I recently upgraded my PC with a fingerprint reader and Windows Hello to make the login experience much more convenient, but there was another little thing I needed to address. At a few years of age my PC didn't have a TPM but I wanted to use BitLocker drive encryption properly, so it was time for a little hardware upgrade.
What is a TPM?
A TPM, a Trusted Platform Module, a little hardware device that's usually embedded into most modern PCs on the motherboard. The TPM is designed to be a tamper-resistant store for cryptographic keys and in the context of this article, I will be talking about using it in conjunction with BitLocker drive encryption. If you want to encrypt the storage drive in your PC, and you really should, then BitLocker is certainly one of the most convenient and relatively secure ways to do that. If you drive is stolen or cloned the encryption will prevent an attacker from being able to read data from the drive, which is great. The problem is that encryption needs keys and keys need to be securely stored and protected, or the encryption is worthless. This is where the TPM comes in.
As well as being a store for encryption keys, the TPM can also observe the state of your device and detect changes to it. There are several scenarios during which the data on your device may be at risk and we can have a good level of protection in all of them using a TPM and BitLocker. Let's say someone was to clone your drive or even steal the physical drive itself and then connect it to another device to read. They wouldn't be able to do anything because the drive is encrypted and the key to decrypt it is safely stored on the TPM of your PC that they left behind. Bad luck for the attacker. The only choice this leaves them is to perform their attack "in-situ" with the drive still installed inside the machine it belongs to. This means they need to be physically present at the device or steal the entire device itself, neither of which are impossible. Trying to boot from any kind of USB media would be detected by the TPM as a change in the system which would in turn cause it to refuse to decrypt the drive, again, no luck for the attacker. The only real option this leaves the attacker with is to boot the device "as-is" and try to break the password for the Windows account to login and gain access to the file system that way. Stealing the drive or cloning it won't help, you can't boot off alternate media to read the contents of the drive and if you boot it without tampering with it then you have a (hopefully) strong Windows password to contend with. That's an awful lot of protection to get from something that is transparent to the user after being setup and requires no maintenance or user interaction. This is a win all around.
