Let's Encrypt are amazing and regular readers will know I'm a huge fan of theirs, having covered them numerous times on my blog. They issue more certificates and cover more domains than any other CA out there, all for free. Whilst all of these are amazing facts, we are creating a lot of dependency on them so having a backup is (always) a smart idea.
Let's Encrypt
I've blogged about Let's Encrypt a lot, I have 16 posts on my blog that are tagged with Let's Encrypt. They're free, they're open and the automation is so easy I once hacked an Amazon Dash button to issue Let's Encrypt certificates! With their amazing growth one thing that has crossed my mind is what happens to us if they go 'pop'. Sites may be moving to Let's Encrypt because they're free, which means they couldn't afford to replace those certs if they had to pay. Perhaps a site can only do it at scale because of the automation so if they lost that it wouldn't be attainable. There's lot of reasons that having a single CA is a bad idea and it's even a topic I cover in my TLS training course, The Best TLS Training in the World. If something happens to your CA, it could have a big impact on the availability of your site. For that reason, having a backup CA is always a good idea and I want to show you just how easy that is.

The ACME protocol
To obtain certificates from Let's Encrypt you use something called the ACME (Automated Certificate Management Environment) protocol. The ACME protocol allows you to do everything you need when communicating with a CA to obtain a certificate and it's an open protocol. There's nothing specific to Let's Encrypt here and wider support of ACME is something that I've been hoping to see for some time now. We're finally at a point where more CAs are starting to support ACME and that means that any tools/scripts/processes you currently use to get certificates from Let's Encrypt should work perfectly well with any other CA that supports ACME.

Getting certificates from another CA
