LinkedIn have recently launched their new service called Intro. In a nutshell, you can now see the LinkedIn profile of whoever emails you right there in your email, without having to use another app. At first glance this seems like a fairly innocuous feature, but it has generated a huge backlash in the security community. Let's take a look why.
'Intro'duction
LinkedIn announced Intro over on their blog and with a title like "doing the impossible" I was immediately expecting to be blown away by what I was about to read; it turns out I was blown away, but for all the wrong reasons. The purpose of Intro is to allow you to get more of an idea about who is emailing you without having to look them up elsewhere. If they have a LinkedIn profile you can view it right there in the email, alongside their picture.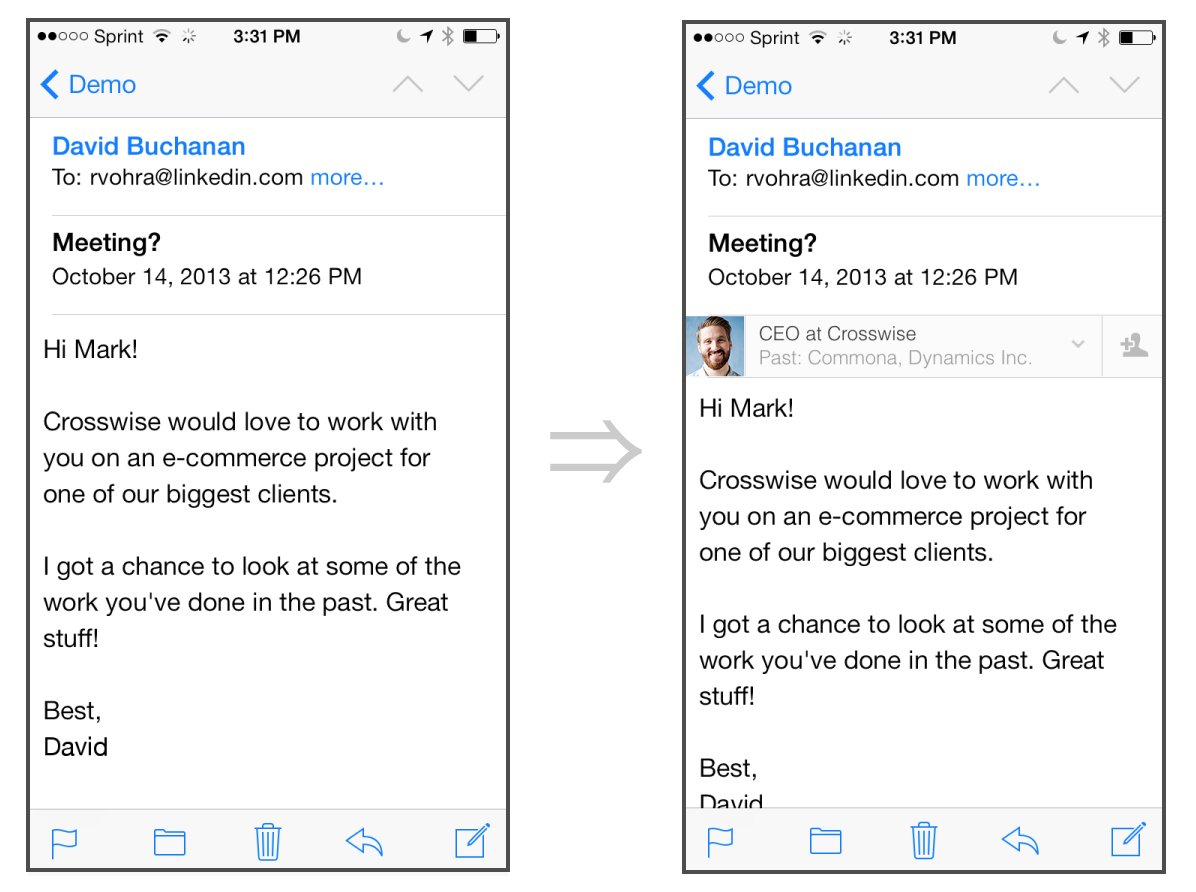
"Great!", I hear you say! "Now I can see exactly who it is I'm speaking to without having to put a face to the name". Okay, so what's so bad about that? Well, it's how they achieve it.
