Wired Equivalent Privacy (WEP) was ratified in 1999 and intended to give WiFi users data confidentiality comparable to that of a traditional wired network. Although the name implies a high level of security, WEP has several serious and demonstrable flaws that result in it offering very little protection at all!

WEP was the de-facto security protocol used to protect WiFi networks from the mid 90's well into the new millennium. Even now in 2013, almost 14 years after its use was first ratified, you can still find countless networks protected with WEP just walking around your local streets using your phone to pick them up.
Using this blog, the tools I have linked and the demo video you can see just how easy it is for an attacker to bypass WEP security. In an age where the Internet is being used to carry out more and more crime, and where actions online can be traced back to the person who owns the Internet connection, attackers are regularly using networks protected with poor security to carry out criminal activity. Hopefully this demonstration will highlight just how easy this is to do and prompt you to check your WiFi security and upgrade it where needed.
Tools
Oracle Virtual Box: HEREIf you want to install Backtrack to a Virtual Machine on your computer.
BackTrack 5 R3: HERE
The BackTrack pentration testing distribution.
UNetBootIn: HERE
For creating live USB drives to boot the BackTrack distribution.
Alfa AWUS036NH: HERE
The USB WiFi adapter I'm using to carry out the penetration tests. If you already have WiFi on your PC or laptop then you probably don't need this.
List of commands: HERE
A copy of all the commands I will use in the following videos.
Unfortunately there is no real way of strengthening a WEP protected network against this form of attack. Whilst you can take steps to try and inconvenience an attacker, that's really all it would be, an inconvenience. The security protocol is fundamentally flawed and with the rapid progression of computing power over the last decade following Moore's Law it has become easier and easier to break WEP. Even with the strongest possible key allowed by WEP an attack of this nature is still trivial in modern times.
Interestingly I have seen a lot of material online regarding WiFi security and how you can improve the security of your network. I came across most of it whilst I was researching the topic and a lot of it is either incredibly outdated or just plain wrong. Worryingly even the website for the ICO, www.ico.gov.uk, contains advice that is both completely useless and in one instance completely wrong! Let me know in the comments if you spot it.
Here are a few steps that you can avoid:
Hide The SSID
An incredibly large amount of websites suggest that by restricting the broadcast of your SSID you can increase the security of your network as no one will know it's there. Unfortunately the aircrack suite, and tools like Kismet, can de-cloak a hidden SSID in a matter of seconds and do it automatically. An attacker is going to be able to bypass this in less than 2-3 seconds and all it serves to do really is cause an inconvenience when you try to add new devices to the WiFi.
MAC Address Filtering
Another common piece of advice is to only allow specific devices on our WiFi network based on their MAC Address. Whilst in theory this should work the very first steps of my demo video show how you can spoof any MAC address you like for your WiFi adapter. As you can view clients that are authenticated to the network, and their MAC address, you can simply change your MAC address to match theirs and the access point will allow you on the network. This represents a significant inconvenience when you want to add new devices to the WiFi as you need to identify their MAC and insert it in the allowed list on the router but barely does anything to slow down an attacker.
Use A Strong Key
Whilst using a strong key or password in any circumstance is always good advice, WEP security is so broken that it will make close to no difference to an attacker trying to break the key. Using a strong key in my demonstration video I managed to break the key in 3 seconds flat... This advice really should be to switch to WPA or WPA2 and to stop using WEP all together. WPA allows for a much longer key which results in it being far stronger than any possible WEP key. It has also had many of the major security flaws fixed.
Assign Static IP Addresses And Disable DHCP
The Dynamic Host Configuration Protocol (DHCP) is used to assign all devices an IP address when they connect to a network. An IP address is required for any form of communication to occur. If you manually assign all devices a unique IP address and disable DHCP, the theory is that an attacker will not have an IP address and not be able to communicate on the network. Unfortunately once the attacker is authenticated to the access point they can simply sniff packets and extract the information they need. This will show them the IP address range being used on the network and they can manually configure their own just like you did on all the other devices. This represents another considerable inconvenience to you as all devices need to have a unique IP address assigned. This is to avoid conflicts on the network and it makes tracking the use of addresses and adding new devices even harder still. Once you have the WEP key for the network Wireshark will allow you to decypt and view packet contents.
