out there that will be affected.
