Learn just how easy it is to hijack sessions over the LAN or Wifi and why using that free WiFi at your local coffee shop could cost you more than you expect!
In a previous blog post I gave a demo of session hijacking on my own PC. Whilst I only hijacked the session locally, from one browser to another, it was more a proof of concept than an actual viable attack. In this blog I'm going to demonstrate session hijacking across different clients on a network using a Man In The Middle (MITM) attack known as ARP Poisoning or ARP Cache Poisoning.
Before continuing it may be worth reading the 2 PowerPoint presentations I have created that explain the basics of Session Hijacking and ARP Poisoning in a little more detail.
Session Hijacking: HERE
ARP Poisoning: HERE
To perform the attack I'm going to be using 2 tools. The first tool, called Cain, is the Swiss Army Knife of an attackers tool kit. Alongside being able to perform ARP Poisoning attacks (which it refers to as ARP Poison Routing - APR) it can perform cryptanalysis attacks on many secure protocols, features a brute force and dictionary based password cracker, automated password stealing and much more! The second tool is Wireshark which is a fantastic traffic sniffing tool that will allow us to view the traffic of other clients on the network once they have been ARP Poisoned.
Download Cain: HERE
Download Wireshark: HERE
I'm also using the Firefox browser and the Cookie Manager+ plugin or the Chrome browser and Cookie Manager to help make things a little easier.
Download Firefox: HERE
Download Plugin: HERE
Download Chrome: HERE
Download Plugin: HERE
Important