Power Down Your Router When Not In Use
Powering down your router when it's not in use prevents an attacker being able to launch an attack as the router isn't on. This sounds great in theory and seems to make sense, until you realise that for the above attack to work there has to be a client using the network any way! This means the router is only going to be on when someone is using it which also the only time it can be attacked. Again this is just another inconvenience as you realise your phone has been using precious 3G bandwidth all night because you forgot to turn the router back on! This serves no purpose in preventing an attack, unless you never turn the router back on...
Position The Router In A Safe Place
A lot of websites suggest placing your router in the centre of your house or building to reduce the range outside of your walls the WifI network can be detected. Again this seems great in theory until you want to use the WiFi in the garden and you can't pick up the signal. That aside, the even bigger concern here is that just because your phone or laptop can't pick up the WiFi, it doesn't mean an attacker can't. The USB WiFi adapter I use in my attacks is incredibly sensitive and incredibly powerful. I can pick up WiFi networks at the end of my street that my phone can barely detect stood outside the front door. In reality, it doesn't matter where you place the device in most homes, it will be easily detected outside the walls of your building.
Enable Firewall On The Router And Your Computers
Whilst I could never argue with this advice from a general standpoint, it's always a good idea to have firewalls enabled where available, it does nothing to protect your WiFi network. A firewall will stop an attacker trying to gain access to your network from the Internet, or, stop them gaining access to your PC from within your own network. To crack WEP security and use your internet connection an attacker doesn't need to do either of these two things. However, once on the network they could decide to attack computers too so as I say, it's always a good idea to have these enabled anyway, just understand they will not help prevent someone performing this kind of attack.
Change The Default SSID
The SSID, or the name, of a WiFi network has no impact whatsoever on the ability of an attacker to compromise it. If you're happy with the SSID "TalkTalk-A9B4" you can rest assured that not changing it will have no impact at all in terms of the actual attack. That said, I would still advise changing it but for different reasons. If I was looking for a WiFi network to try and break the key for and use the internet on, any network with a 'default' name would be a prime target. If a user has the technical ability to change the SSID they could also have the ability to improve the key strength for example. If they have just un-boxed their router, plugged it in and never changed any configuration, it's much more likely the key will be easier to break and that the admin details for the router are also factory defaults too!Below are some quick guides on downloading BackTrack, creating a bootable USB flash drive and installing a virtual machine using Oracle's VirtualBox.
Downloading BackTrack
As BackTrack is the largest item to download we will start that going first. Use the download link above and skip the optional registration step:
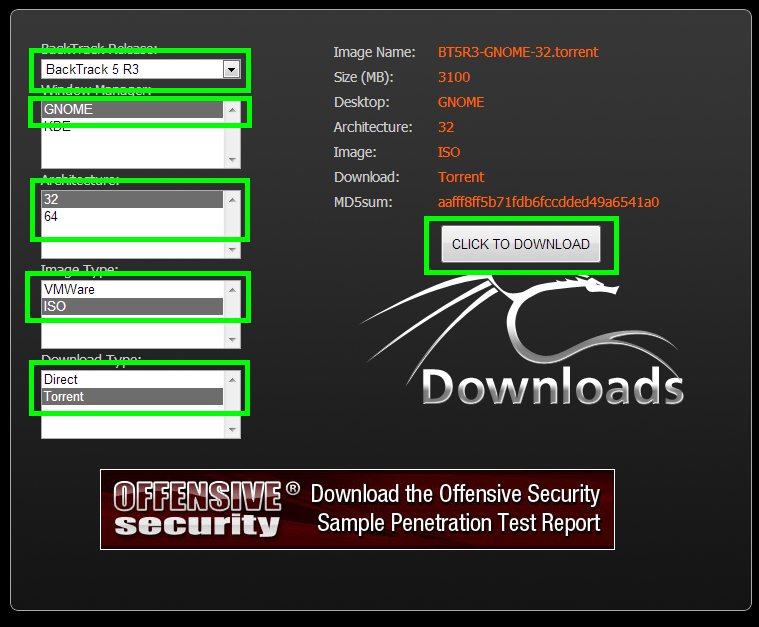
From the download screen you need to select the following:
- Release: The latest available.
- Window Manager: Gnome.
- Architecture: You can stick with 32 for compatibility on all hardware.
- Image Type: ISO (unless you have VMWare Player and want to use that).
- Download Type: If you have a torrent client that will be much faster, if not use direct.
Then hit download!