My PC doesn't have a TPM...
I should have seen that one coming... My main PC at home consists of an Asus Z170-A motherboard and an Intel Core i5 6600K CPU, the two components where you might expect to find a TPM but I currently don't. Both a little dated but at the same time, perfectly modern and functional devices. With the introduction of insanely fast SSDs and my ability to throw crazy amounts of RAM at this thing, it's still more than fast enough for any of my needs. The CPU is also running a small but worthwhile overclock thanks to the water cooling it has installed so it really doesn't need upgrading right now. I do still want a TPM though...


I was in luck though because my motherboard does have a header where you can install a TPM. Flicking through the manual I came across this.
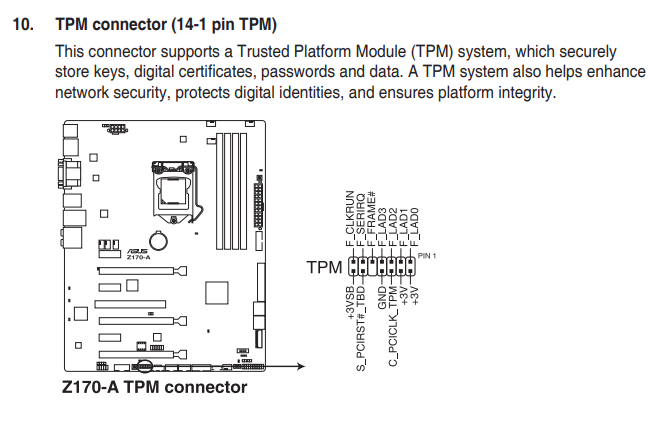
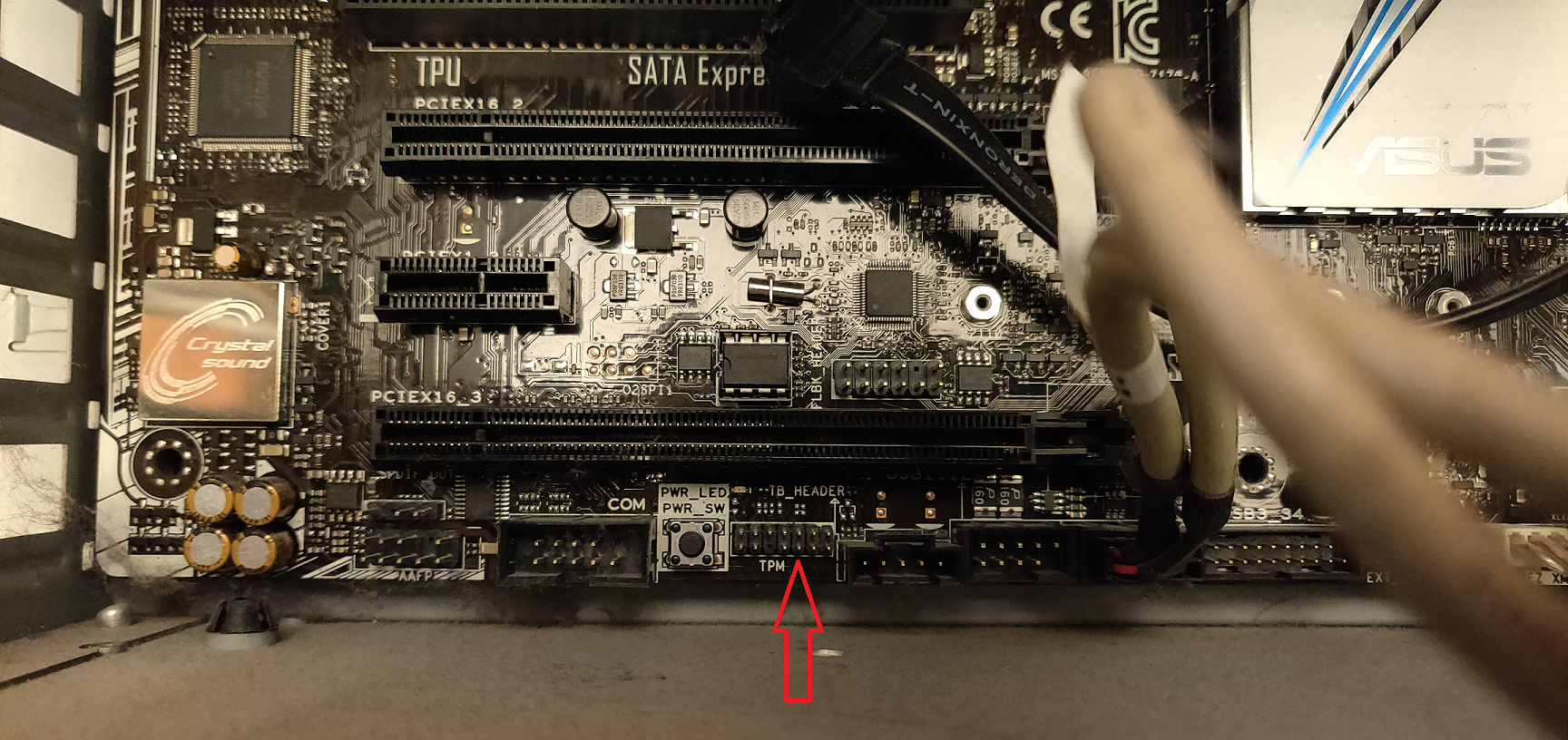
I flipped open my case and after cleaning out most of the insane amounts of dust I found (seriously what's with that?) there was indeed a header at the bottom of the board labelled "TPM".
Ordering a TPM
In theory this should be really easy. Order a TPM, install the TPM, setup BitLocker. Let's give this a whirl and see where we end up and what the process is actually like.
First of all I had to find somewhere that sold these things and various Google searches kept bringing me back to Amazon which was kind of handy and also a little surprising. I was also pleasantly surprised at how cheap the TPM was at only £8.92 ($11.72 USD)!
I got it ordered and the device was delivered within a couple of days, so far, so good. It came in an anti-static bag and was rather small, probably around the same size as a standard YubiKey. Here it is.
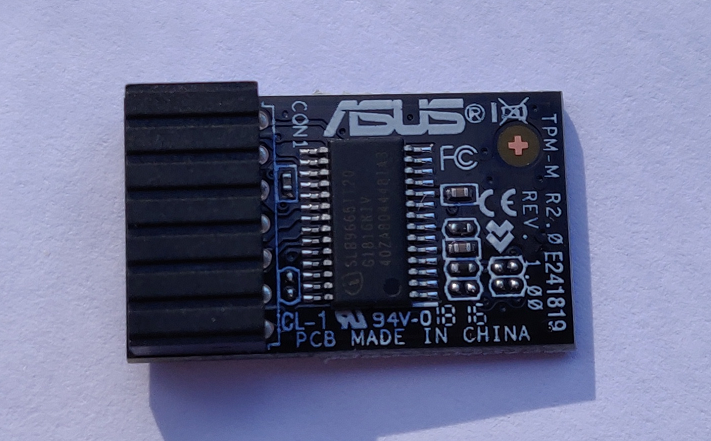
I opened up the case on my PC and simply pushed the TPM on to the TPM header on my motherboard. Like most devices it will only fit one way as there is a blanked out pin on the connector so installation was a breeze. Case closed up and it was time to boot up and see if everything was working.