Only ever perform the following tutorial on a network that you own. The following tutorial explains how to use tools that will interfere with the operation of your network. If you choose to use any of the information provided here, you do so completely at your own risk. You will also be accessing the data of other clients on the network. Ensure that only your own devices are connected to the network, or, you have permission from any and all clients on the network to access their data. Now that's out of the way, let's go!
Setup
Install Cain and Wireshark from the download links above. Once you have Cain and Wireshark installed you're ready to get started.
ARP Poisoning
After launching Cain you may get a warning about the windows firewall. For the most part I have found no problems with using Cain with the firewall enabled but if you do have problems with any of the steps here disabling the firewall can help. You can also launch Cain with admin privileges by right clicking the icon and selecting 'Run as Administrator'. Once Cain launches you should be at the main screen.
The first step of the attack is to identify clients on the network so click on the sniffer tab and then click the start sniffer button:
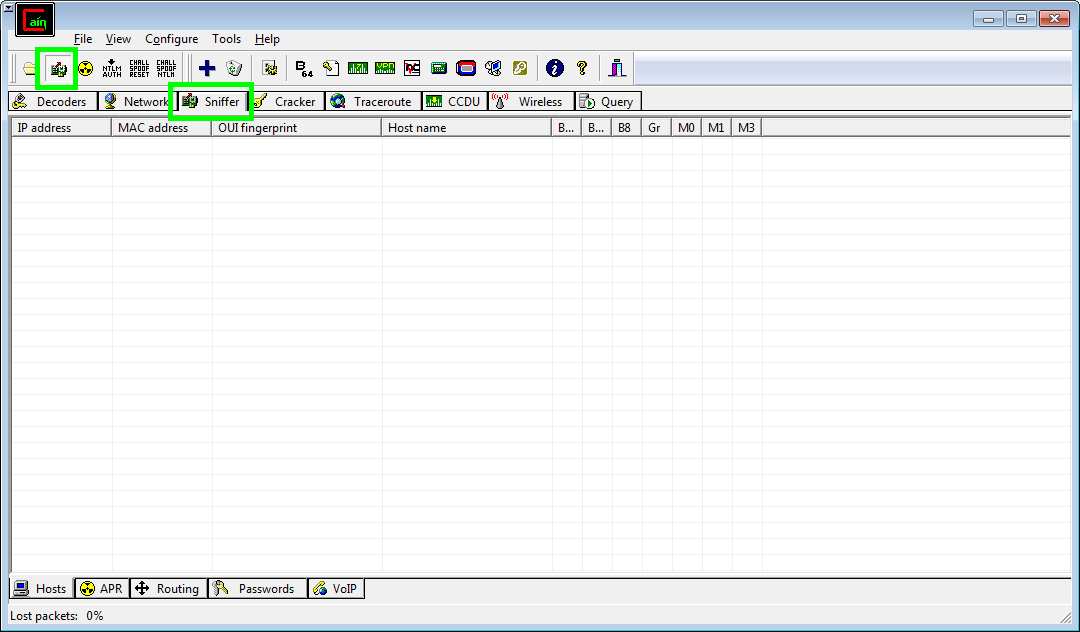
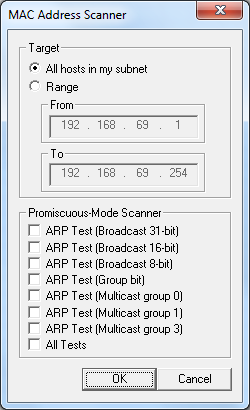
Now if you wait patiently clients on your network will slowly start appearing in the currently empty list. But enough of waiting already, we can speed things along! Right click anywhere in the empty list and hit 'Scan MAC Addresses'. Click OK in the little window that pops up and Cain will check every single IP address on your network and see who is there:
Here in my result list you can see the clients it found currently on my network:
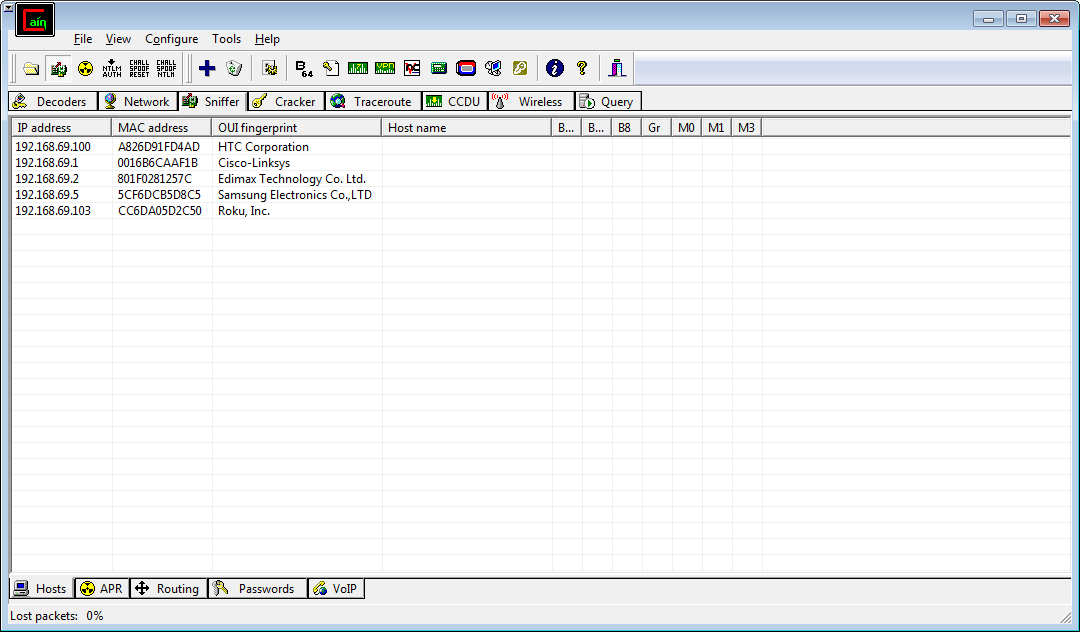