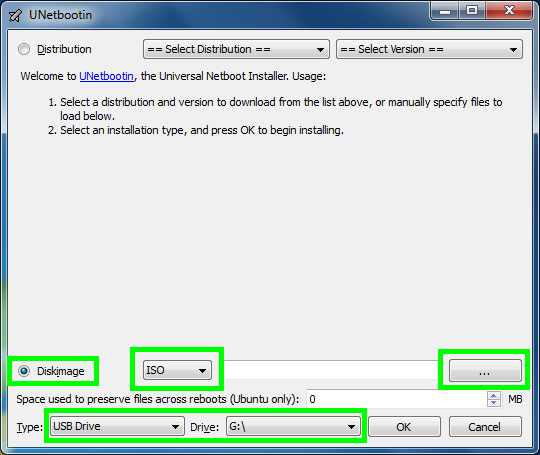
Creating A Live USB With UNetBootin
Download and open UNetBootin and use the following steps:- Select "Diskimage".
- Ensure ISO is selected in the dropdown.
- Click the "..." button on the right and locate the BackTrack ISO you downloaded earlier.
- Set the "Type" to "USB Drive".
- Set the "Drive" to your USB Drive (must be formatted as FAT32).
- Click "OK".
To boot from the Live USB make sure you're BIOS is set to boot from USB Media.
Creating A Virtual Machine with VirtualBox
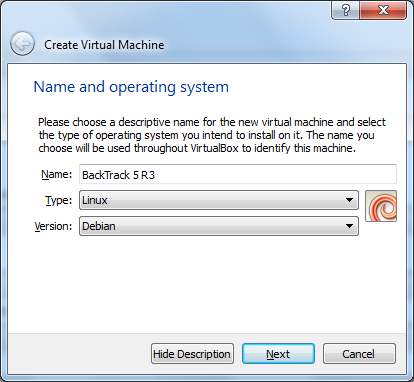
Download, install and launch VirtualBox. Click the "New" button.
Set the name of the virtual machine, select the type "Linux" and the version "Debian".
1024Mb of RAM is best if you have enough on the host machin.
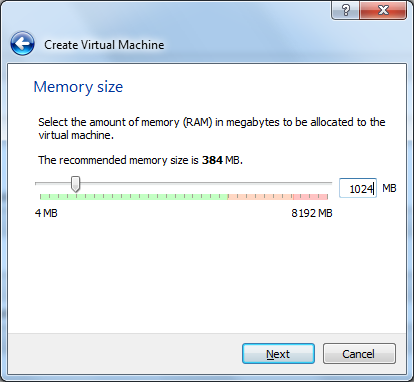
You want to "Create a virtual hard drive now".
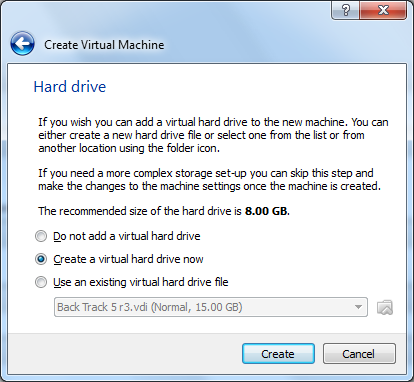
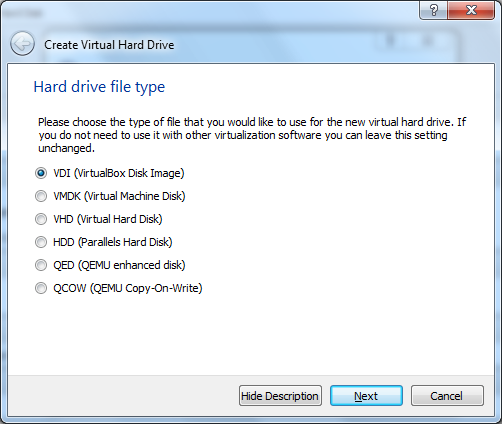
The default "VDI" selection is good here.
Select "Fixed size".
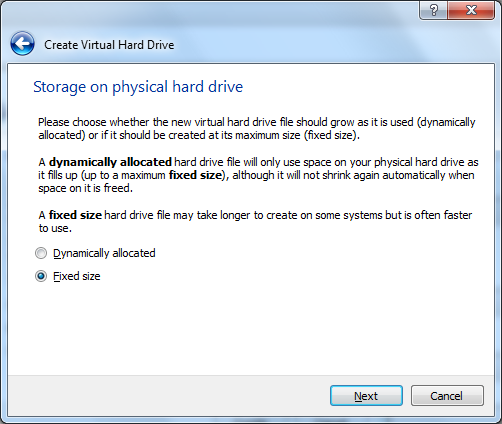
Input "15.00 GB" for the size of the hard drive and click "Create".
