Like everyone else, I get a lot of spam emails that range from downright annoying through to deceptive phishing emails that are really dangerous. Today I got one of the latter and when I do, I like to see what can be done about them.
When they make it to your inbox
Various mail providers that I've used have some pretty good spam detection and the vast majority of this kind of crap you receive will wind right up in the Spam/Junk folder where it belongs. Every now and then though, something makes it to my inbox, and I always like to take a closer look at those.
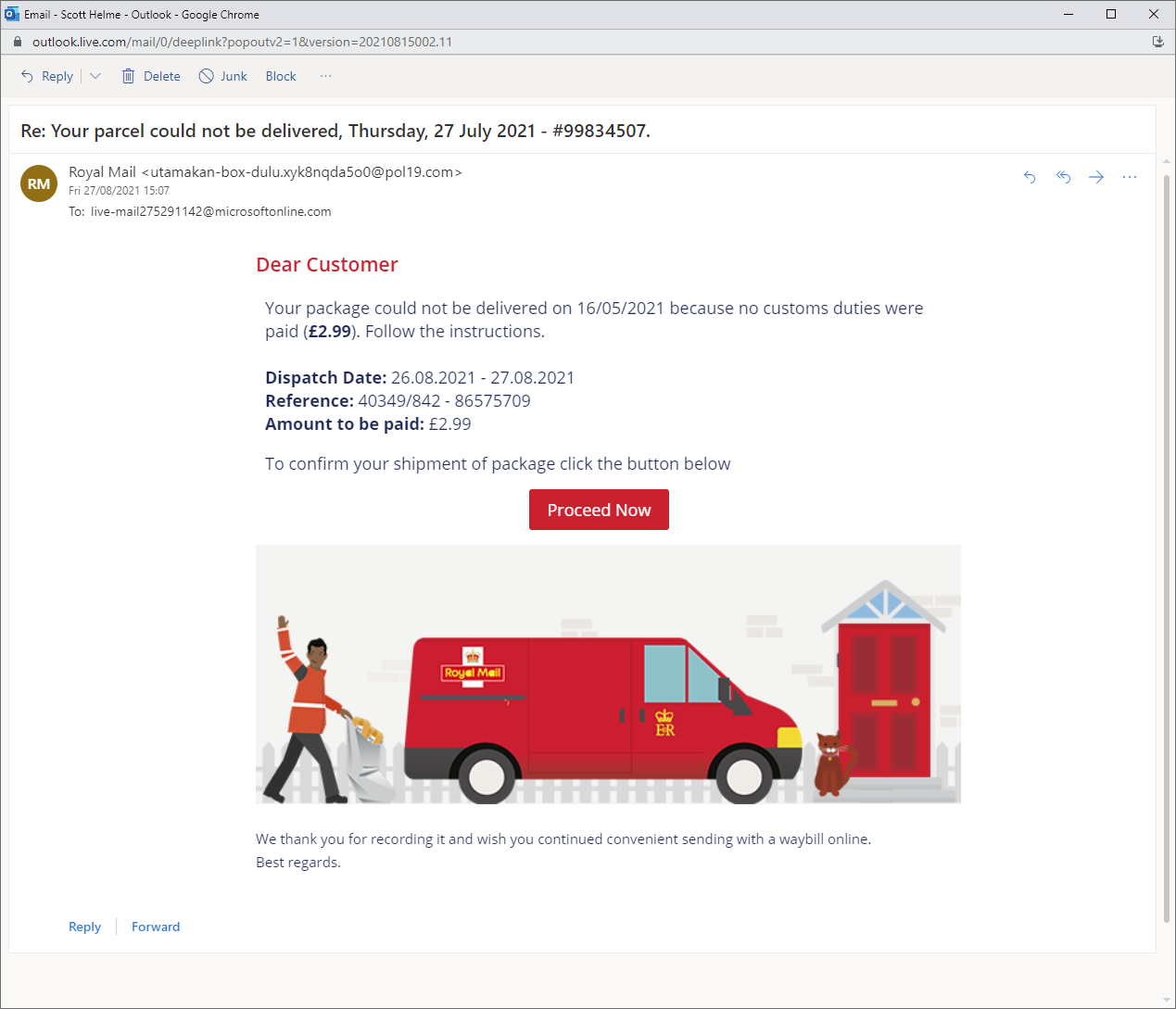
Throughout the pandemic, the amount of home deliveries and parcels people have been receiving has skyrocketed as online shopping has become even more popular. Scammers have caught on to that and 'missed delivery' scams have also skyrocketed via both email and SMS. As I said, it's not uncommon for me to receive phishing emails, but what was concerning was that this one made it to the top of my inbox, making it much more convincing, so let's take a look at it.
