Last week I launched the new version of securityheaders.io at PasswordsCon in Cambridge. Here's a quick round up of what's new!
Scoring!
The biggest and best new feature is the brand new scoring system. Inspired by the rating system on the Qualys SSL Test, created by Ivan Ristic, I wanted a quick and easy way for people to understand the information that was being presented. All of the headers were previously colour coded, which helped, but it still required some reading. I'm hoping the new scoring system will change that.
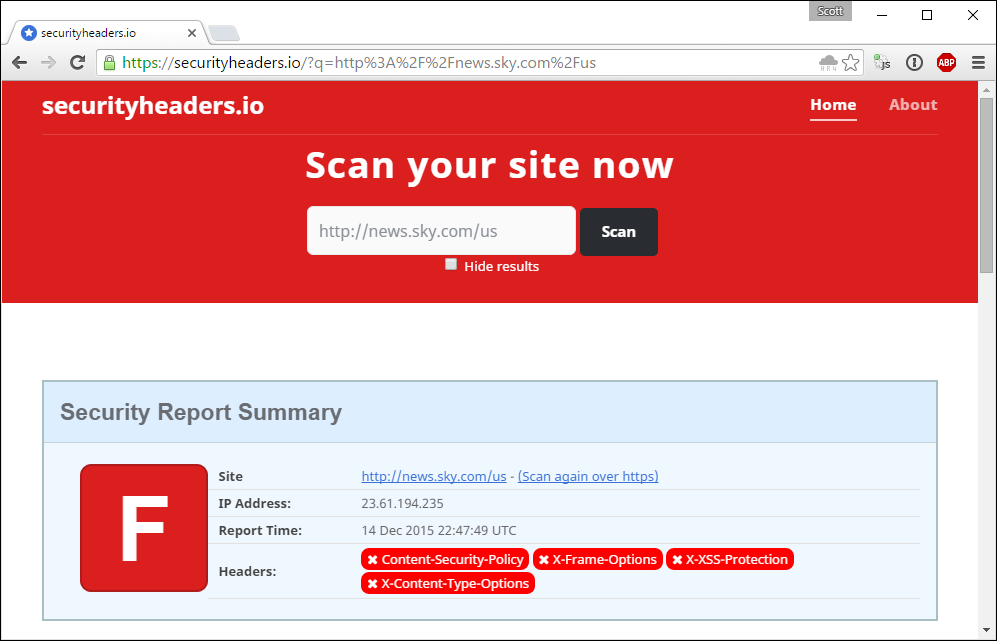
Sites that implement all of the appropriate headers for the scheme of the current connection will be rewarded with a very positive response. At a glance you can see the score and the headers that were or were not implemented. As you can see, the A+ score is quite clear!
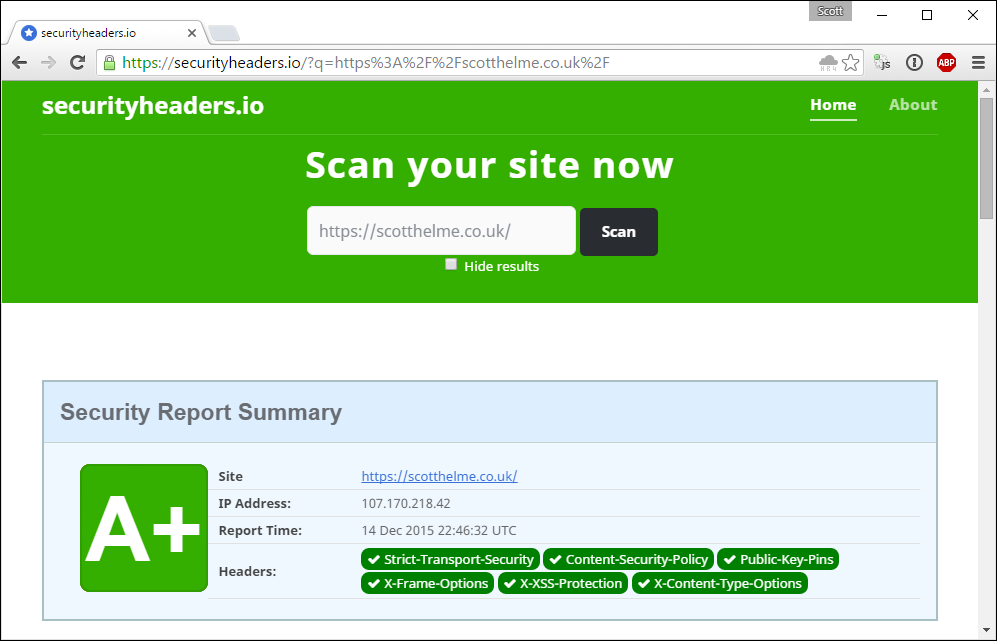
The same also applies for the other end of the scale for sites that don't implement any of the headers and score the lowest grade, an F.
New home page
The old home page was a little... bleak. With the introduction of scoring I've now created a few metrics that can be tracked on the home page. There's the Grand Totals section, covering all scans (excluding hidden scans), Recent Scans which is just a running list of all recent scans, the Hall of Fame which shows recent scans that achieved an A or A+ and the Hall of Shame, which shows recent scans that scored an F.
