I have a couple of subdomains on scotthelme.co.uk to show how good a TLS config can be and how bad a TLS config can be and still not attract any warnings in the browser. I'm now adding a third subdomain to demonstrate what happens when your HPKP policy is violated.
HTTP Public Key Pinning
HPKP policy is delivered via a HTTP response header and allows you to define a whitelist of certificate fingerprints that the browser should accept for your site going forwards. Even if an attacker managed to get hold of a valid certificate for your site, say from a compromised Certificate Authority, the browser would reject it. To read more on HPKP, you can check my previous blog HPKP: HTTP Public Key Pinning. This covers HPKP in much more detail and has a guide on how to set it up. For now, on with the demonstration!
The subdomains
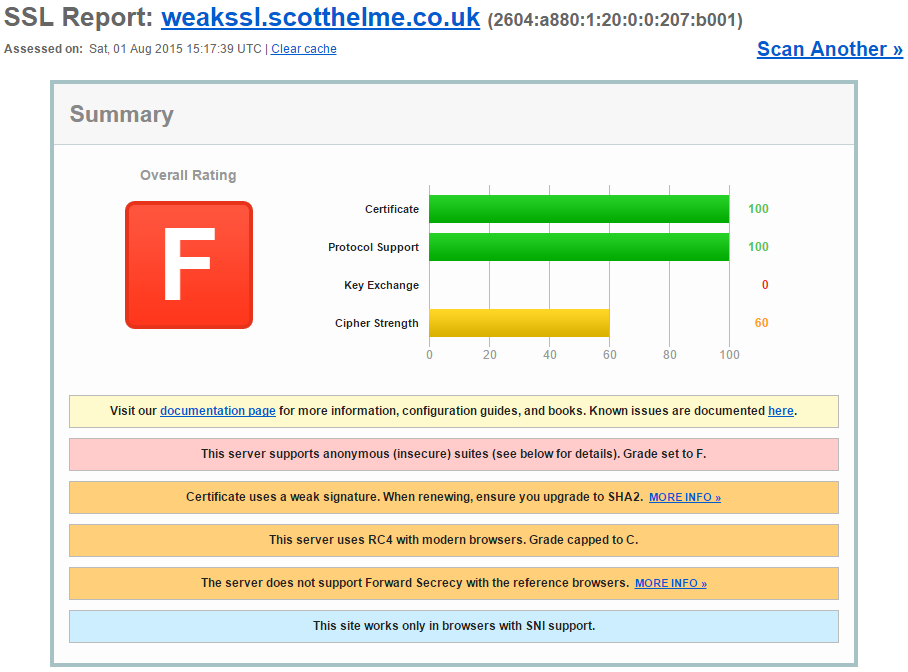
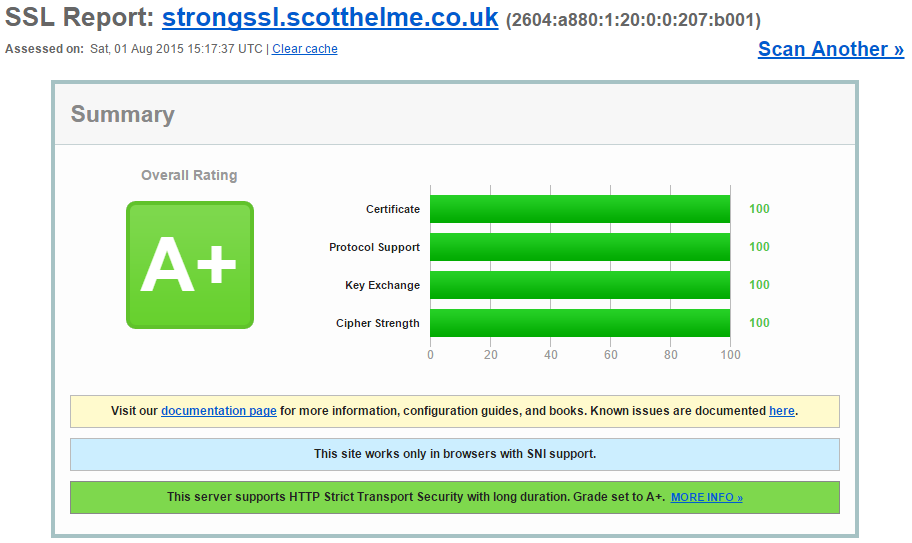
I have two existing subdomains on scotthelme.co.uk and they are https://weakssl.scotthelme.co.uk and https://strongssl.scotthelme.co.uk/. As you can probably guess, they're examples of the worst possible SSL/TLS config you can have without attracting any warnings from the browser and the best possible config possible to see if your browser is compatible.