On first glance I hadn't realised the date in the first sentence was wrong, my eyes were drawn straight to the bold "Dispatch Date", I saw the "Amount to be paid" and of course the next step is the "Proceed Now" button. Emails like this are not uncommon and it seems plausible at first glance.
Looking deeper, it says "Re:" at the beginning of the subject line even though I've likely never emailed anyone at Royal Mail (our national postal service here in the UK) and my Spidey Sense was now really tingling. Over to an incognito window we go with a copy of the link from the "Proceed Now" button and I get the following redirect chain
https://www.homes4wiltshire.co.uk/ViewSwitcher/SwitchView?mobile=True&returnUrl=https://registerdomainid.createsend1.com/t/y-l-odhjiud-l-r/
https://registerdomainid.createsend1.com/t/y-l-odhjiud-l-r/
https://w3llson.duckdns.org/r/bFj0Et0
https://fi.uy/pi2f
https://secure01c.package-royamail.co.uk/That redirect chain leads me to this very convincing phishing page!
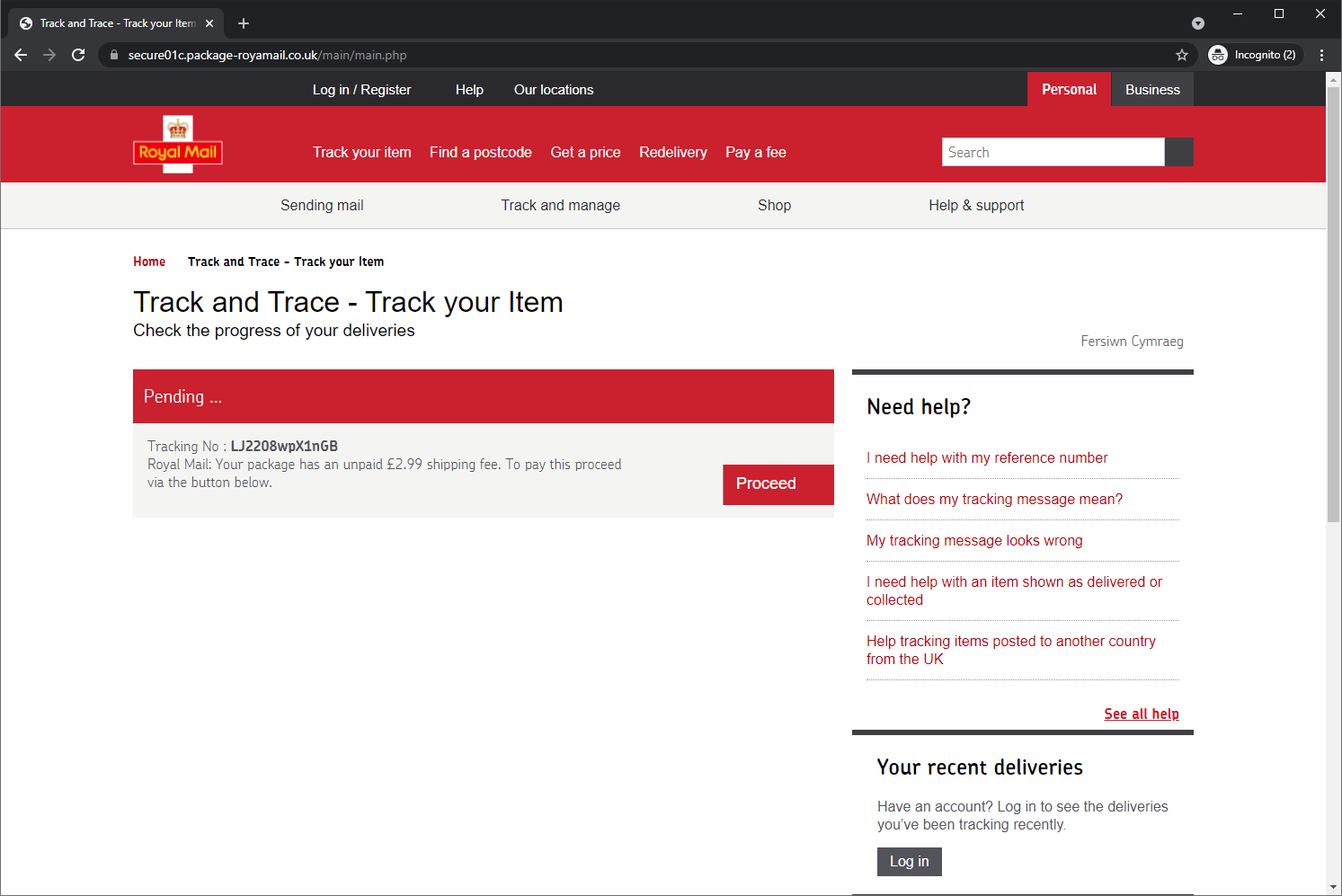
The absolute first thing I do when I come across any phishing page is report it to Safe Browsing here, as you should too: https://safebrowsing.google.com/safebrowsing/report_general/
If a site is reported to Safe Browsing and confirmed as a problem, it will be blocked and very quickly visitors will see this in their browser instead of the phishing page above.