Impossible #1: Extending the iOS Mail Client
(Yes, they actually created a list of "impossible" tasks)As we all know, the Apple platform is generally quite locked down and this has helped to create a relatively safe ecosystem. When compared with a platform like Android, which has countless malicious applications in circulation, the very restrictive practices over at Apple have helped to shield users, to some extent. One part of this restrictive nature is that a developer does not have the ability to extend the functionality of the built-in mail app, which made the title of impossible task #1 somewhat confusing. Having read the first sentence though, it seems that LinkedIn were already aware of this, stating "Our key insight was this: we cannot extend the mail client". To get around the actually impossible task of extending the built-in mail app, LinkedIn needed to shift the integration off the device. They needed to make the changes before the email arrived at your device. Their solution was to act as a proxy for your emails.
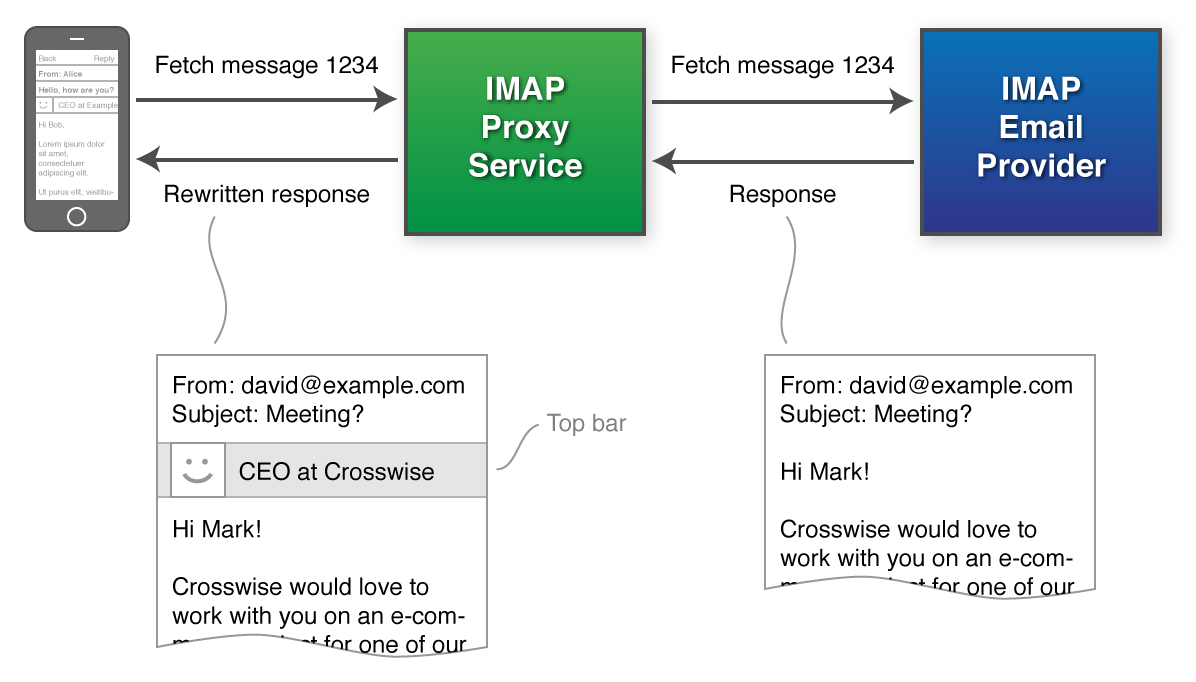
By inserting themselves as a Man In the Middle, yes that does sound scary, LinkedIn can now intercept your emails after they leave your email provider and before they arrive at your device. Whilst they have your email at this halfway house, they open and inspect it to determine if the sender has a LinkedIn profile. If the sender does have a profile, LinkedIn perform a little code injection, sounds even more scary, and insert the appropriate code into the email, to display the profile of the sender. Once that's done, or if the sender doesn't have a profile, LinkedIn then forward the email on to you, it's rightful owner. It's pretty much the same story on the way out too. LinkedIn append a signature to your email for you and then forward it on.