If another CA supports the ACME protocol then using any ACME based tool to get a certificate should be a simple case of pointing the tool at a different CA. Not all CAs are going to give away certificates for free, and the ACME protocol has support for payments, but I'm going to be using Buypass who are a Norwegian CA that support ACME and offer free certificates.

Buypass have a little information on their 'Buypass Go SSL' offering and some technical details which is where you need to get started if you're looking to obtain a certificate.
Using Certbot
The official docs linked above guide us on using Certbot for obtain a certificate so that's where I started out. It's the official client from the EFF to "obtain certs from Let's Encrypt" and "any other CA that uses the ACME protocol".

I've done the registration step in the Buypass docs and the next command you run is the command to issue a certificate. That's.... pretty much all there is for me to talk about.
certbot certonly --webroot -w /var/www/html/home/ -d acme-test.scotthelme.co.uk --agree-tos --server 'https://api.buypass.com/acme/directory'With that, a certificate is issued, just as easy as if you'd used Let's Encrypt!
-----BEGIN CERTIFICATE-----
MIIGSjCCBDKgAwIBAgIKCTyzeSTaACj96zANBgkqhkiG9w0BAQsFADBLMQswCQYD
VQQGEwJOTzEdMBsGA1UECgwUQnV5cGFzcyBBUy05ODMxNjMzMjcxHTAbBgNVBAMM
FEJ1eXBhc3MgQ2xhc3MgMiBDQSA1MB4XDTE5MDEwMzE2MjEwNVoXDTE5MDcwMjIx
NTkwMFowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKZgnsfDLeYj
r6s6P1OqZM12e6ydgfsxr26Zo7diIs2ihmBRiUHSd3Q/Tokx/0D7uV8L016RnUsl
j5EjQ+auNEBrHdCckfGzDYLvrTGASbTpzqHM5yz7khIrRZkHNkgYGA4+3KoNLhvA
aTjrJnLIwwmXYvsvKegGgBqERjvEgM+IP3a17GMM/RA4qF7c2wvQeaF5qOXlRdV+
fKHhcEB+lyqCuNxM8TV4l87fYHgsWf6zB0k5zLaof/Lxv7w0xX2FruzsMDxqgeUW
GVZlzAm95GNTyWz7bjHJKwQlDCRgwae+i4bZEDWW8bkzwqsdP/xDTKgONmyng/Xx
mxF2PRIwyt0CAwEAAaOCAnkwggJ1MAkGA1UdEwQCMAAwHwYDVR0jBBgwFoAUJ1Kk
by0qq0CTkOzWacv+fGE7fEIwHQYDVR0OBBYEFLF2LoK1CJb5CjchBFPO5Pa4sScT
MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
HwYDVR0gBBgwFjAKBghghEIBGgECBzAIBgZngQwBAgEwOgYDVR0fBDMwMTAvoC2g
K4YpaHR0cDovL2NybC5idXlwYXNzLm5vL2NybC9CUENsYXNzMkNBNS5jcmwwKAYD
VR0RAQH/BB4wHIIaYWNtZS10ZXN0LnNjb3R0aGVsbWUuY28udWswagYIKwYBBQUH
AQEEXjBcMCMGCCsGAQUFBzABhhdodHRwOi8vb2NzcC5idXlwYXNzLmNvbTA1Bggr