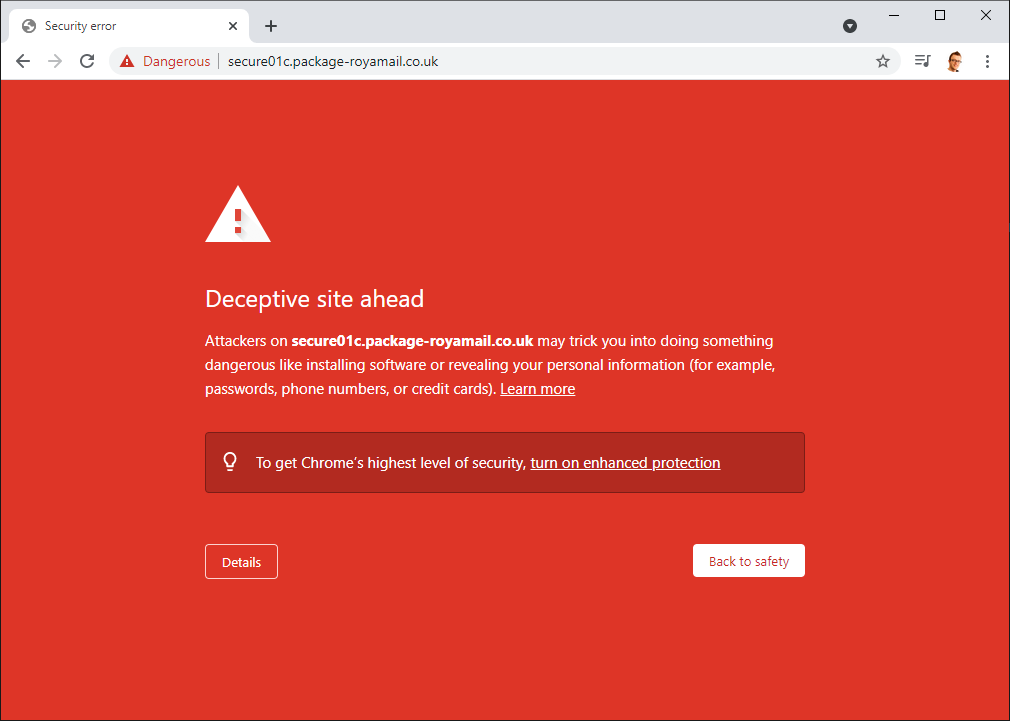
Shortly after reporting the phishing site it was indeed blocked and the email was moved from my Inbox to Spam without my action which was a nice touch.
Looking at the certificate for the site, it seems that this particular subdomain was setup on Aug 27th, the same day I got the email, via cPanel with a certificate issued by Sectigo.
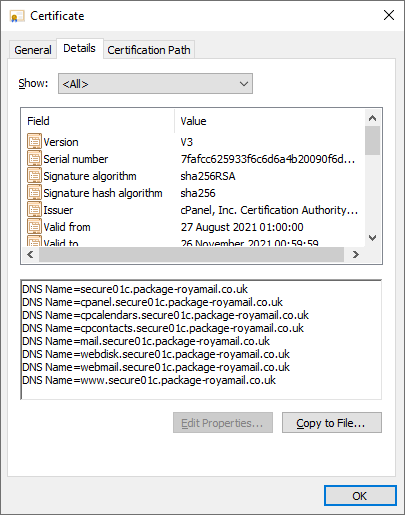
This is also the first and only certificate that the package-royamail.co.uk domain has had at the time of writing.
Why use the open redirect?
The problem with having an open redirect like the one above is that it can, and will, be abused by attackers in scenarios like this. The reason these open redirects are useful is that they add legitimacy to the URL in the email itself which helps it to bypass spam filters.
If an email provider were to check the domain reputation of homes4wiltshire.co.uk then it would come back as quite positive. It hasn't been flagged as being involved in any phishing/malware activity, it doesn't appear on any block lists, it's been registered for a long time and various other factors all indicate that it's a 'good' domain. The email provider likely wouldn't have any concerns.
If you were to take a look at package-royamail.co.uk then one of the biggest alarm bells that would immediately ring is that it was registered only hours before the email was sent, which is a pretty big cause for concern and would likely get caught up in many filters, landing it in Spam. This is what the attackers want to hide and is why the open redirect on a 'good' domain is so useful.
The other negative here is that it can start to have an impact on the domain reputation of homes4wiltshire.co.uk as they're linking out to sites being reported as phishing sites. If providers start to pick up on that and put it as a bad mark against your domain, it could be harmful in the long run.