Impossible #2: Interactive UI in Email
I still can't quite understand the need to declare that ineractive UI in an email is an impossible task because all that seems to be happening here is the use of the CSS :hover state. A commonly used and widely documented feature that LinkedIn have coupled "with some creativity" to embed a profile into the email message that expands out when you hover over the info bar (in the iOS mail app a single tap is hover, double tap is click).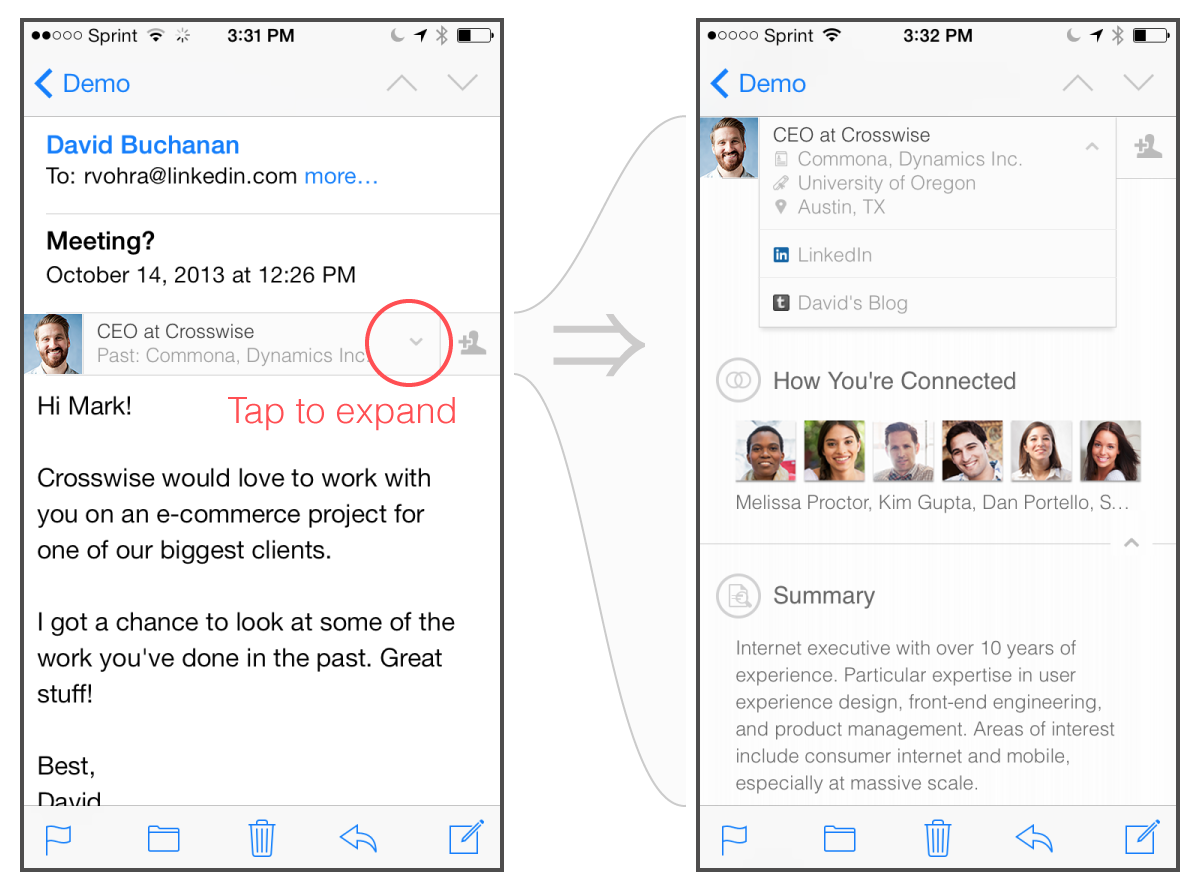
Impossible #3: Dynamic Content in Email
Moving on to impossible task number 3, LinkedIn inform us that if we ever make a connection with someone after exchanging a few emails, that the static content showing that you weren't a connection would become outdated. For this reason it would need to be dynamic and update to reflect your current relationship with the sender, even if you go digging through old emails from before you connected. This impossible conundrum was solved with the use of an <iframe>. Yes, an <iframe>. Another widely used and well documented feature of HTML.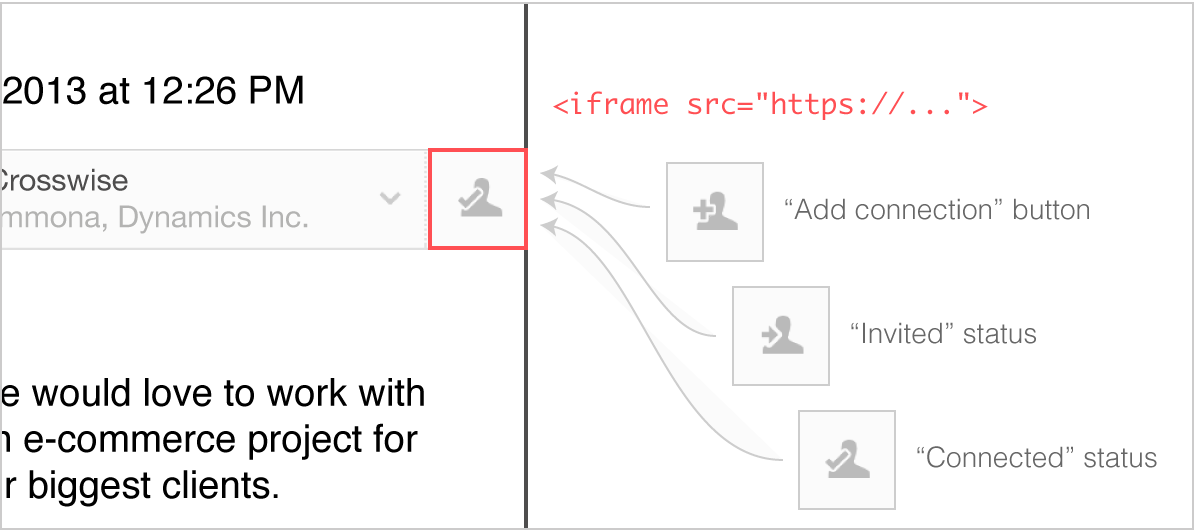
The little icon that represents your connection status with the other person is simply loaded inside an <iframe>. Each time you open the email you can load an up to date status icon, or if you have no Internet connectivity, the icon defaults to the connection status from when the email was first received.
Impossible #4: Easy Installation