BgEFBQcwAoYpaHR0cDovL2NydC5idXlwYXNzLm5vL2NydC9CUENsYXNzMkNBNS5j
ZXIwggEEBgorBgEEAdZ5AgQCBIH1BIHyAPAAdgC72d+8H4pxtZOUI5eqkntHOFeV
CqtS6BqQlmQ2jh7RhQAAAWgUhK+ZAAAEAwBHMEUCIQCltSCGpl6jvcEUEFBW1KOu
eXe5/lug5slQS3UB1F+/PAIgANvSoEEN3Qeh/EKrOQnzsgwcmRrRXGuxbk8+DVm5
dIIAdgBVgdTCFpA2AUrqC5tXPFPwwOQ4eHAlCBcvo6odBxPTDAAAAWgUhLDSAAAE
AwBHMEUCIH1tDAbHafX5ZMPr/wjI5q01rpJq7d3ezKKZPdGtOJ5dAiEA+VJYXuwP
lJYMy2Rc7Mw01N20YWfhC7ETaHTWv4WIlBowDQYJKoZIhvcNAQELBQADggIBAI9O
a+ECe2BHU4aq5/GvJ8eRYu4a+Y+cZq69HMNfX9tXlhTgtll+XnHoGqGx0IBb23bh
1jse2ZdgcY+d0eWCEQkhz1yR9urWaib/rsqbYpWXjlNJp9v79mThb9PTrbkJE92E
Dns3RRcrPkunrh7ReZpqqy6hRtaR2V/sI/4pKJa2rKArtmmPo3JamJXaJkgTh/0J
vLqQencTcfOJu88xeu3hbC/STvgUmEZX4/5Om01lOmbXLs6P6AaVW30jAATeSexG
oDzBTwYghU1vM8yxsFPHyErH+JseJyWtFBZo2D0qmHMVbqWXwh/JqytNC9/OCDbm
Tx7sPcfYPHSzuOXUTohl1pEOisdjngNwzu0qyatUC0/XmIWkcF97YACBvLhp0uMR
y4Iqn0F6SrvlSL2KdxaYmr8IZvnfPxvEV4bgiurfhuOk3VnGb/Sh129pQP8G3lbm
o7fmqKNMyWdmMMw6//SZPLuPjtzJ25hslduxYOghOrUsLL7b1dpScpVMQ02QtYZn
SwtqgIWJbhlkvNvJkF+Xf/o43yN3/ZyKLtBx/DTjDGIvEgd2NWQrwa7m88Kh6T2D
6fqnVpcQcaDnOLxnz242rIFQgbb3UIp3UGvtf/rZlo0ybJcK2rjeeXzMIGDO1LvI
h4T0jFehfT+bXnXs2VBNCM8u+1vq1gtsbw8PCp/B
-----END CERTIFICATE-----If you want a prettier view of that you can copy/paste PEM data into our PEM Decoder over at Report URI:
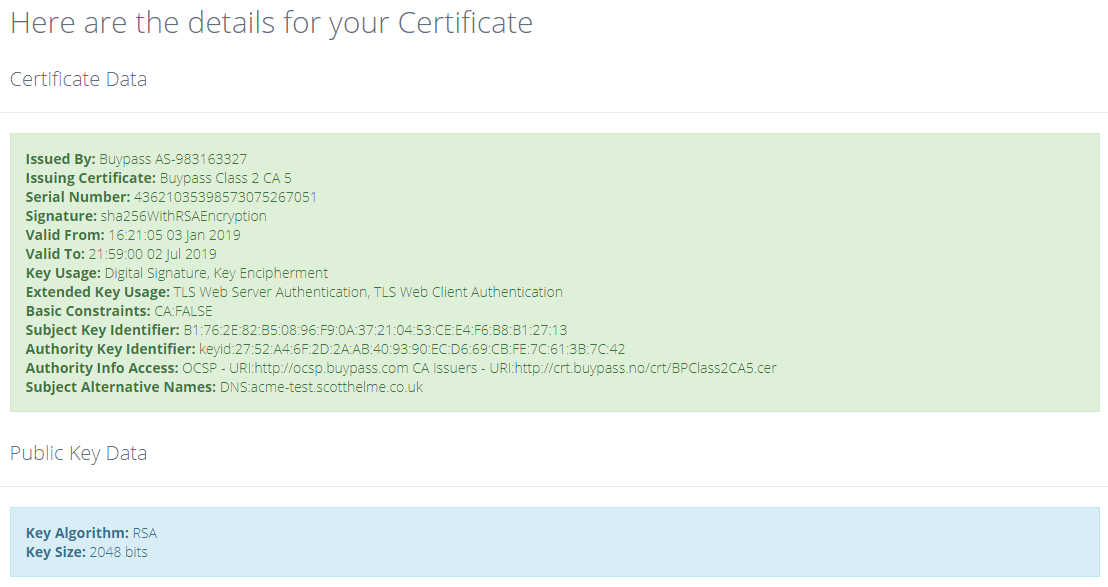
You can also see the CT entries on Censys and Crtsh to see that these certificates definitely do exist and were issued by Buypass.
Using acme.sh
Another awesome client that I've used a few times is acme.sh and just like Certbot it's geared up to get certs from Let's Encrypt but it's easy to switch it over to Buypass. Simply use the acme.sh command with the --server flag and set the Buypass endpoint.
./acme.sh --issue --dns dns_cf -d acme-test.scotthelme.co.uk --server "https://api.buypass.com/acme/directory"That's it, when you run the command to issue a certificate the tool will point itself at the Buypass API instead of the Let's Encrypt API and because they're both compliant ACME endpoints, it all just works. Once that's run you have your new certificate ready to go!
