Distributed Denial of Service (DDoS) attacks have gained fame in recent years after becoming an effective tool for hacktivist groups such as Anonymous and LulzSec. What exactly are these attacks, how are they carried out and how can websites hope to defend themselves against such assaults?
Introduction
DDoS attacks have been at the very epicentre of many cyber attacks in recent years, against some quite sizeable and influential organisations too. Mastercard and Visa, PayPal, SOCA and the UK IPA have all been subjected to, and crumbled under, the strain of a DDoS attack. Even today as I publish this blog the PlayStation Network and Microsoft Xbox Live have been knocked offline by a huge DDoS attack. I'm slightly reluctant to call it hacking because there isn't really much skill involved. To successfully carry out a DDoS attack the target site doesn't need to be compromised from a security standpoint. There are many forms of Denial of Service (DoS) attacks, a DDoS attack is simply a denial of service attack that is launched from multiple locations simultaneously. In essence a DoS attack is any form of action that intentionally renders a service unusable or inaccessible. A simple example of a DoS attack would be someone repeatedly calling your phone number to prevent you making outbound calls. The attacker is denying you the use of your phone service. To upgrade the attack to a DDoS attack would require several people to repeatedly call your phone. This distributes the attack and makes it more effective as you're even less likely to be able to use your phone now.
Launching a DDoS attack
Web servers are generally incredibly powerful computers with substantial amounts of bandwidth to the Internet. This allows them to serve requests from thousands of visitors without suffering a degradation in their service. Web servers are often located in data centres which are large buildings, purpose built for containing huge amounts of web servers. One of the simplest forms of DDoS attack is to successfully overload a web server with enough traffic to use up all of the available bandwidth. This is known as a Resource Exhaustion Attack and is what I will be taking a closer look at.
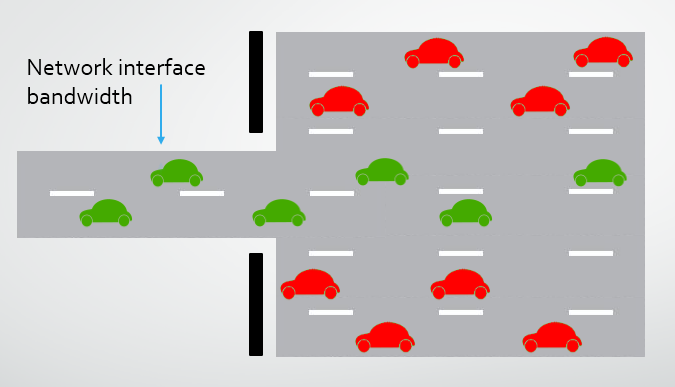
Imagine a car park for a large shopping centre. It's capable of handling 10,000 vehicles per day entering and leaving with very limited disruption, this is the web server. At any given moment only a small hand full of cars would be using the entrance, the network interface, but over the course of the day it is capable of meeting the requirements of a substantial number of vehicles, the traffic. If all of these vehicles were to arrive at the same time in the form of a huge traffic surge, then they simply wouldn't be able to fit through the entrance, the bandwidth of the network interface is saturated. The only difference now is that whilst the vehicles would sit in the queue, a packet will be dropped and then re-sent until it either makes it through or the connection attempt is abandoned. An effective DDoS attack requires the ability to generate huge amounts of sustained traffic to maintain the congestion at the network interface. If the network adapter has 10Gbps of bandwidth and an attacker can send 10.1Gbps, it doesn't matter what defences are in place, the traffic simply can't fit down the route and the service becomes unavailable for an increasing proportion of the traffic. Let's take a look at some of the methods attackers use to generate these huge amounts of traffic.
