For those that read my blog often you may have seen me talk about EV certificates before. From a technical perspective there are many things that I don't agree with about EV certificates and from a non-technical perspective there are many things I don't like about the way they're advertised and sold. There is however another problem, and it's what happens when your CA turns against you.
Extended Validation
Extended Validation, or 'EV', certificates give you a little piece of green lipstick in the browser when you visit a website. You can see an EV certificate in action on the PayPal site here:
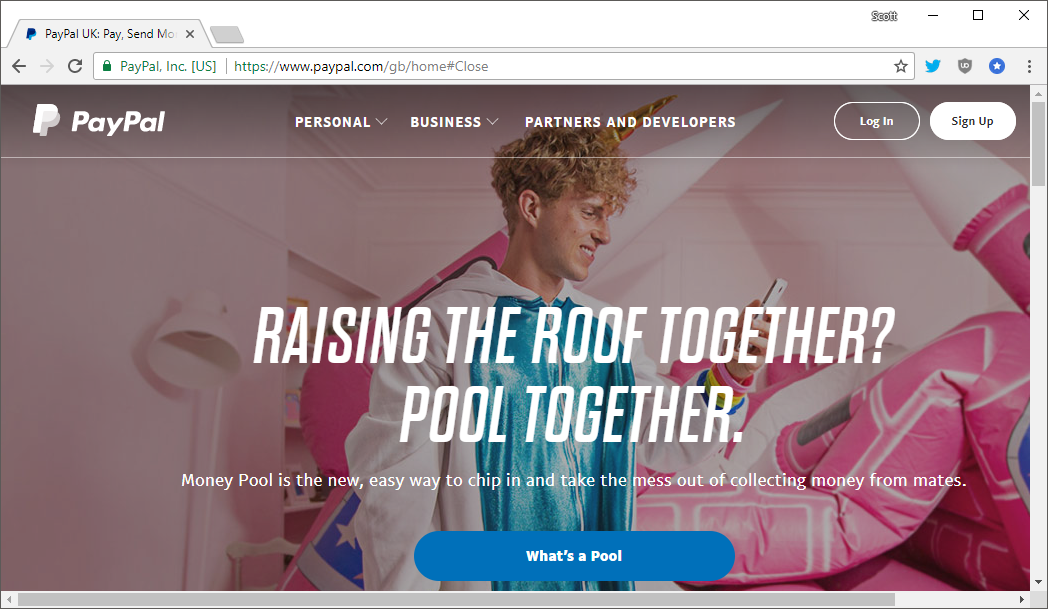
The "PayPal, Inc. [US]" string to the left of the address is what EV gives you (most of the time) and that's it. If you want more details on the problems with EV you can read my blog Are EV certificates worth the paper they're written on? but in this article I want to focus on what happens with your certificate after it's issued.
Clearing up what EV 'is'
Before we start on the issue here, I think it's important to clarify exactly what an EV certificate 'is' and does. The best and only place to get this information is from the CA/Browser Forum, the governing body of Certificate Authorities if you will. They set out the Baseline Requirements which is the rule book by which all CAs must play and for EV certificates there are the additional EV SSL Certificate Guidelines too. The EV SSL Guidelines are where we need to focus our efforts today and at the time of writing v1.6.8 is current. Section 2 of the guidelines set out the purpose of EV certificates in general and section 2.1.1 gives us the following:
2.1.1. Primary Purposes
The primary purposes of an EV Certificate are to:
(1) Identify the legal entity that controls a Web site: Provide a reasonable assurance to the user of an Internet browser
that the Web site the user is accessing is controlled by a specific legal entity identified in the EV Certificate by name,
address of Place of Business, Jurisdiction of Incorporation or Registration and Registration Number or other
disambiguating information; and
(2) Enable encrypted communications with a Web site: Facilitate the exchange of encryption keys in order to enable
the encrypted communication of information over the Internet between the user of an Internet browser and a Web site
So, an EV certificate lets us know that a legally registered company applied for and obtained the certificate, and thus controls the site/domain, and to enable encrypted comms to that site, just like any other certificate would. Section 2.1.2 goes on to add some secondary purposes for EV certificates:
(1) Make it more difficult to mount phishing and other online identity fraud attacks using Certificates;
(2) Assist companies that may be the target of phishing attacks or online identity fraud by providing them with a tool to
better identify themselves to users; and
(3) Assist law enforcement organizations in their investigations of phishing and other online identity fraud, including
where appropriate, contacting, investigating, or taking legal action against the Subject.