-----BEGIN CERTIFICATE-----
MIIGazCCBFOgAwIBAgIKCT2mO5A06GGm0TANBgkqhkiG9w0BAQsFADBLMQswCQYD
VQQGEwJOTzEdMBsGA1UECgwUQnV5cGFzcyBBUy05ODMxNjMzMjcxHTAbBgNVBAMM
FEJ1eXBhc3MgQ2xhc3MgMiBDQSA1MB4XDTE5MDEwMzE3MjAwOVoXDTE5MDcwMjIx
NTkwMFowJTEjMCEGA1UEAwwaYWNtZS10ZXN0LnNjb3R0aGVsbWUuY28udWswggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQD66KumbvQ3ySA6ZjHLP8iJnTDl
pr0ehmrq6QyGLkdpRTST8tG1y2qhqqCDjdmTlg6rBG20QAPXMIjGSxpGS2dnRZvV
sZ3ucatRLHxLc0NJxtwRKb//DiQhBBhWHI+QylxZ/x/Yc7UPtnemjQHlVYJcR5X6
i/fec9SveOKiLqSbGHqr7grTy0BKokZe3QItYvcslZSQcWxfXBVce+FM6Z6AmTGw
smVanneFVS1OMSke4g+noO9hHbgqzHSUDQKrhwupXnRj8w9oCn0tzVVTop4qa1tn
dcPzS3aOO+EVUZs4cHMazmAOAhPbc50EXLRtUT3ZK02iL+puTC+2Dw7FZxJDAgMB
AAGjggJ1MIICcTAJBgNVHRMEAjAAMB8GA1UdIwQYMBaAFCdSpG8tKqtAk5Ds1mnL
/nxhO3xCMB0GA1UdDgQWBBS3ST7uIILQS/m6IjbVBqew66pcOzAOBgNVHQ8BAf8E
BAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMB8GA1UdIAQYMBYw
CgYIYIRCARoBAgcwCAYGZ4EMAQIBMDoGA1UdHwQzMDEwL6AtoCuGKWh0dHA6Ly9j
cmwuYnV5cGFzcy5uby9jcmwvQlBDbGFzczJDQTUuY3JsMCUGA1UdEQQeMByCGmFj
bWUtdGVzdC5zY290dGhlbG1lLmNvLnVrMGoGCCsGAQUFBwEBBF4wXDAjBggrBgEF
BQcwAYYXaHR0cDovL29jc3AuYnV5cGFzcy5jb20wNQYIKwYBBQUHMAKGKWh0dHA6
Ly9jcnQuYnV5cGFzcy5uby9jcnQvQlBDbGFzczJDQTUuY2VyMIIBAwYKKwYBBAHW
eQIEAgSB9ASB8QDvAHUAu9nfvB+KcbWTlCOXqpJ7RzhXlQqrUugakJZkNo4e0YUA
AAFoFLrEMwAABAMARjBEAiBhtgg4l9vVq/xOwMYedqHxvJXHx+UiGYF3JwuvvB8k
gAIgQSx10RjHrU/yl764EKt2sTOSJGELahDRCxr6g45mSv4AdgBVgdTCFpA2AUrq
C5tXPFPwwOQ4eHAlCBcvo6odBxPTDAAAAWgUusWZAAAEAwBHMEUCIQDiDS4ONeCH
YOL+6iXutm7zieDq2qg6neQTwjD8UipriQIgItnx+0mwueyE4MWW7rxapGAgPI2R
fmjoRY9piB/ek0UwDQYJKoZIhvcNAQELBQADggIBABtrtpQBPvR+1neVFECRkp2S
KYM1zaaZfvB50neUOWXXjAEYtrS3Yte/Z5eNIdDBfy+0JY8iPdQGP1yyey9ivmXc
VMkiERWBQo/Qp2ew1fYHxj4H7z7BTZ+GhlBlyzPkf62fG92vfpWgJZ+aeLRCoR2C
L5SNHEhziySQNTFishm7FW6XwZZhtIBND4ofK7SJjk0Lwhn94je8hSUEQukad7oH
VaypSmuXtr/b9SiDQJPqkO3sp9+FtI274rJES8KpvmUZm80d6ycemEgoXXXk3DeN