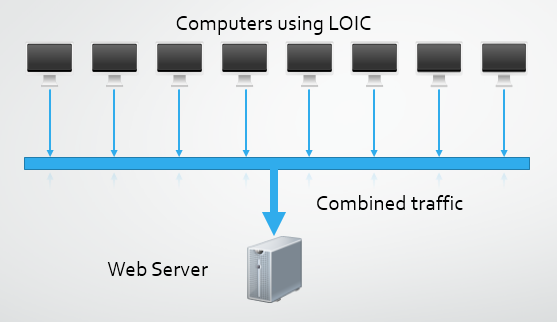
Low Orbit Ion Cannon (LOIC)
LOIC is a tool made famous by hacktivist group Anonymous and allows a user to "stress test" their network by launching a DoS attack. There is nothing illegal about owning or even using LOIC in the right circumstances, you can download it for free over on SourceForge. A network administrator or systems architect may have perfectly valid reasons for wanting to load test their infrastructure. Load testing and performance testing create useful metrics in determining exactly what your hardware is capable of and allows for accurate expansion planning. But hey, who are we kidding, take one look at a LOIC and it's fairly obvious what its sole purpose is! LOIC allows an attacker to create a voluntary botnet of users prepared to dedicate their resources to the attack. I'm going to cover more on botnets a little further on but they're basically huge collections of computers dedicated to a single task. There is even a JavaScript version of LOIC that can be run directly in your browser so nothing needs to be downloaded or installed. A large collection of several thousand people can launch a fairly sizeable DDoS attack by dedicating their upload bandwidth to an attack. A modest collection of 5,000 users with a typical upload in the UK of 1Mbps could easily sustain 2.5Gbps per second of traffic (assuming ~500Kbps sustained upload). That does sound like an awful lot of traffic when compared to what you're used to at home (at least here in the UK), but it's only going to be enough to slightly impact performance on most large targets and perhaps not even do that on some.
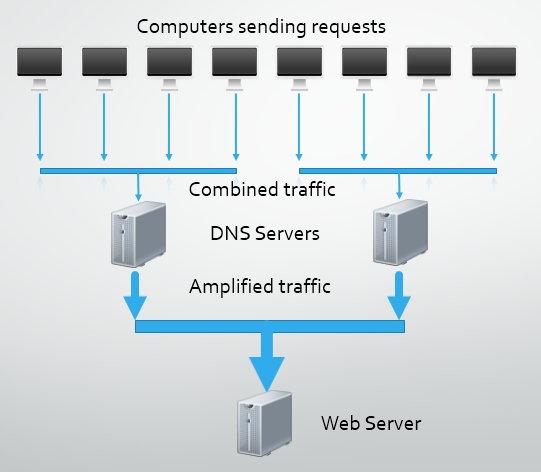
DNS Amplification
One of the responsibilities of the Domain Name System (DNS) is naming resources connected to the Internet. Most importantly, DNS is used to translate a domain name, like google.co.uk, into an IP address for the server hosting it, like 62.24.154.88. When you type any domain name into your browser a request is sent to a DNS server to resolve the domain name into an IP address. The browser then requests the resources from the hosting server using its IP address. Go ahead and try any of the following IP addresses:
62.24.154.88 62.24.154.89 62.24.154.98 62.24.154.99
These are all IP addresses used by Google's servers and when input directly into your browser you skip the need to perform a DNS lookup. This is the address your browser navigates to behind the scenes when you type google.co.uk into your address bar.As DNS requests are made using UDP there is no handshake between the requesting user and the server receiving the request, UDP is a 'fire and forget' protocol. A user makes the request without verifying if the server is present and waits for a response. Similarly the server receives the request, processes it and responds using the details in the request without verifying if the user is still there. This lack of handshake between the server and client allows for details in the packet to be forged. A malicious user can issue a request to a DNS server and insert a fake source IP, the IP of their target. When the DNS server receives the request and processes it, it will send the response to the source IP address, the IP of your target. This form of attack is very useful because a request to a DNS server can be as small as 60 bytes yet the response could be 4,000 bytes, almost 70x larger. This allows the attacker to take their 500Kbps of upload bandwidth and amplify it to around 35Mbps of bandwidth. This would take our theoretical attack force of 5,000 computers to 175Gbps of sustained traffic. Now we're getting into serious territory with a considerable tidal wave of potential traffic to flood the host web server with.