The first point here is due to the cost and process involved in obtaining EV certificates but I think that's a really dangerous assertion to make and we should have already learned from this mistake. For years, decades even, we put too much faith in the DV indicator of a padlock because they were expensive and hard to get, and look where that left us. To make the same mistake again with EV would be foolish. The second point is the problem of relying on users to identify and behave according to the EV indicator and the third point is a bit of a stretch in my opinion but would hold true. Moving on to the next section, 2.1.3, we have the excluded purposes of EV certificates, things that they are not to be used for:
2.1.3. Excluded Purposes
EV Certificates focus only on the identity of the Subject named in the Certificate, and not on the behavior of the Subject.
As such, an EV Certificate is not intended to provide any assurances, or otherwise represent or warrant:
(1) That the Subject named in the EV Certificate is actively engaged in doing business;
(2) That the Subject named in the EV Certificate complies with applicable laws;
(3) That the Subject named in the EV Certificate is trustworthy, honest, or reputable in its business dealings; or
(4) That it is “safe” to do business with the Subject named in the EV Certificate.
Looking at point 1 you can easily agree with that, having an EV cert doesn't mean we're actively conducting business, but after this, things get interesting. Point 2 basically translates to 'EV certs don't mean a site is good' and points 3 and 4 also translate to exactly the same thing. A site with an EV cert can rip you off, steal your information, phish you and do all kinds of other nasty things. The point I want to make here is that EV certs offer assurance of nothing other than the fact that somewhere there is a legally registered company with the name shown in the EV indicator. That's it. It's really important that we understand the purpose and limitations of EV certificates if we're to understand the following problems.
Demonstrating weaknesses in EV
EV certificates rely absolutely and completely on the user for them to have any effectiveness. If the user doesn't know what the indicator is or means, they don't look for and verify the indicator or don't check for its presence on every page load, the EV certificate provided no value. My biggest problem with EV is this dependency on the user, I don't think it's fair to expect the user to participate in our security, but that aside, the user is unreliable.
In recent weeks I've been following and supporting Ian Carroll with some of his research to demonstrate problems with EV. He registered a company in the US called Stripe Inc. and applied for an EV certificate for his company. He meets the EV criteria in that he owns a legally registered company and controls the domain he was applying for a certificate for, and a certificate was issued to him. You can see his site here stripe.ian.sh but it doesn't currently have an EV certificate, which we'll talk about shortly:
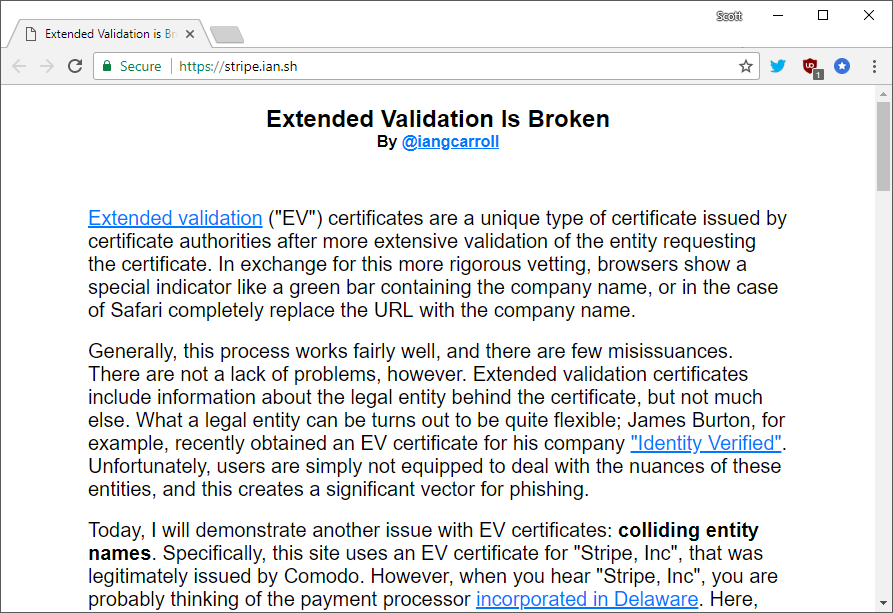
Of course, he is demonstrating that his EV certificate looks very similar to the Stripe Inc. you're probably thinking of, the payment processor.