jrhTRz+F7wjC29dsp2ZmRK2KFDTfmpEoW437EkkISjOt1MU23UPzhduSO7UeWUsW
HLGqj7TK/nubjeO6fqLashROwGeZwx91zdprQnD8gyxZESo56rLtWfFNV1eNraLG
QB44zvi5sW37zD5A8JVOj5LbX8j+7hQBR3L/Mt/c1Vx80upEj6IiwtaBepOw+s7W
pnXG8s7PYKj3i37KDGLKf1+lEY7rd3sP3RFrModq64IpnirFHX2p7xQfU8MicEv2
ESjD2hvIXLto9NUPqDJWe7wqFgjuGhZ7FsR6UilX9pjRZEFPWPuh1x9L46plf0qD
YP2QnWgztYVYw31s9ktjW6yBXhHAp8f75jn0l+SZXluA44N5oPkjBQmzhAvZXenT
kOPphFao1Zgi6MlRiI/U
-----END CERTIFICATE-----Again you can copy/paste PEM data into our PEM Decoder over at Report URI:
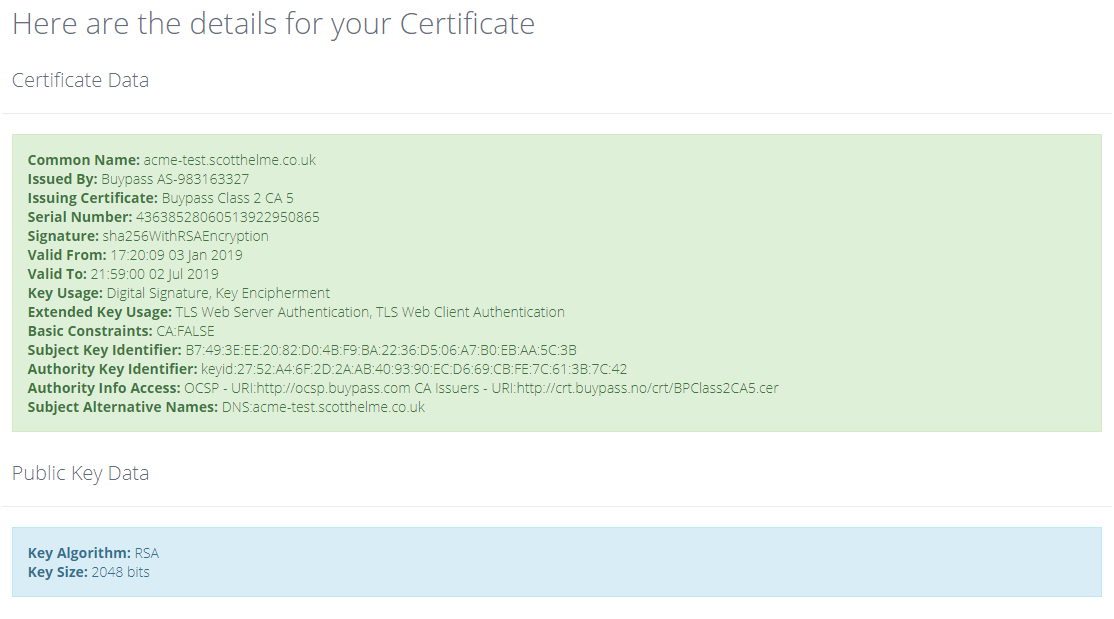
You can also see these certificates in CT on Censys and Crtsh to see that these certificates definitely do exist and were issued by Buypass.
Using acme_tiny
I've also covered acme_tiny in a few blog posts up until now but sadly getting acme_tiny working isn't so easy. The Buypass ACME API endpoint isn't actually fully compliant with the spec and while other clients can tolerate that and still function, acme_tiny can't. I've raised this with Buypass and I'm hoping they will update their endpoint to be fully spec compliant to really open up the possibilities of using any client you like.
Looking to the future
Whilst Buypass is a slightly limited backup option, it's still a backup option and it might be the only one right now. If you are using an ACME client to get Let's Encrypt certificates it's worth checking out if you can get a Buypass certificate so that you know if it will work should you ever need it. Looking forward into 2019 I think we need to see better support for ACME across the ecosystem. Just imagine a world where you could call your certificate renewal command and point it at any one of a dozen different CAs. Sounds great, doesn't it?
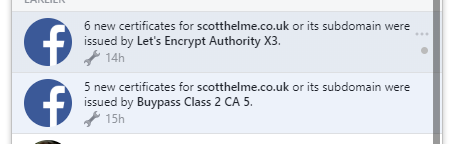
Update: The CAA value for this CA is buypass.no.