weakssl.scotthelme.co.uk
strongssl.scotthelme.co.uk
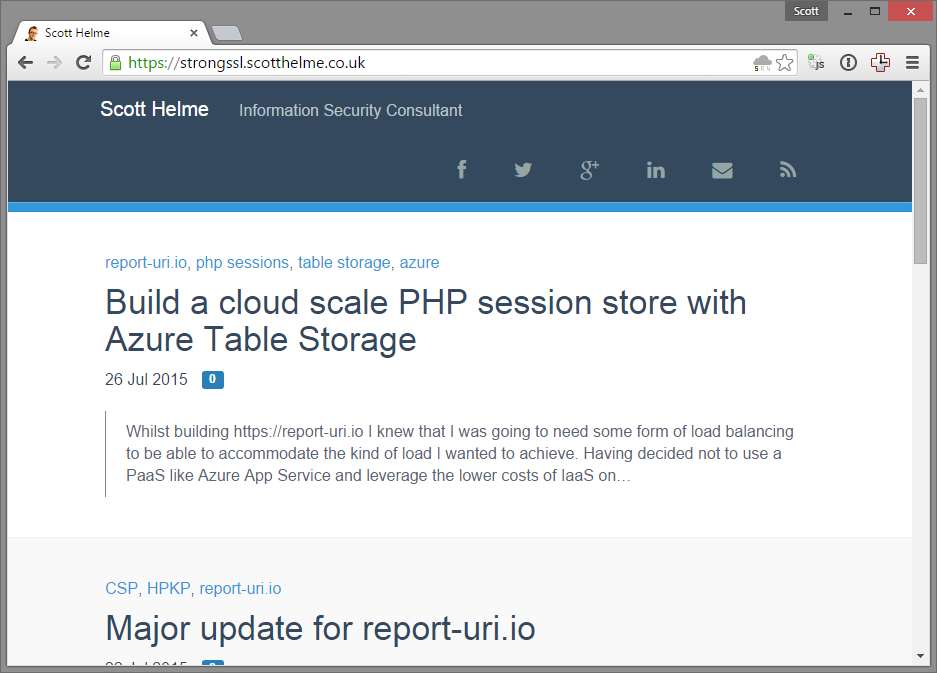
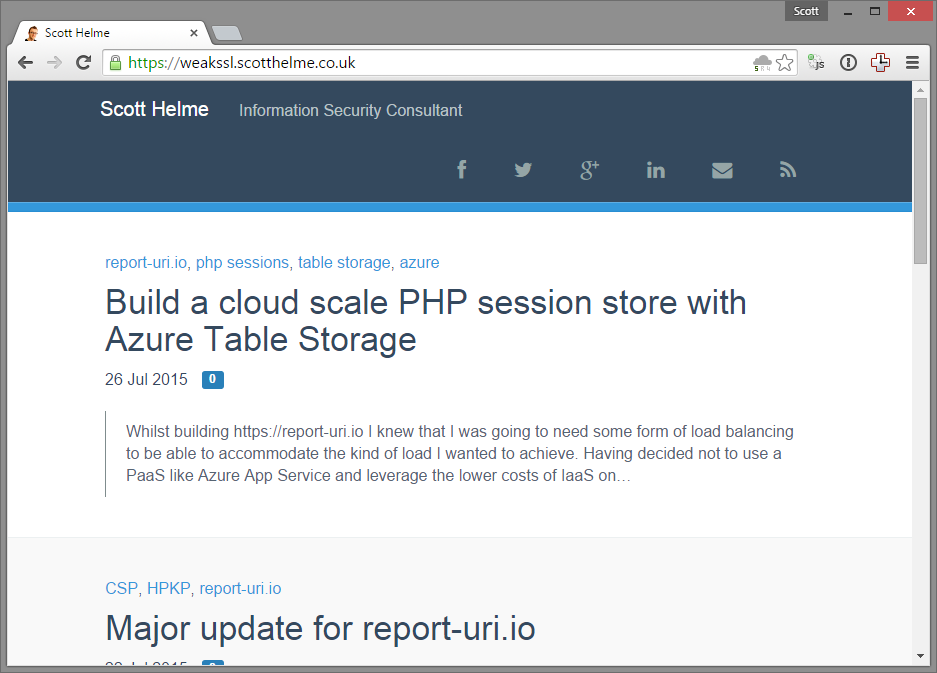
Introducing hpkp.scotthelme.co.uk
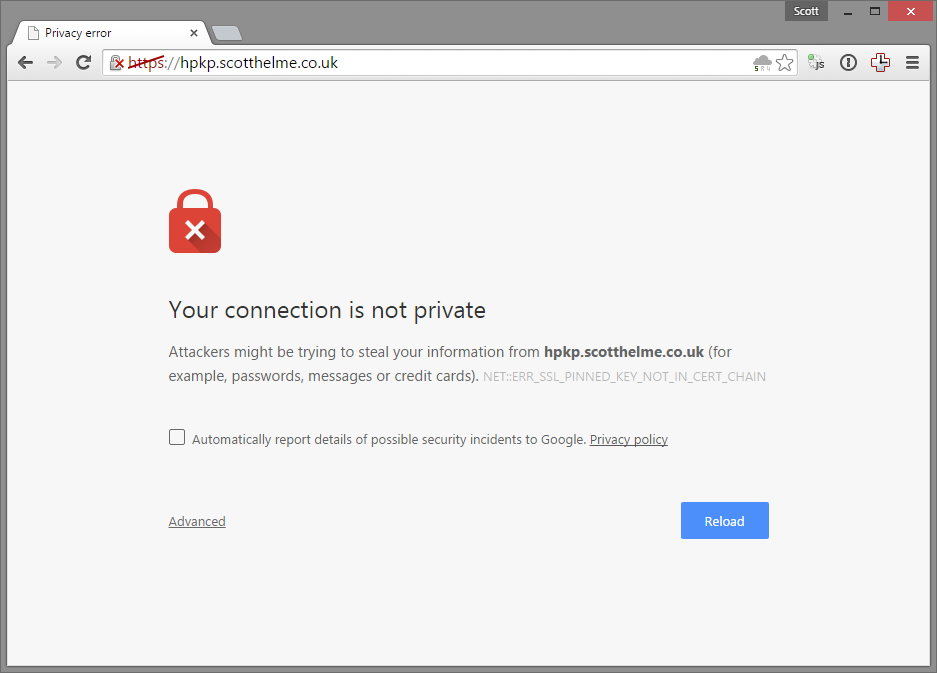
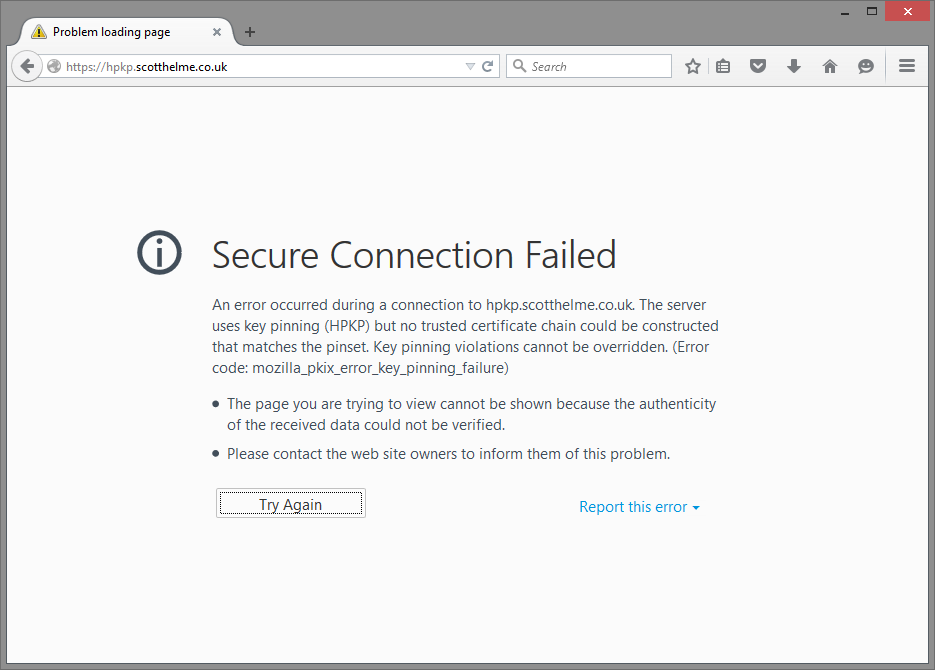
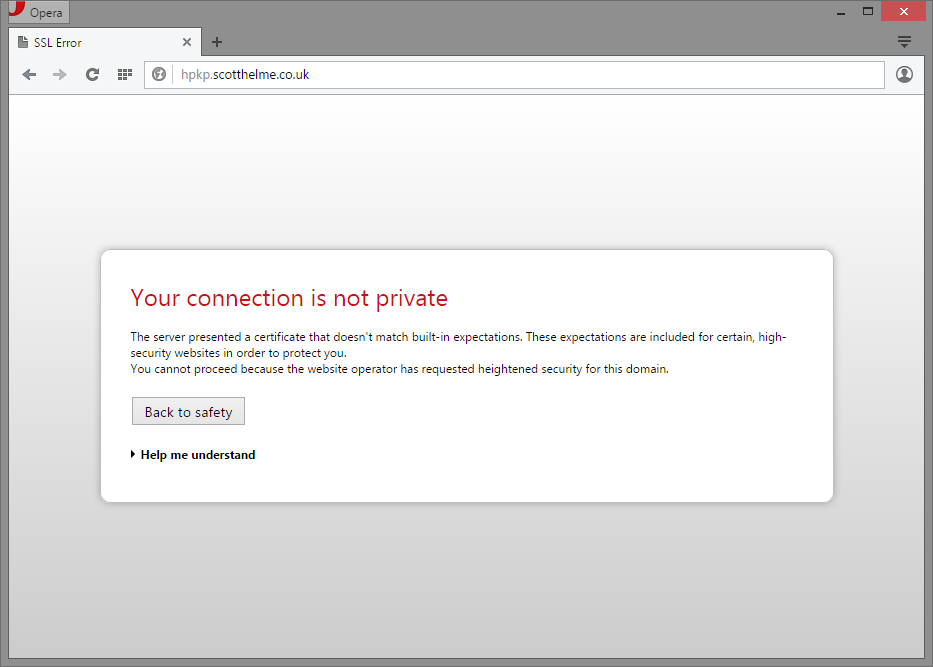
My new subdomain, https://hpkp.scotthelme.co.uk, is designed to show you what a pin validation failure looks like