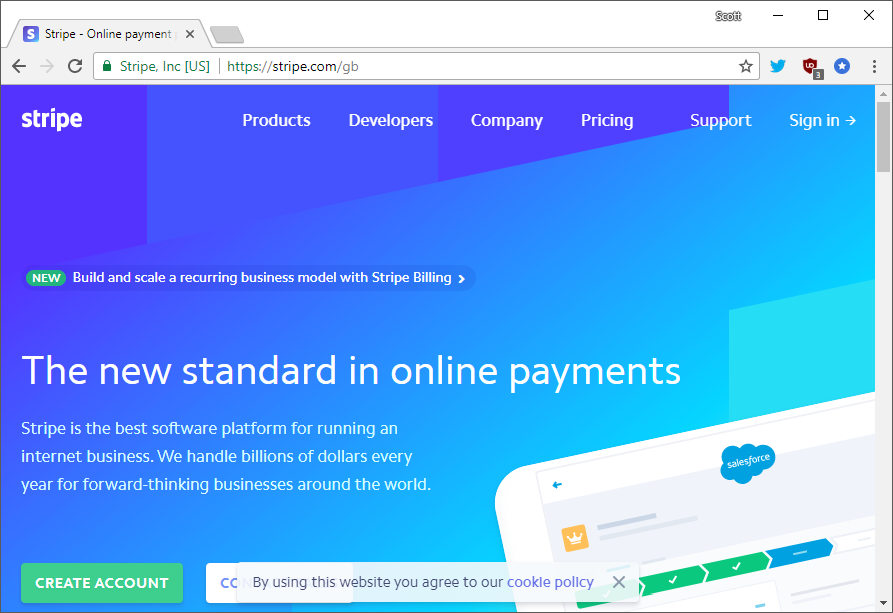
We need to be clear up front that Ian's certificate is absolutely valid and properly issued here. Legally registered company names do not provide any guarantee of being globally unique and he controls the domain stripe.ian.sh, there is nothing wrong here. The problem is that some CAs don't like it when you make them look bad, especially not when you're making their main revenue stream look bad. Comodo issued that certificate to Ian and his legally registered company but after it gained some attention in the wider community, Comodo were not happy.
I got an extended validation certificate for "Stripe, Inc" but in another state. Can you tell the difference?
— Ian Carroll (@iangcarroll) December 11, 2017
More: https://t.co/soIxWGwovs pic.twitter.com/4BXDdeg2h1
Following various discussions and debates online the community agreed that this certificate was perfectly legitimate, it met all of the criteria to be issued and no action was required. Comodo did not agree. Comodo did not agree at all. In fact, Comodo disagreed so much that they took action against Ian and his certificate, they revoked it.
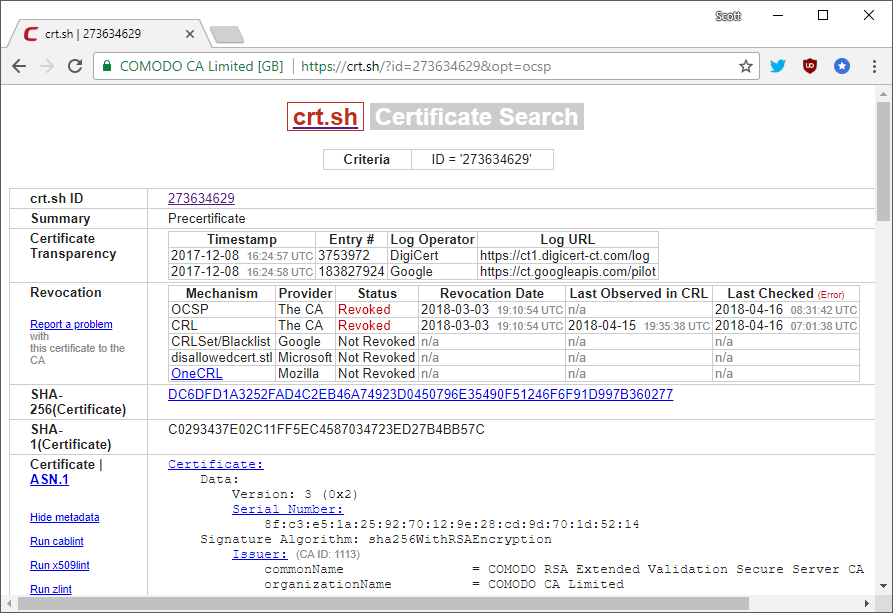
You can see the details of that revocation right here but yes, Comodo revoked Ian's certificate, despite him having done nothing wrong and having met all of the criteria to apply for and obtain it, which is why he got it in the first place. This represents a pretty significant problem because the CA has now taken his site offline. Without a valid certificate the website won't work so Comodo have essentially taken his site down. The poor excuse that Comodo came up with for this revocation was apparently that Ian was running a phishing site but I think we can all see this was because they looked bad. I prompted Ian to get another certificate but found that he didn't have the cash to burn on expensive EV certificates and he didn't get a refund for his now revoked certificate so he couldn't use that either (yes you did read that right, they revoked his cert and kept his money). Unhappy with the way this was playing out I offered to money for Ian to apply for an EV cert from another CA and he got one from GoDaddy.