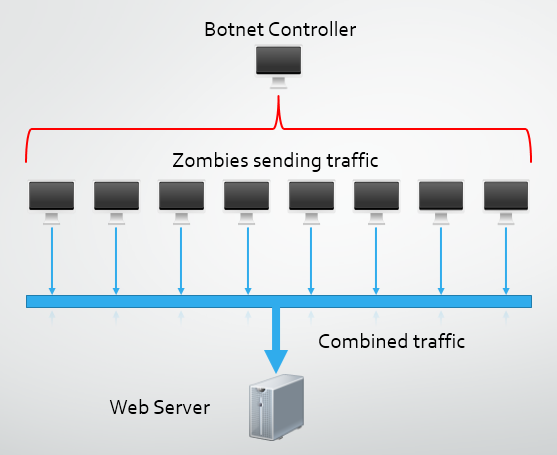
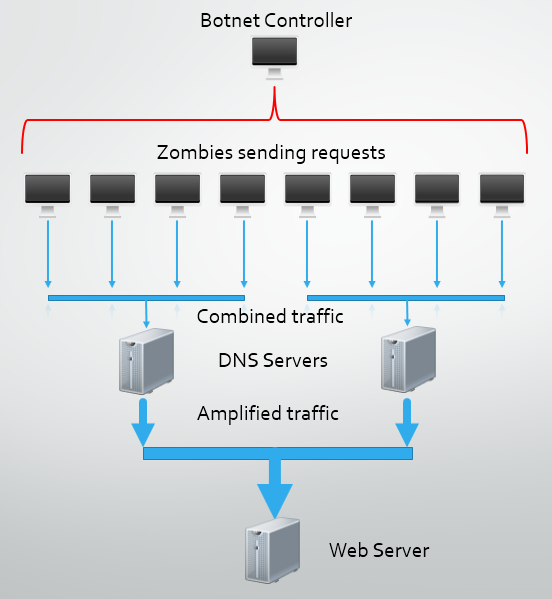
Botnets and Zombie Computers
A botnet is a large collection of computers that have been infected with some form of malicious software that allows an attacker to control them. A botnet controller can use all of the computers, or zombies, they have access to for carrying out tasks like sending spam emails or launching a DDoS attack. The controller can use a similar method to LOIC and flood the target with traffic using the internet connection of the zombie, or coupled with some research to locate open DNS resolvers, can use DNS amplification to increase the power of the attack. The main difference with a botnet is that participants in the attack are not doing so voluntarily or knowingly. Their computer has been taken over and utilised by a cyber criminal without their knowledge.
Web Server Hijacking
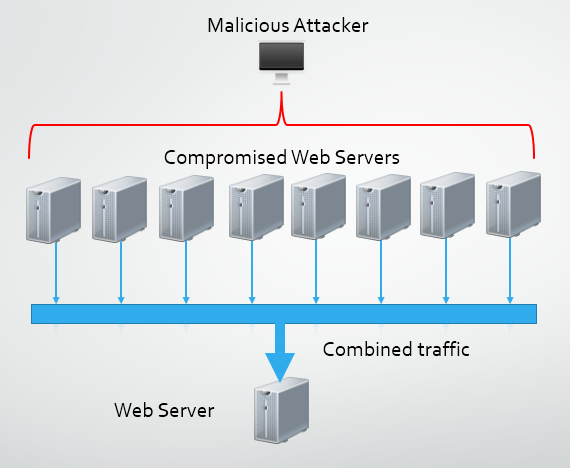
Traditionally, a DDoS attack is comprised of anything from a few thousand to a few hundred thousand computers using any of the above mentioned methods to attack a web server. Another attack vector that has been identified is to compromise web servers themselves to utilise in an attack. Web servers are generally very powerful machines with large amounts of Internet bandwidth and are ideal candidates for use in a DDoS attack. The main problem is they are much more difficult to compromise and take control of in comparison to a standard computer. A typical web server can have as much as 100x the bandwidth of a residential Internet connection, so where available, they make a great addition to a DDoS attack force. There are documented cases of DDoS attacks being launch solely from web servers that have been exploited with vulnerabilities. As few as 300 web servers were all that was needed in comparison to the thousands of computers that would have been required. My own blog was hit by a DDoS attack that utilised compromised webservers.