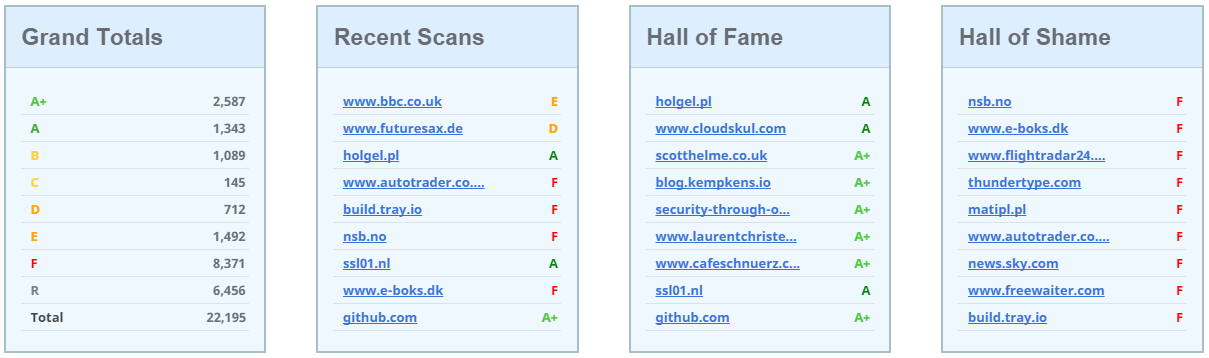
This is a handy section to take a look at how the different scores appear and keep an eye our for good and bad examples of header implementations.
Hidden scans
This was mentioned in the beta but was very commonly requested as soon as the service went live. People wanted the ability to hide their scan results from the public dashboards. I was a little hesitant about this at first because all of the information here is just HTTP response headers, it's publicly accessible from the dev tools of any browser. If a site has a bad configuration then hiding it from the main page doesn't really change much except them keeping their poor configuration a little more quiet. The argument that swung me was people testing sites that weren't quite ready for launch but who wanted to make sure that things were straight before they announced. This seemed like a fair enough argument and I didn't want to put people off testing sites pre-launch, it's better that they get things right early on. That's why, the day after launch, I added the hide feature.
When checked, the 'Hide results' button will prevent the score from the scan being published in the public dashboards on the main page. Everything else will work just as expected. The results will also not be included in the counts for the Grand Totals column.
Redirects
How to handle redirects was a tricky one. Most of the headers have no impact when delivered with a redirect, things like CSP and X-XSS-P are meaningless as no content is rendered into the DOM. That said, headers like HSTS and HPKP are still cached and applied by the browser even on a 3xx response. Because of this, I decided to handle redirects a little differently. I didn't want to give an A+ to a site for issuing just HSTS and HPKP on a 301 which might not be clear to everyone using the site. For this, I created the 'R' grade. This makes it clear the site being scanned issued a redirect, but still allows the inspection of headers that were delivered with the redirect, which would be lost if I automatically followed it.
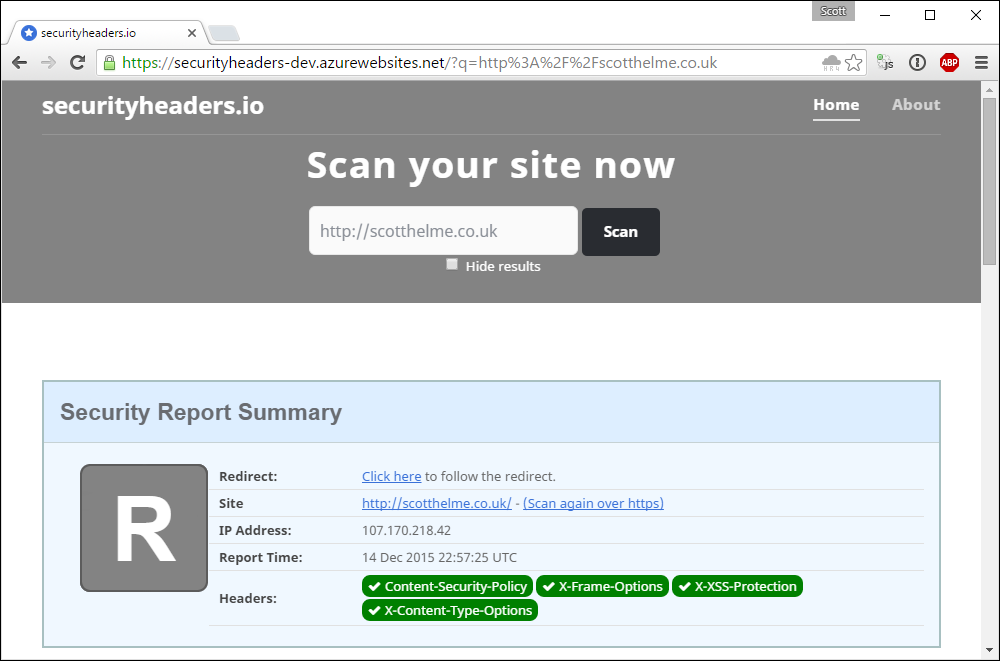
As you can see, there is a new 'Redirect' section in the summary table that provides a link that you can click to follow the redirect issued by the site. This may still need to be made more clear so feedback is welcome if you have any ideas on that. Other than that, enjoy!