https://t.co/YERaLaMJNr is back! Thanks to @GoDaddy and @Scott_Helme for the certificate. pic.twitter.com/bq4FJMuP3m
— Ian Carroll (@iangcarroll) April 11, 2018
The site was back and the proper EV indicator restored for the security and benefit of all! Except, it didn't stay online for long...
Either way, I'm sure @iangcarroll will be thrilled when he wakes up to find that GoDaddy took his site offline! pic.twitter.com/qG0GyY1jOb
— Scott Helme (@Scott_Helme) April 12, 2018
Yep, GoDaddy revoked the certificate and took Ian's site offline overnight. This is a really concerning event because the CA is wielding a great amount of power here and right now it's pretty apparent that they're abusing that power. Looking at the revocation the CA provided the reason 'cessationOfOperation' but Ian certainly hadn't stopped operating his site and most definitely did not ask for the revocation to take place.
Well @iangcarroll that didn't last long. EV checks:
— Scott Helme (@Scott_Helme) April 12, 2018
☑️ Own and prove control of domain.
☑️ Have a legally registered company.
☑️ Charged $$ and certificate issued.
Then at some point in the future:
☑️ CA arbitrarily changes their mind and revokes certificate... pic.twitter.com/5IdSGpy4zd
If you want the details of this revocation then you can find those right here but again, we're in a situation where a CA has issued a certificate, verified all of the necessary information including the legally registered company and ownership of the domain name, charged money, issued the certificate and then at some point in the future changed their mind. They revoked the cert, took his site down and that's apparently the end of it. The only difference this time around is that after Ian spoke to GoDaddy they did refund his money, how very kind of them...
The larger issue
The bigger problem here is around how the CAs are wielding the power they have and abusing their position. Yes, this might not be a glorious example of how great EV is and it might not exactly make the CA look good, but the response here is chilling. We've seen similar issues in the security community for years where someone points out a problem with a system only to be met by overzealous reactions and an inappropriate response. In revoking the certificate issued to Ian they have taken his site down and potentially caused harm to him or his business. Both of these revocations came after the fact, because the CA was concerned about their reputation. This is not and should never be sufficient grounds to revoke a certificate. Just think about that, what happens if that continues to be acceptable as we move towards a 100% encrypted web?

When the entire web is encrypted, and we're making great progress on getting there, the CAs become powerful gatekeepers of content that can be put online. My Alexa Top 1 Million report from Feb 2018 shows that over 38% of sites in the top 1 million are now redirecting to HTTPS. We've also discussed the problem of a CA being some kind of 'content police' on the web before and it's really not a great idea. Over a year ago in March 2017 I published Let's Encrypt are enabling the bad guys, and why they should to address the constant reports of Let's Encrypt issuing certificates to phishing sites. The CA should not, must not and cannot be some or any kind of censor for which sites get certificates to go online. CAs have technical criteria set out in the Baseline Requirements and EV SSL Guidelines and they do not include any kind of 'are you a good person' metric, to suggest that they should is terrifying.
Going forwards
I will continue to fund Ian in his quest to obtain an EV certificate that a CA won't later turn around and revoke for many reasons, the main reason being that he should be able to get one according to all of the rules and guidelines set out by the CA/Browser Forum. Demonstrating a perceived flaw or weakness in the EV system should not give a CA the power revoke that certificate and there should have been consequences for those that have already. Once we start down the road that a CA can revoke a certificate for [reasons], where do we end up? DMCA takedowns, copyright, trolls, trademarks or even writing an article critical of a CA? What about paypal-class-action.com, should PayPal be able to have that revoked because it contains a substring match for PayPal? Certificates are issued once the technical criteria for issuance is met and the only time that a revocation should be exercised is when the host that obtained the certificate requests it or another party can prove ownership of the associated private key. To use revocation for any other purpose is a slippery slope and once we start down that slope, it's going to be hard to come back from our race to the bottom.