From here you determine which clients you're going to target, assuming you're not going to target everyone. It's worth pointing out that attempting to target many clients will force a potentially considerable amount of network traffic through your adapter. This could result in a performance hit on the network as your network adapter attempts to handle large amounts of traffic!
With the information above I've decided I'm going to target my own phone, the HTC device. Select the APR tab at the bottom, click anywhere in the empty space indicated and the blue plus icon at the top of the screen will be activated. This allows you to add clients to the attack, click that.
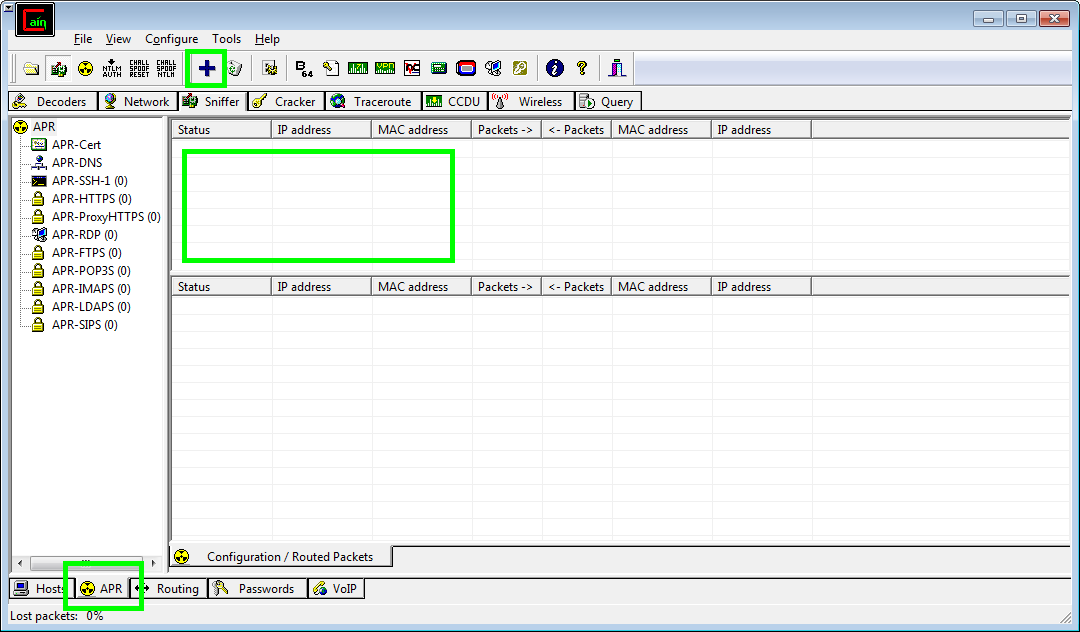
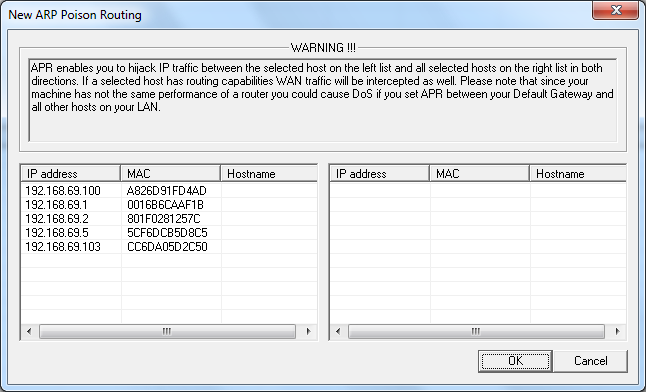
As warned again here by Cain, it may be worth just targeting a specific device on the network. I know my HTC device is 192.168.69.100 from the previous screen and I know my router (default gateway) has the IP address 192.168.69.1. If you don't know the address of your default gateway, open a command prompt and type in "ipconfig /all" and hit enter. You will get the following which will allow you to target the default gateway if you wish:
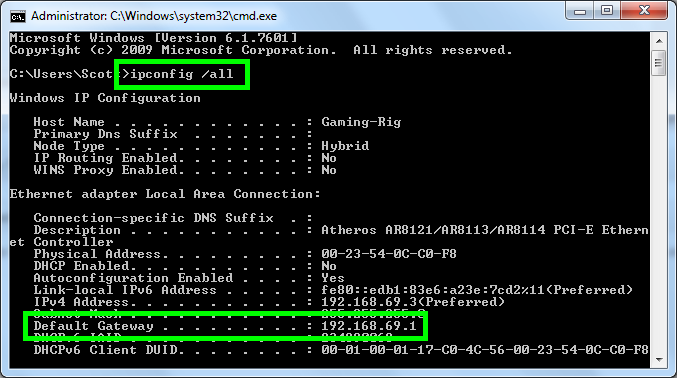
As I only wish to intercept the traffic between my phone and other clients on the network, I'm going to select the IP address 192.168.69.100 on the left and then all of the addresses that appear on the right hand side. After that just click OK:
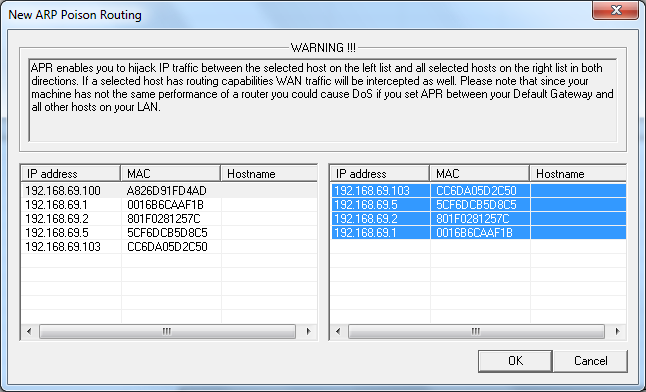
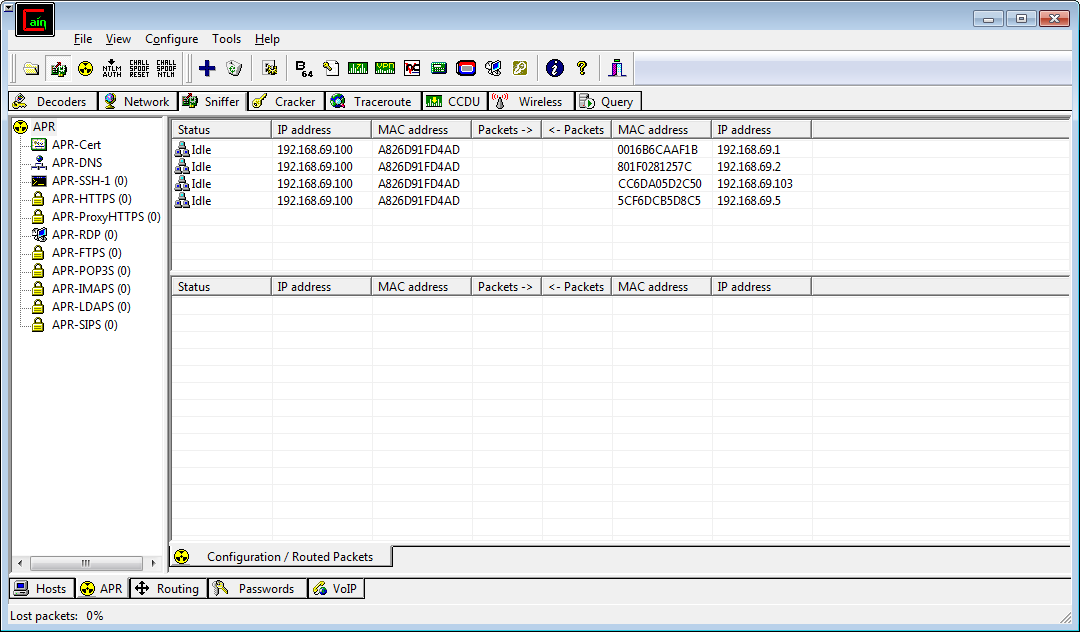
Now you can see that Cain is ready to start ARP Poisoning any traffic between my phone and any other client on my network. The most important one is the default gateway as this is where the phone will be sending all traffic bound for the Internet.
