It's finally happening! We've had 2 failed attempts through the CA/B Forum and now Apple has decided to enforce a maximum lifetime of 398 days on certificates issued from 1st Sep 2020.
Previous attempts to reduce to 1 year
The 2 previous attempts to reduce certificate lifetimes to 1 year came with Ballot 185 in Feb 2017 and then Ballot SC22 in Sep 2019. You can read all of the details on both of those in my blog Ballot SC22: Reduce Certificate Lifetimes, but in both ballots the support from CAs was poor whilst the support from browsers reached 100% in the second ballot.
With 100% support from the browsers in the second ballot there was a clear sign that they wanted this, and with very good reasons too. I have a blog post going back 2 years on Why we need to do more to reduce certificate lifetimes so if you're interested in some of the reasons then you can check them out there, but there are some very good reasons that have only become more important over time.
Back in September when Ballot SC22 failed, I made the following comment in my closing paragraph of the blog post.
All in all, this process really highlighted some of the issues we have in this ecosystem and just how deep they run. The browsers tried to change this twice through the forum and if I were a gambling man, my money would be on the 3rd attempt being taken elsewhere.
It now seems that my prediction has come to pass!
Apple to enforce a maximum lifetime of 398 days
The CA/B Forum met in Bratislava this week and at that meeting, Apple announced their plans to enforce a maximum lifetime on TLS certificates of 398 days. Any new certificate issued from this date can only have a maximum lifetime of 398 days or it will not be accepted as valid by Apple in applications like Safari. With Safari hovering around 18% of the browser market share, they're definitely big enough to enforce a change like this on their own, but I fully expect other browser vendors to follow suit with their own requirements and signal their support for Apple. This change will not impact any existing certificates so there's no need to panic, you will simply only be able to obtain 1 year certificates from Sep 1st 2020.
How big will this change actually be?
Looking at my data from Crawler.Ninja I can see the certificate validity periods for the certificates in use across the top 1 million sites on the Web.
| Validity period (days) | Number of sites |
|------------------------|-----------------|
| 1-398 | 394,758 (75%) |
| >398 | 133,930 (25%) |Of the sites presenting certificates to the crawler, 25% of those sites will need to renew with a shorter certificate from 1st Sep 2020 as they're currently using one longer than the 398 day maximum. It's not just me looking at this either, Paul Calvano did an analysis using a different data set from HTTP Archive and came back with the exact same 25% figure for certs that will be too long!
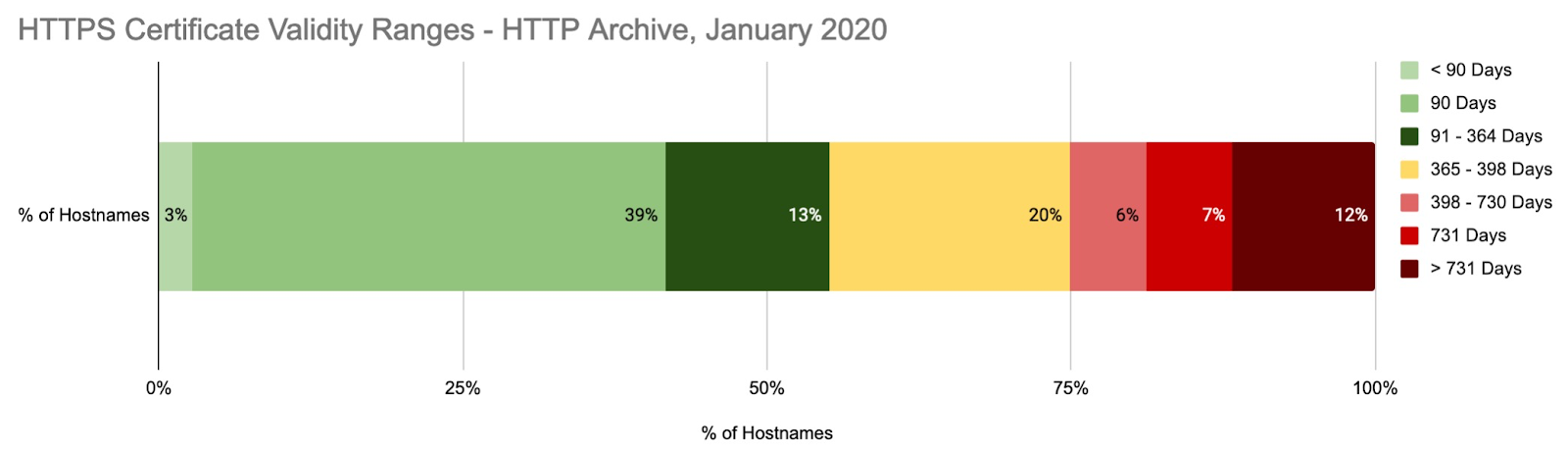
That data covers over 5 million websites so it's nice to see my findings backed up by other independent work. It seems quite a few people will be in for a surprise come Sep 2020 if they still want their longer certificates! I will keep an eye on this number over the months leading up to the change and then in the months following to see how soon the industry shifts to 1 year certs.
TLS Training
If you enjoy learning about TLS/PKI and would like to spend some real time getting hands on then don't forget to check out the 2 day TLS/PKI Training Course that I deliver. We cover a lot of the reasons why shorter certificates are better, get to grips with using automation via CAs like Let's Encrypt and it's a really hands-on, enjoyable course.
Useful links and info
Michal Špaček also covered this topic in Maximum HTTPS certificate lifetime to be 1 year soon.
DigiCert published their Position on 1-Year Certificates.
Paul Calvano and his analysis with HTTP Archive data Certificate Validity Dates.
I will update this post with links to the CA/B Forum minutes and Apple announcement when they become available.
Apple announcement About upcoming limits on trusted certificates.