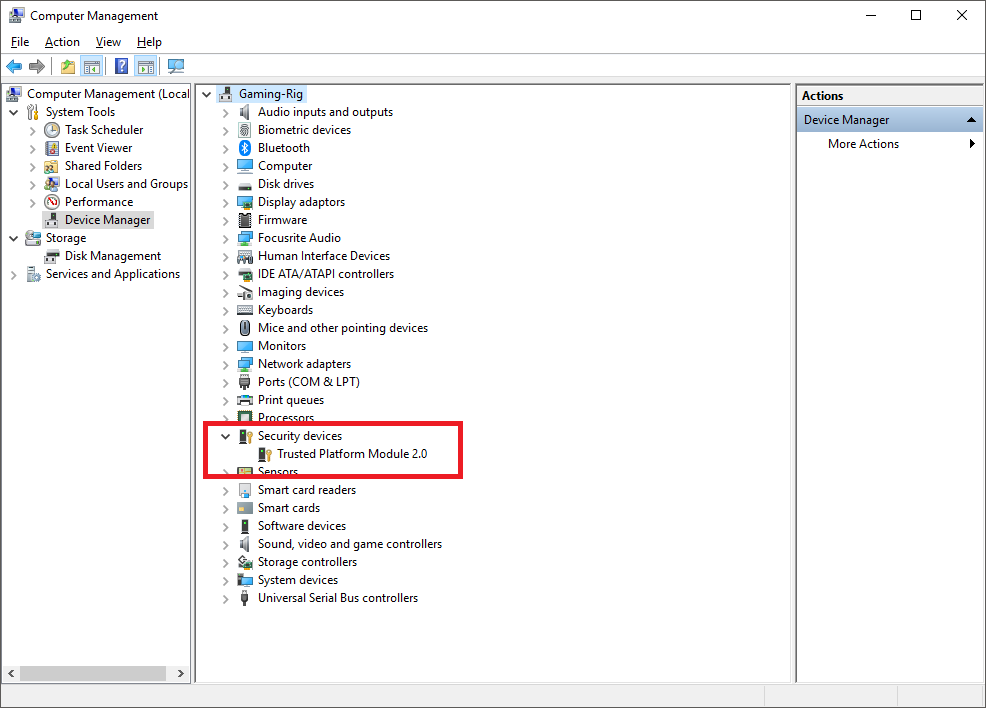
It looks like Windows is now detecting the TPM so it's time to move on to the next step.
Setting up BitLocker
I had previously wanted to setup BitLocker on my PC but without the TPM being present I had to set it up with a USB drive to act as the storage instead. This is basically a USB drive that's required to be present for the PC to boot as it contains the key to decrypt the drive. If you use this setup and just leave the USB drive with the device the whole time, including whilst unattended, it does present a less secure solution. An attacker could take a copy of the USB drive along with a copy of your main drive which results in them getting the encryption key and the encrypted data, something not possible with the TPM, or of course just take the USB drive itself with a copy of your main drive. The USB method doesn't have the same anti-tamper characteristics of the TPM in that it can't later detect a change in the environment and refuse to decrypt the data. The better way of doing this is with a TPM and I now have one at my disposal so it's time to switch to using that.
Before starting things off with the TPM I disabled BitLocker on my main drive and with a blazing fast SSD, this isn't something that takes long at all. Once the main drive was decrypted I could remove the USB drive being used for BitLocker and destroy the key on there. Now to setup BitLocker properly which is a painless and fast process too.
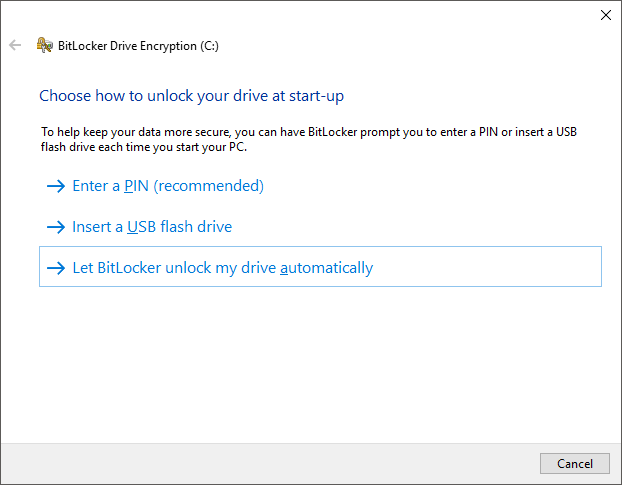
With that, everything is done! Someone could take a copy of my drive and not be able to decrypt it, they could take the drive itself and still not be able to decrypt it so all they can do is boot the PC as it stands to have it decrypted and then attack my Windows account password to try and get at my data. Is it a completely secure and fool proof system? No, of course it's not, no such thing exists! It is however astronomically better than having no drive encryption and better than other ways of implementing BitLocker without a TPM too. Fortunately for me, my laptop already had a TPM built into the hardware and given I travel with that device it's probably more at risk from data loss due to that portable nature. All I had to do when I enabled BitLocker on that was the last few steps of this article to simply turn it on. With that the only questions I have left are do you have BitLocker enabled and if not, why not?