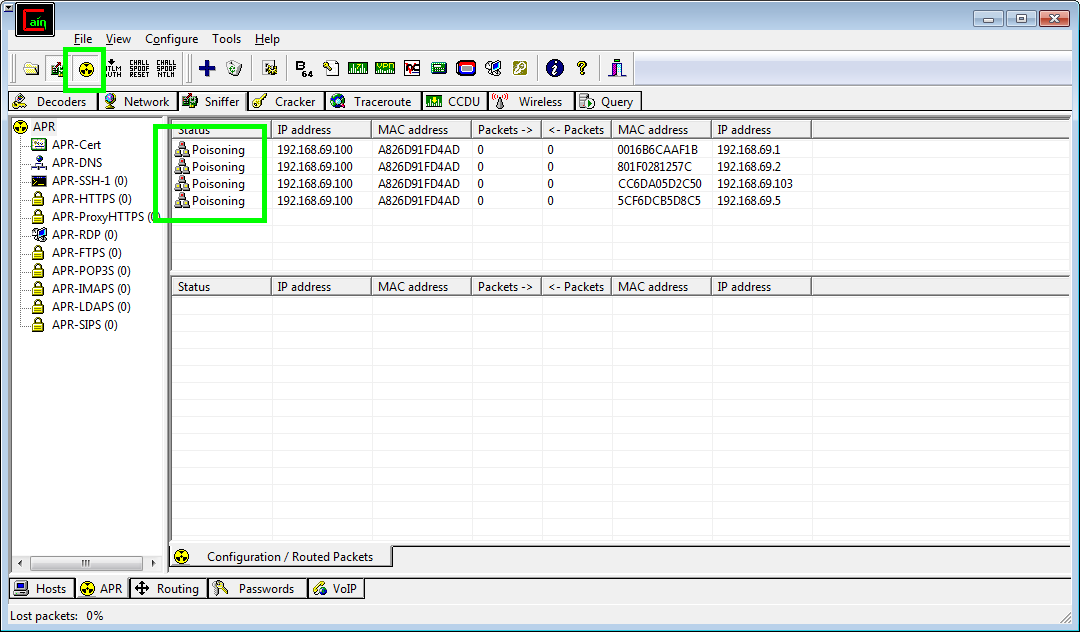
To start the ARP Poisoning attack simply hit the Start APR button at the top of the window and watch Cain begin to work!