The purpose of DDoS Attacks
Right now you might be thinking that any of these methods of attack seem like a whole lot of trouble and they could land you in an awful lot of hot water with local law enforcement. So what's the point?
Ideology
Political motivation is the most widely recognised factor behind almost all of the recent high profile DDoS attacks. 'Hacktivists' use DDoS attacks to assault the websites of large organisations and government agencies involved in controversial activities as a symbolic gesture of defiance in taking them down. In 2010 Anonymous attacked the servers of several credit card companies for suspending payment processing to WikiLeaks, an organisation that publishes secret information leaked from governments. WikiLeaks itself has also come up against similar attacks.

Distraction
Once a site is targeted by a DDoS Attack, it's a safe bet that the system admins or security response team are going to be devoting their efforts towards mitigating the attack and keeping the servers from going down. This tactic has been used in the past to distract the security response teams of some banks whilst fraudulent transactions were carried out. Get the attention of your target with a DDoS and then sneak in the back door while they're not looking.
Extortion/Competition
The threat of using a DDoS attack against companies that depend heavily on their web presence, or like an ISP are purely based on their Internet serivces, is incredibly serious. As recently as August 2013 cyber criminals have been using the threat of DDoS attacks to blackmail companies into paying up. Smaller companies may not have the ability to mitigate a serious DDoS attack and involving law enforcement isn't going to result in an expedited resolution. A successful DDoS attack could result in serious harm from lost revenue and damage to the companies image. Even if no financial demands are made, launching a DDoS attack against a competitor could prove to be beneficial.

Exploitation
A DDoS attack can be used as an effective means to make a system more vulnerable to being compromised. If a primary line of defence is overwhelmed, such as a load balancer or firewall, and it fails, it could leave the systems behind them exposed. This is known as a Fail Open scenario. When the device or service fails, it can either shut down communications or allow them to continue, depending on its configuration.
Whilst under a sustained DDoS attack a host may decide to bring secondary assets into play to help deal with the increased load. These could be additional servers to handle load or additional network routes to allow greater bandwidth. Generally such backup plans are well devised and secure, but on short notice or created in a hurry, they may present opportunities for an attacker.
During a DDoS attack as systems are overwhelmed they may crash and restart or intentionally be restarted in an effort to bolster defences. Whilst these windows of opportunity may be small, a keen attacker will find them and utilise them whilst sustaining the DDoS attack.

Mitigation
Whilst DDoS attacks aren't very complex, in fact they're actually an incredibly simple flood of useless traffic, they are difficult to defend against. Depending on the scale of the attack they can actually be impossible to mitigate and this is regularly the case. Sometimes there is even collateral damage. Fortunately there is something that we can do to defend against DDoS attacks, spread the load!