To install the LinkedIn IMAP servers as a MiTM for your emails, the developers (quite rightly) decided that asking the user to change or setup server host names, SSL/TLS settings and credentials was too tedious and likely to result in errors. To get around this, LinkedIn decided to take advantage of configuration profiles, a feature commonly used in enterprise environments. For this easy installation, all LinkedIn have to do is "simply ask the user for their email address and password, autodiscover the email provider settings and send a configuration profile to the device". Right, simply hand over your password. Interesting that the LinkedIn User Agreement states that "You agree to: (1) keep your password secure and confidential; (2) not permit others to use your account; " yet expect other service providers to not have the same clauses in their terms.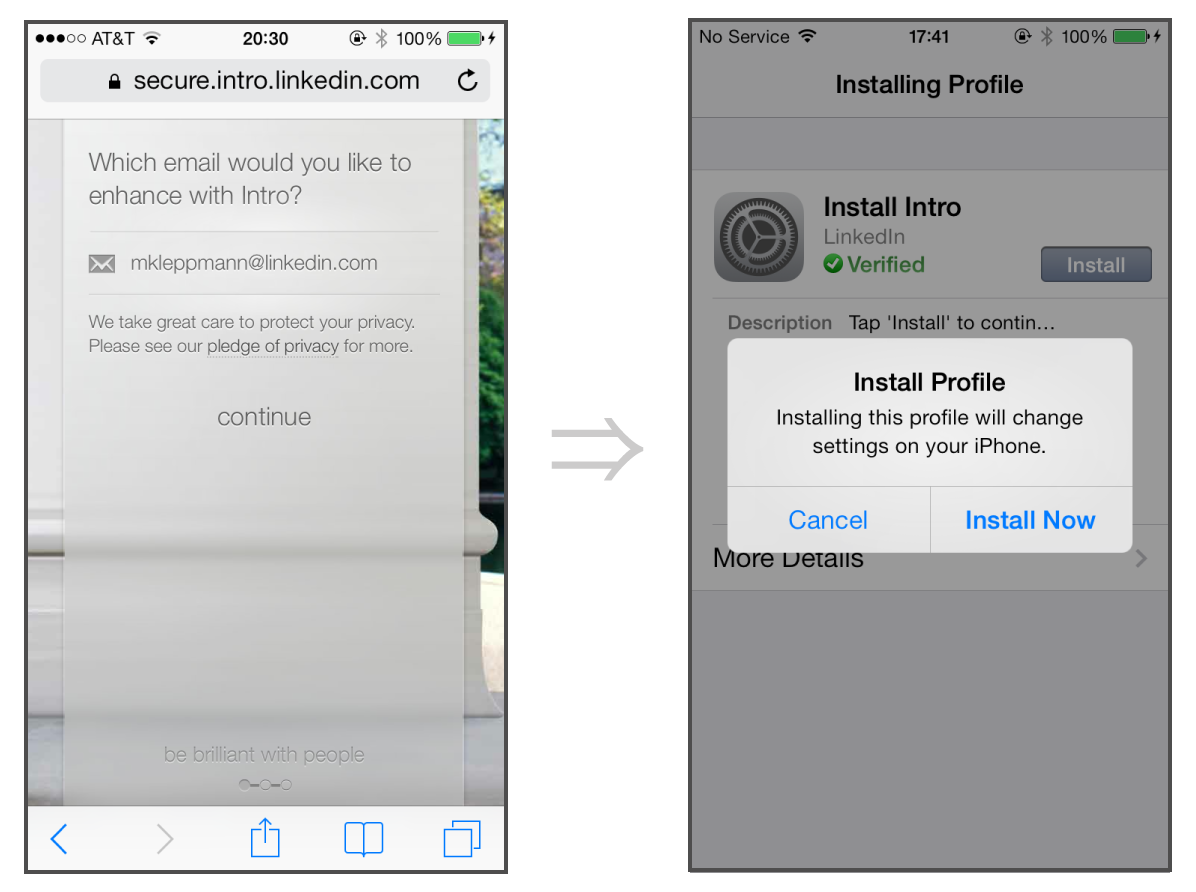
So what are people worried about?
While the entire process of being a MiTM, scanning your email and injecting code into it is entirely automated and done by a machine, not a human, it still presents an additional link in the chain. With every additional link comes the possibility of introducing a weak link. Bishop Fox goes into quite a few (very good) points about why you should not introduce Intro into your environment. Points like, is it a breach of your corporate IT policy, do we trust their security, who has reviewed their security, what happens with the meta data they glean and what happens when they get hacked? After all, with that much access to privileged information, they have to be making themselves a target. Another, very simple point I see quite often overlooked is, what happens if there is a problem with Intro and the service is offline? Your chosen mail provider may be up and running all day, but if Intro goes down, you lose access to your emails. At least, without reconfiguring to access them the traditional way, you do.
Conclusion
The slightly arrogant nature of the original blog post. and the decisions that LinkedIn have been forced to make, due to the restrictive nature of the iOS platform, have lead to a poor reception in the Info Sec community. Allowing a 3rd party unnecessarily to proxy all of my private and confidential emails, just for the addition of a LinkedIn signature or header, is far too high a price to pay. You're providing unfettered access to your emails for a tiny bit of HTML/CSS to be injected into them. Security and convenience have always, and always will be, at odds with each other but there is a balance that can be struck. Unfortunately, Intro is asking just too much.
Update: LinkedIn issued a response to some of the concerns from the community here. They assure us that they created "the most secure implementation [they] believed possible" and go on to use equally vague statements. It's also worth noting that their track record isn't particularly great when it comes to password security or email privacy.