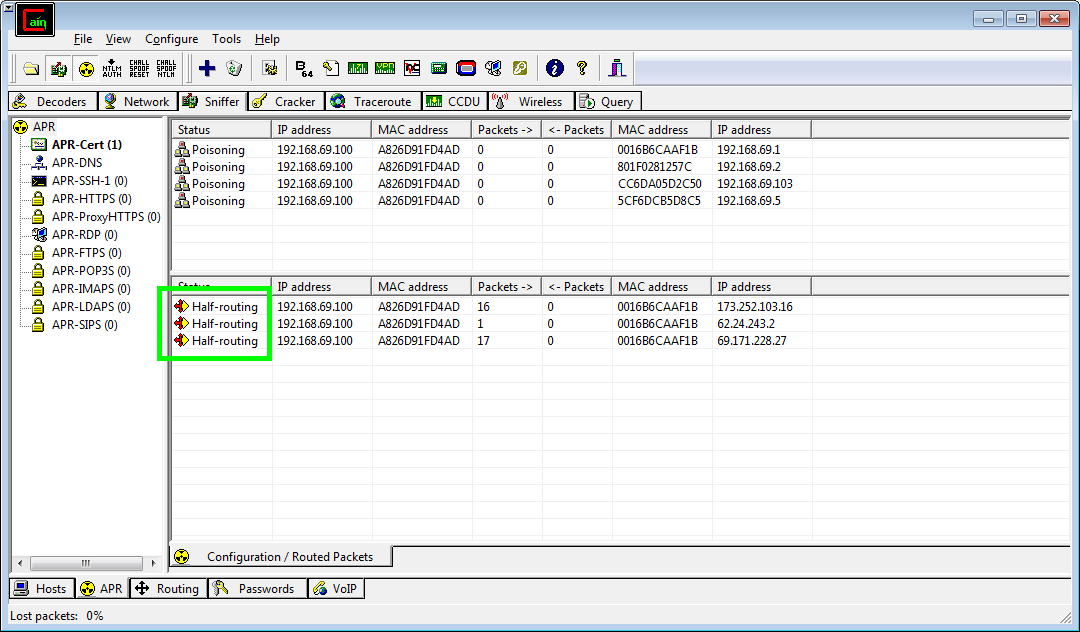
As Cain begins to work you will see the traffic being routed via you in the window at the bottom. Half-routing means Cain is currently working on getting all of the traffic and Full Routing means you have unrestricted access to the traffic going to and from the device!
Gotcha!
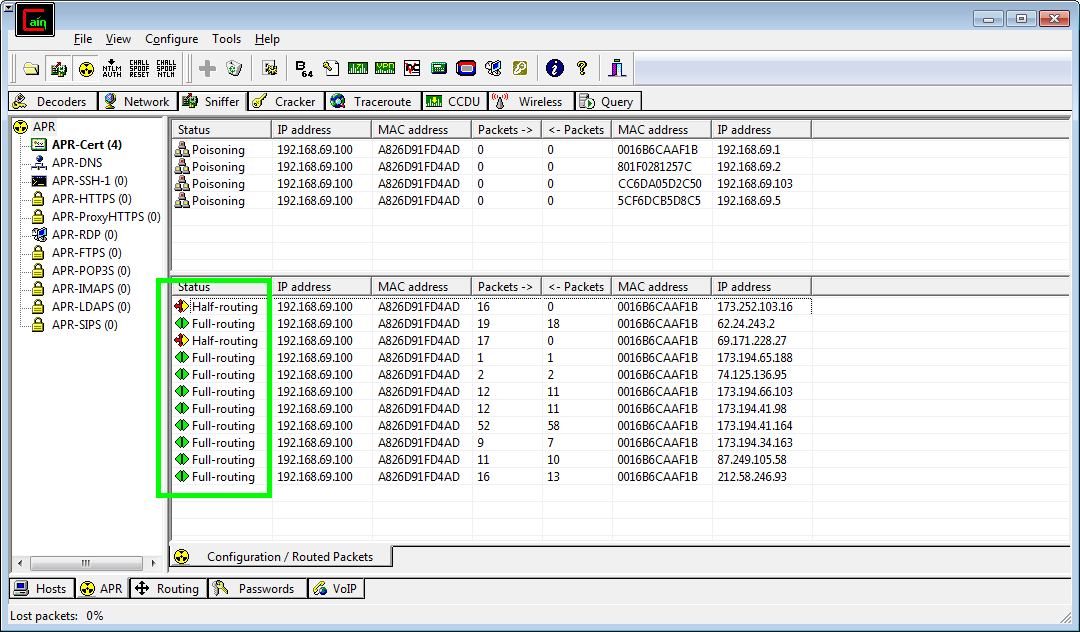
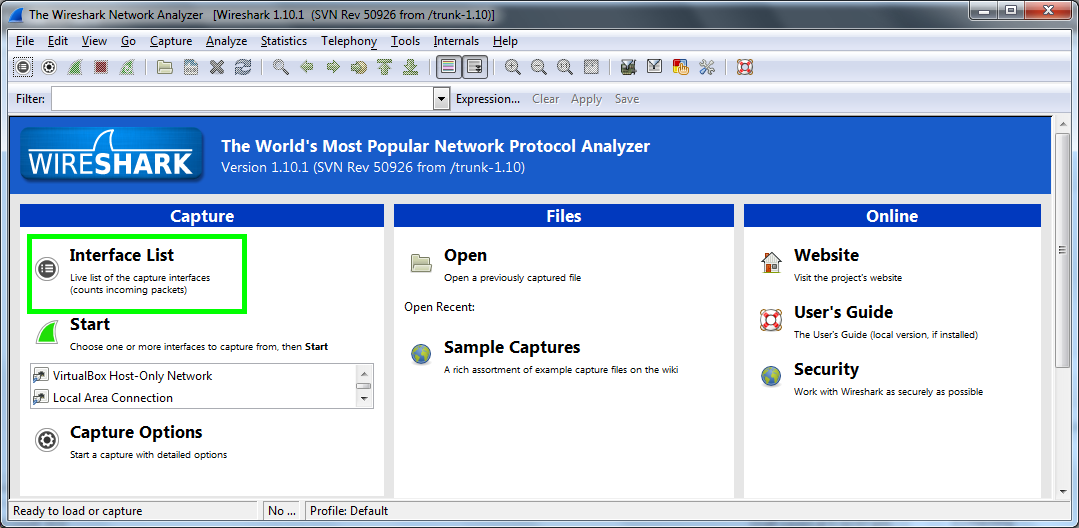
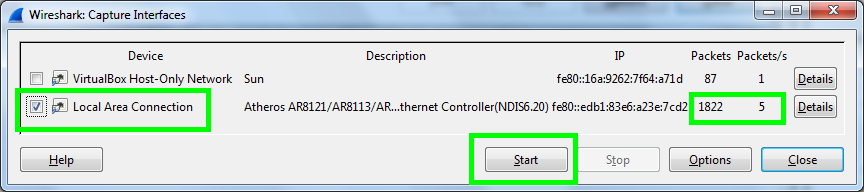
At this point all of the traffic sent from my phone is being routed via my PC before being forwarded on to the default gateway. This is where Wireshark comes in. Open Wireshark and select the 'Interface List'. In here you need to select your network adapter, there is usually only one but if there are more, it will be the one with most packets coming in and out. Then hit 'Start'.
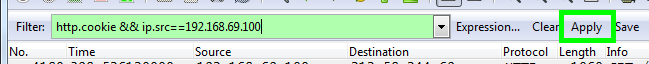
Once you start the capture you will see a lot of information flying through the list, this is normal, especially considering all of the traffic from the target device is now passing through. As we're specifically looking for a session ID in the traffic you can use a filter to slow things down a little. In the filter field type in "http.cookie && ip.src==192.168.69.100" replacing the IP address with the IP address you want to target. This will tell Wireshark to only look for cookies coming from the target device. Hit 'Apply'.