Break the chain
The first link in the email went via homes4wiltshire.co.uk which is a local government website here in the UK so my first idea was to send them a DM on Twitter. They have a verified account and a few followers, so maybe I will get a speedy reply.
I dropped them a DM and just before I left the page I noticed they had a phone number on there and thought it might be nice to speak to someone and relay the message instead. I called up and spoke to someone in customer services and it's always really odd trying to explain to someone that you've identified an issue in their site! The message was well received though, I explained who I was and that they could Google me to confirm I wasn't some shady person calling from the dark corners of the web. The call was returned just under an hour later by someone responsible for overseeing the website in question and they told me it would be passed to their external web development company.
10 days later though I hadn't heard anything, so I decided to chase this up as the open redirect was still in place and working exactly as it was before. I couldn't get through to customer services at the council and tried the direct line I'd received a call from previously, but didn't get through so left a message. Later that evening I got a call back and again heard from someone who was genuinely concerned about what I'd raised, but didn't have any update for me.
Having worked in local government here in the UK, and in some quite large tech companies, I understand how it can be difficult for someone either on the inside or the outside to get a message through to the right places. These organisations aren't always capable of moving as fast as we might sometimes like, but so far everyone I'd spoken to was giving all the right signals so I asked who their provider was and wondered if maybe I could help expedite matters.
Once I realised they were such a large provider, I wondered if this issue was isolated to just the site I'd found it on, or if there was a pattern. Once I knew what I was looking for, it wasn't hard to find a few more examples.
https://www.durhamkeyoptions.co.uk/ViewSwitcher/SwitchView?mobile=True&returnUrl=https://scotthelme.co.uk
https://www.tyneandwearhomes.org.uk/ViewSwitcher/SwitchView?mobile=True&returnUrl=https://scotthelme.co.uk
https://www.hampshirehomechoice.org.uk/ViewSwitcher/SwitchView?mobile=True&returnUrl=https://scotthelme.co.ukWith a few seconds of Google-fu, I'd found a handful of other sites all with the exact same issue. It seems this isn't a single incident but judging by the common formatting in the URL, it's likely the same issue in an application that's been deployed many times. I checked for a technical contact on the Civica site and also for a security.txt file but I couldn't find one so I decided to reach out on Twitter. This isn't something I like to do but there were a few factors pushing me towards getting this fixed sooner rather than later.
- The email did end up in my inbox which makes it more dangerous as people are far more likely to get caught by the scam.
- It was sent on a Friday afternoon of a Bank Holiday (Public Holiday) 3-day weekend here in the UK so it was unlikely anyone would be able to fix this for several days after it was sent. Was this a coincidence or careful planning by the attackers?
- I'd since learned of two other people who had contacted the council to report similar issues with phishing emails redirecting through their site.
- The fake website was a good effort at ripping off the official Royal Mail website and looked convincing.
It's not a critical issue where a database is open to the Internet, but there was a good chance that innocent people would get scammed by this, so I reached out.
I need a security contact @CivicaUK for an issue that's being actively exploited. We're 10 days in going via standard channels, no joy.
— Scott Helme (@Scott_Helme) September 6, 2021
I was quickly contacted by a follower who worked at Civica, which worked out quite nicely, so I shared all of the details of what I'd found and 2 days later I had an update call in the morning with the company. The issue itself had already been identified and fixed but was several weeks away from being deployed due to their deployment schedule. Given the new understanding around the severity of the issue being actively exploited, the patch for this issue was carved out and would start being pushed out from 8th Sep. I've since tested that the issue is resolved and also checked the handful of other sites I found and I'm happy to report everything is now good.
Responsible Disclosure
From receiving the phishing email on Fri 27th August, all the way through to the patch being rolled out, only 12 days elapsed. If you consider that this started right before the weekend, and it was a 3 day weekend here in the UK due to the Bank Holiday (Public Holiday), that's not bad at all. The council were receptive to my initial communication which was quite refreshing and Civica responded quickly once I contacted them too. All in all, I've been quite impressed with how this progressed and I'm hoping that this is good indicator that the industry is improving. Other researchers will know how hard it can be to contact an organisation as some stranger from the Internet and tell them they have an issue. It's very common for that to not go down well at all!
This is one of the biggest problems we need to solve: ad hoc, usable, secure communication with mutual authentication. You can't just call up a retailer and say "Yo, I need to talk to your security team." Or even "No really, I'm from the FBI." https://t.co/gvNZVN6OxQ
— Wendy Nather 🐝🔑🗡 (@wendynather) September 7, 2021
Beyond that, I hope this just highlights how something as simple as a redirect can end up causing quite a bit of bother and maybe have a poke around to see if you have any in your application!