if you use HPKP and things go wrong. I'm forcing this failure as the certificate I'm using on the subdomain is not in my site-wide HPKP policy. The certificate on the subdomain is perfectly valid. You can inspect it and see that it's for the correct domain, it's issued from a trusted authority and we're within the validity period stated on the certificate. That said, despite the fact that everything checks out just fine and the browser would normally accept this certificate, the browser is refusing to load the site. This is the very essence of HPKP at work.
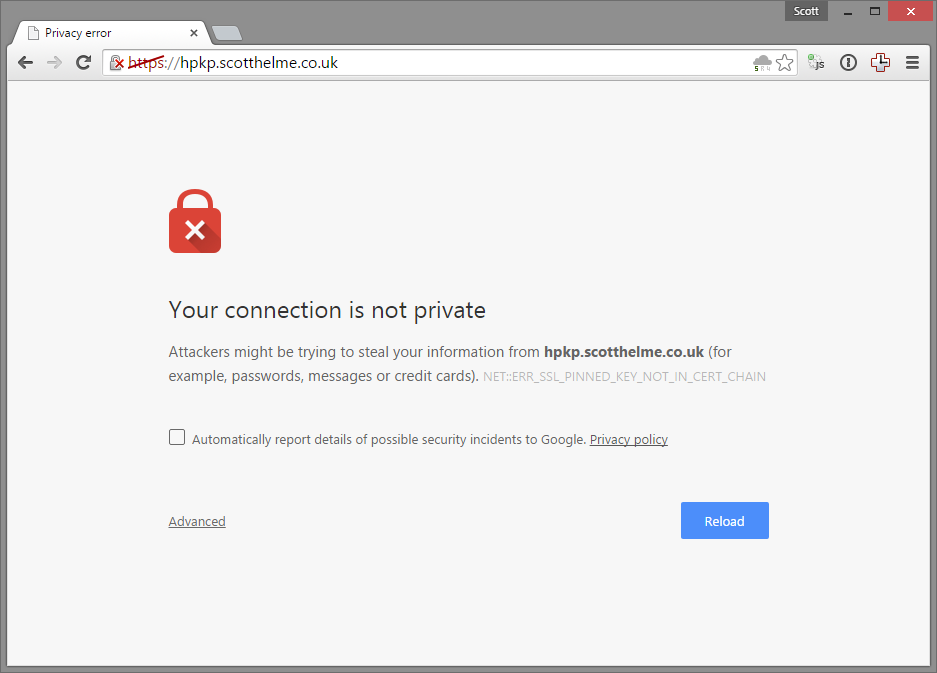
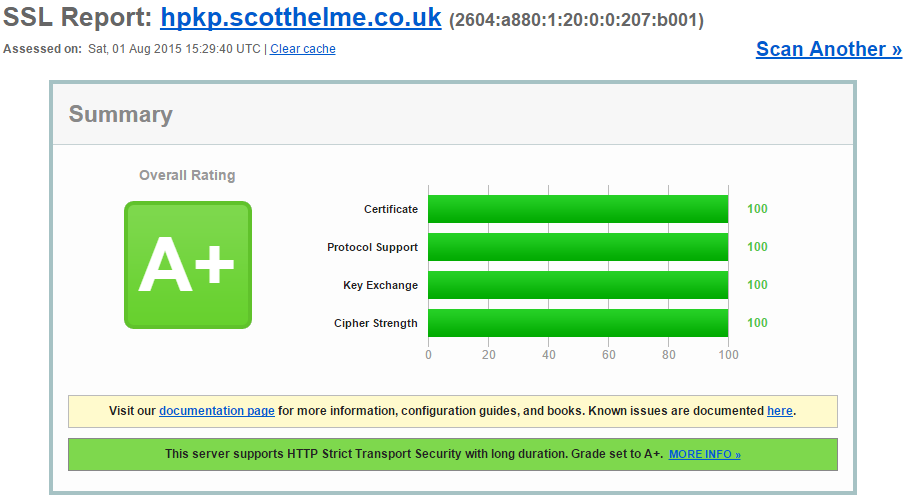
Just an extra assurance, everything checks out perfectly fine on the Qualys SSL Test too. There is literally nothing wrong with this certificate, it is perfectly valid, but your browser should not accept it!