Now this is normally where you would wait patiently for your victim to start visiting websites that you can hijack the session ID from. To speed things along I'm going to go ahead and open the Kickstarter website on my phone. As I opened my browser, the BBC News website was already open and I could see the request pass through Wireshark.
It's worth observing here that the GET request started off as "/news/" as it doesn't need to include the bbc.co.uk part. The server knows it is bbc.co.uk and as such the request doesn't include that. This will make it easier when you're trying to identify websites later on. As I navigate to the Kickstarter website I can see another HTTP GET request come through for "/" which means the root of the site, most commonly the home page. If you select the request, expand the 'Hypertext Transfer Protocol' section at the bottom you can view the host website.
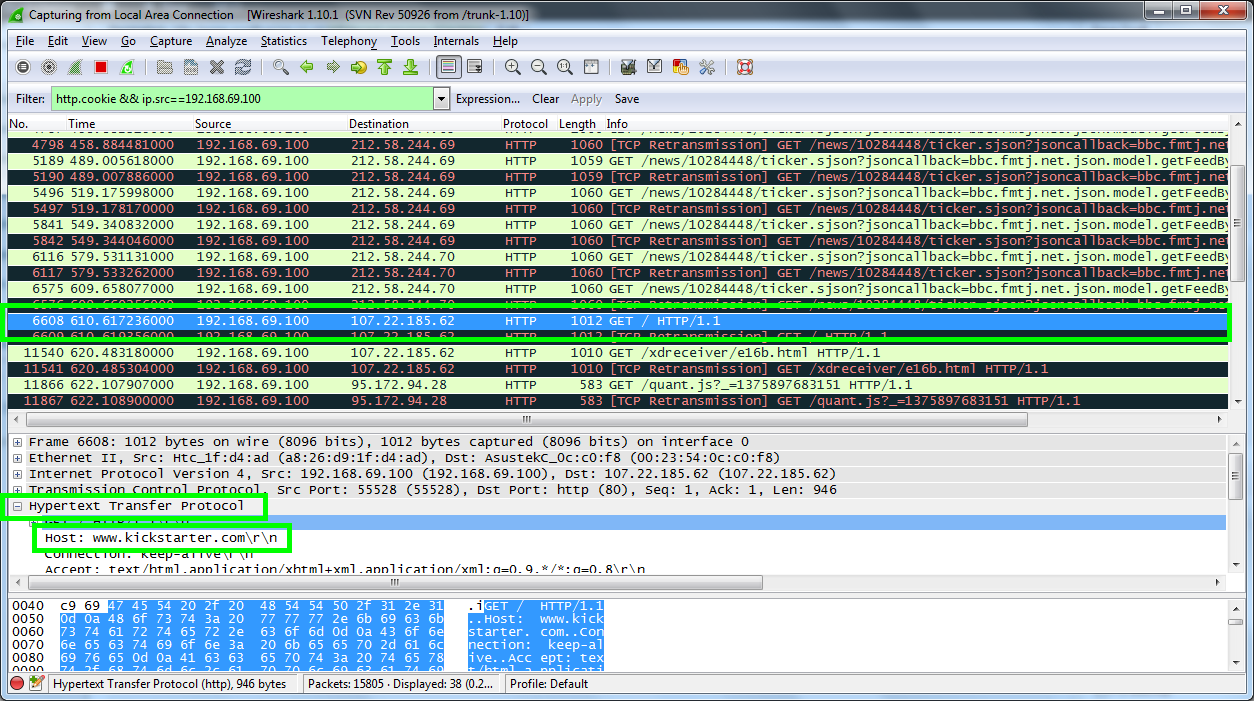
Once you have identified this is a website you want to try and hijack a session for you need to scroll down to the cookie section. Once you find the cookie line, right click on it, select 'Copy' and then 'Value'.