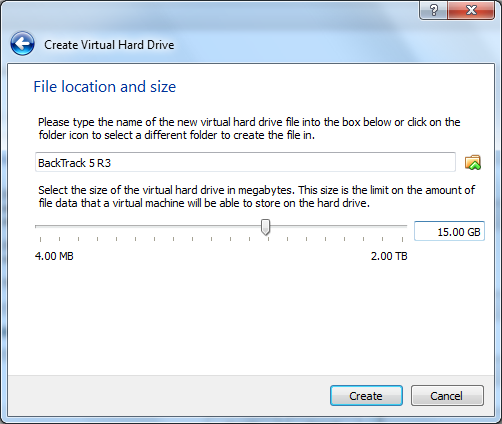
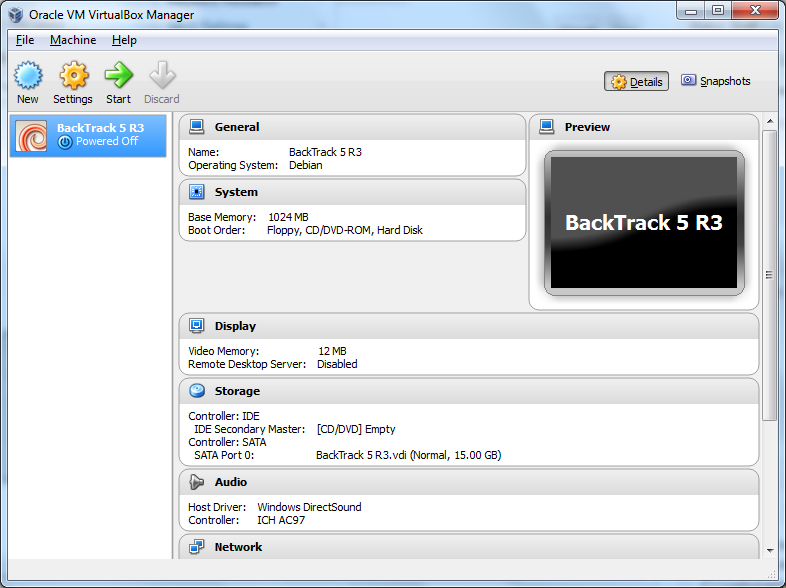
Your VM will now be created!
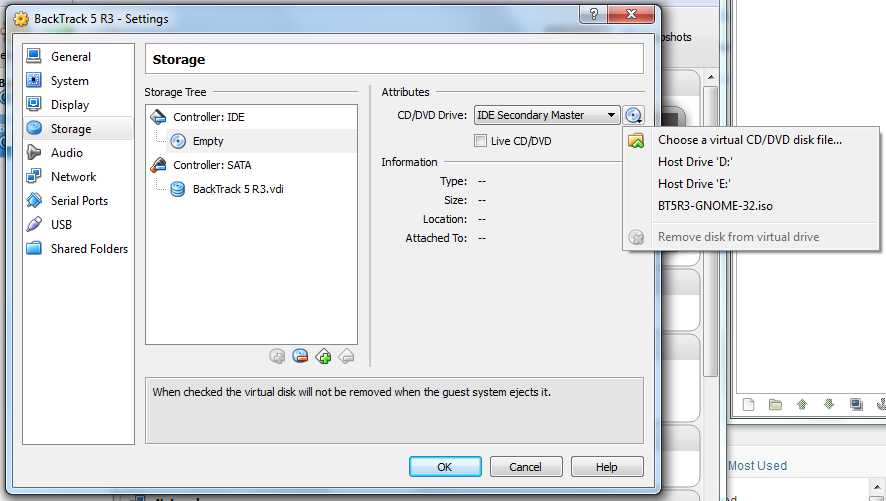
Select "Settings", go to "Storage", select the CD icon, and expand the menu to the right. Sometimes Virtual Box will already have found the BackTrack ISO as you can see in my screenshot or just click "Choose a virtual CD/DVD disk file" and navigate to where you saved BackTrack.
Once you've done that simply hit "OK" and the green "Start" button at the top to boot up your new virtual machine!
Hopefully this blog has provided some insight into the weaknesses of WEP security and if you are using it on your WiFi network then please consider changing to WPA or WPA2 security.
Scott.
Short URL: https://scotthel.me/CrackingWEP