HPKP Support
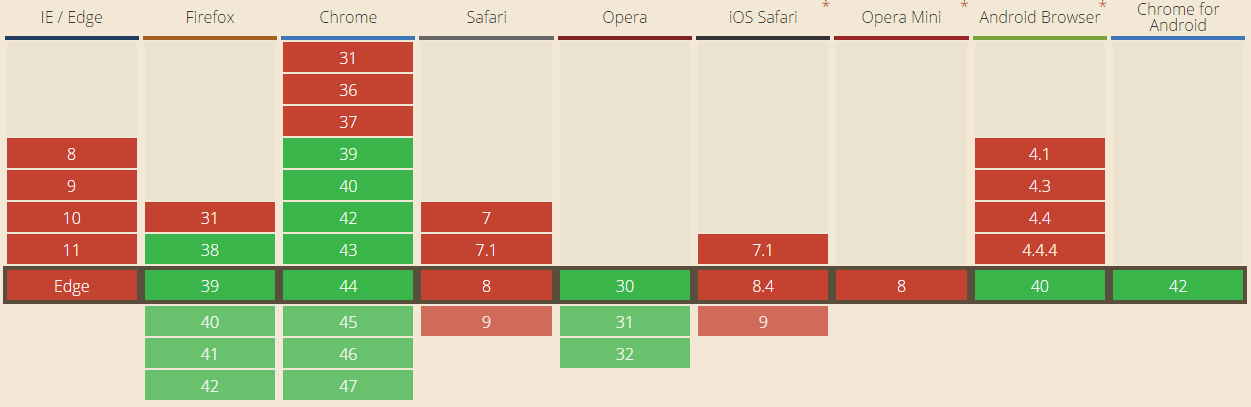
All good browsers support HPKP:
Chrome
Firefox
Opera
Internet Explorer
Safari
If your browser can load https://hpkp.scotthelme.co.uk after you've visited this page, or any other page on my site for that matter, it doesn't support HPKP. You can get more details on which browsers support HPKP over at Can I Use?.