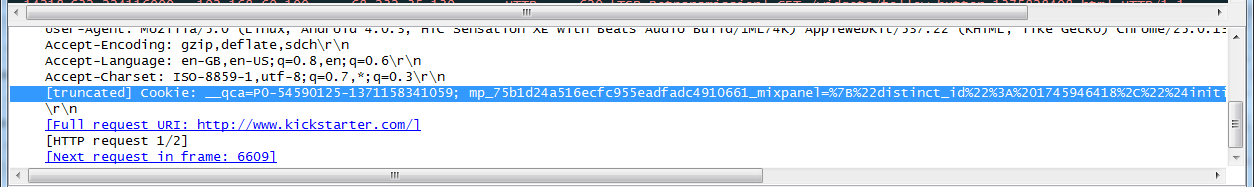
The most difficult part of the attack is trying to determine which value in the cookie is the session ID. In most cases it will be named something like "sess" or "PHPsess" and in the case of Kickstarter it's called "_ksr_session". Paste the cookie you copied in to any text program like Microsoft Word, Notepad or in my case, NotePad++. Select the session ID and copy it.
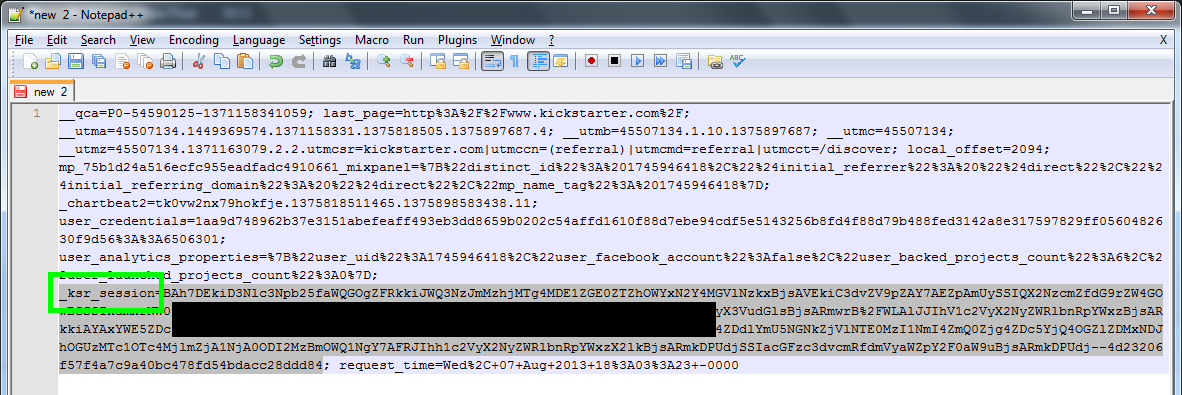
All that's left to do now is to insert the session ID into our own cookie so we can impersonate the user currently logged in on the victim's device. Open up Firefox, go to a cookie manager of your choosing and find the _ksr_session value. Replace this with the value copied from the step above and save it.