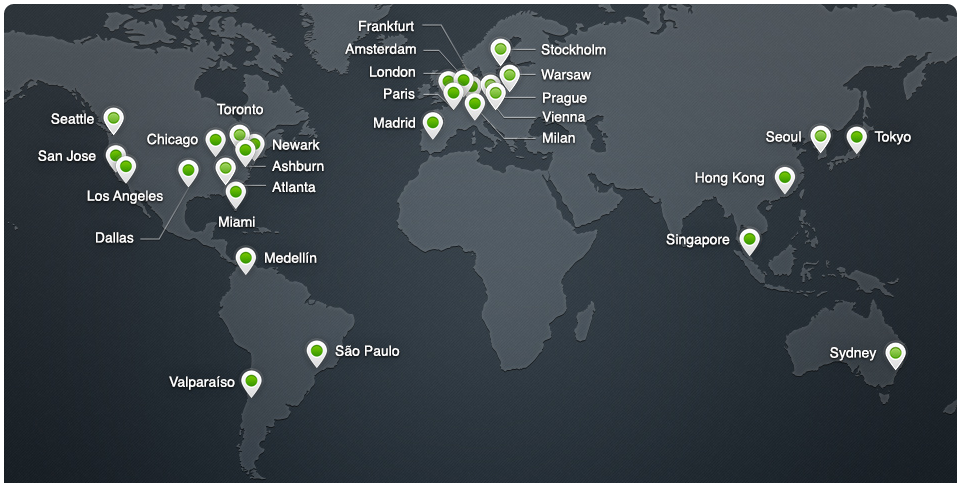
CloudFlare is a Content Delivery Network (CDN) with some advanced features. A CDN helps alleviate load on your web server by serving content on your behalf. This releases resources on your server to focus on more important tasks. CloudFlare has 28 data centres located all around the world and each one broadcasts the IP address of all 28 data centres using Anycast. This means that no matter where you are located in the world you will always be routed to the closest data centre resulting in the fastest possible connection. Using a CDN results in reduced load on your server to free up resources for handling a larger scale attack.
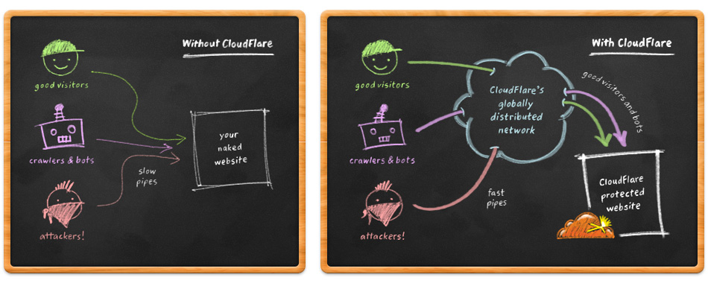
CloudFlare also acts as a reverse proxy. Not only does it serve and cache content at its 28 data centres but all requests to your website pass through CloudFlare's network, which requests content from your server on behalf of the user and delivers it to them. This offers various security and performance enhacements covered on their site, but so much so that hacker group LulzSec used CloudFlare to protect their own website when it came under attack. Because CloudFlare handles all requests on their way to your site, they can analyse the traffic and filter out malicious requests. By filtering out traffic upstream, before it even makes it to your server, CloudFlare slows down the rate at which your server resources are consumed when you're under attack. As the CloudFlare network protects thousands of websites, they are regularly under attack which gives them plenty of opportunity to learn about attacks and how to defend against them. Because they use Anycast at all of their data centres it is physically impossible to single out a specific data centre to attack. A geographically diverse botnet, or group of open DNS resolvers, will end up targeting their local CloudFlare data centre and their overwhelming traffic surge will be broken into smaller, more manageable streams. Even if an attacker did succeed and managed to take a data centre down, it would simply stop broadcasting its IP addresses. As soon as that happened, traffic would automagically be routed to the next nearest data centre which is broadcasting all the same IP addresses. CloudFlare effectively use Anycast as their own load balancing device.
Last year we saw what was the largest DDoS attack in history at 300Gbps, but less than 6 months on that has already been smashed by another DDoS topping 400Gbps. Alongside services like those offered by CloudFlare, organisations like the Open Resolver Project aim to reduce the weapons in an attackers arsenal by cleaning up open DNS resolvers used in attacks. For now, it is possible to pretty much counter a record breaking DDoS attack but the protection isn't going to come cheap. CloudFlare Enterprise accounts start at $2,000 a month. A sluggish site and a few dropped connections seems like a much better prospect than your server being knocked over and taken offline though. Even their free accounts will help mitigate a DDoS attack as they reduce the load placed directly on your server, though as you move up through the paid accounts the protection does get much, much better.