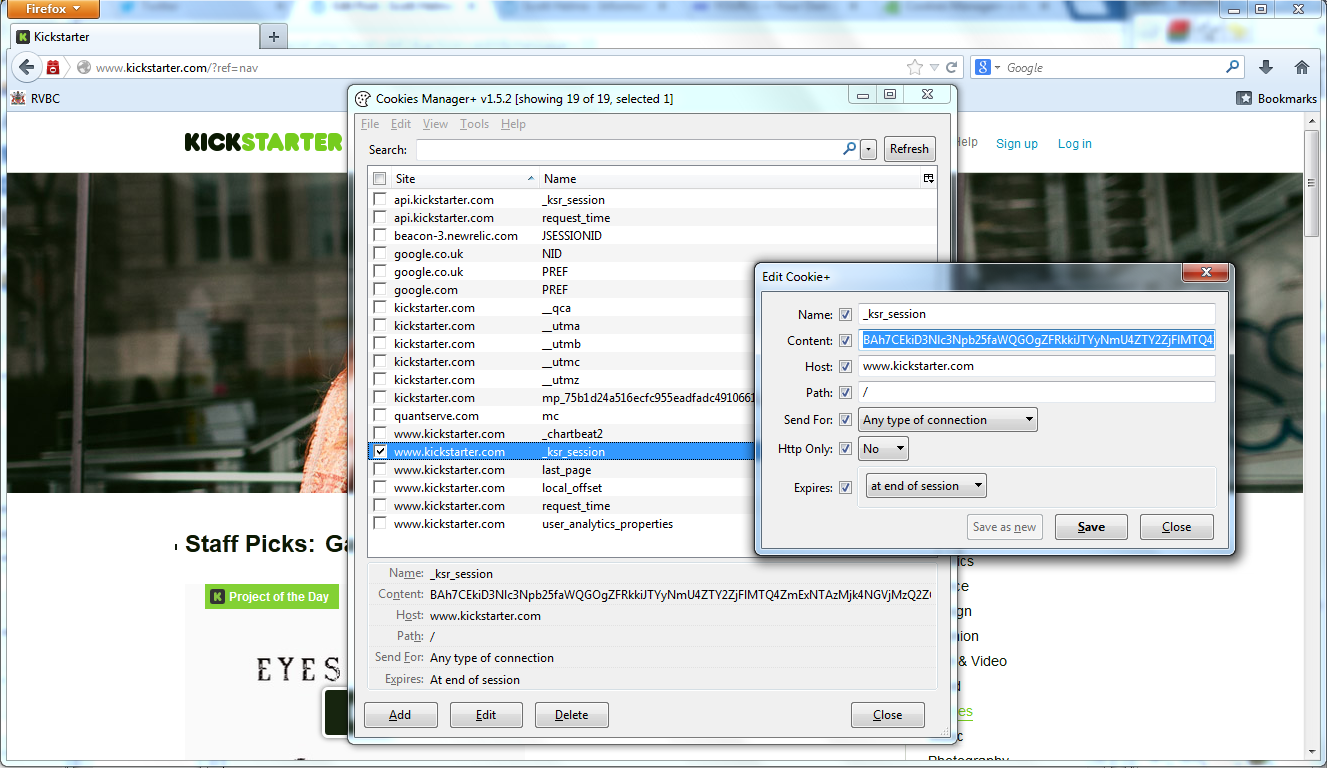
Now comes time for the moment of truth. When you hit the refresh button on the browser it will submit a request for the page but this time it will make the request using the new session ID you have just inserted. If everything goes to plan you will now be logged in as the victim!
Tadaa!
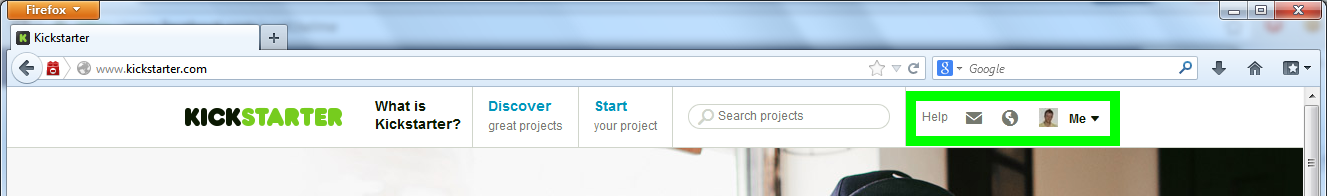
So, now you have the victim's session ID you can do pretty much anything they would be able to do. HTTPS or not you can potentially visit account pages and view personal information, buy some expensive items or generally cause havoc on their profile.
Whilst the process of doing this may be somewhat slow and cumbersome to begin with, once you have done it a couple of times it becomes a breeze. When you can quickly recognise the session ID in the cookie you can hijack a session within minutes of starting the attack. Things like this are always worth considering when you're connecting to networks other than your own. You're trusting the person operating the network, and any other client on the network, to respect your privacy. There are ways to protect all of your traffic whilst using a potentially insecure network and the main one is a secure VPN. I'm going to cover this and other methods of protecting your traffic in future posts so check back and have a read.
As always the information and tools in this blog could get you in trouble if used in the wrong manner! Never use this information to do anything that will get you in trouble, it's intended to be used for informational and demonstration purposes only. Hopefully this highlights the risks involved with connecting to networks where you don't know who or what may be lurking nearby trying to intercept your traffic.
In subsequent posts I will also cover methods to mitigate ARP Poisoning and demonstrate just what Cain is really capable of!
Scott.
Short URL: https://scotthel.me/AdvSessHijack
