We recently saw the introduction of one of many new technologies becoming available to site owners to secure themselves in the form of Certificate Authority Authorisation, or CAA. Let's take a look at just how many sites are using it.
Certificate Authority Authorisation
You can read more on my blog about CAA but in short it allows you to specify which Certificate Authorities (CAs) are allowed to issue certificates for your domain by setting a DNS record.
scotthelme.co.uk. CAA 0 issue "letsencrypt.org"
This DNS record means that Let's Encrypt are the only CA allowed to issue certificates for my domain and I do not authorise any other CA to issue. Simple!
CAs MUST respect CAA
As of the 8th September 2017 the CA/Browser Forum, the 'industry body' that regulates browsers and CAs, required that all CAs check and obey DNS CAA records for all names present in a certificate being issued. You can see the requirement in section 3.2.2.8 of the Baseline Requirements which was added as a result of Ballot 187 to make CAA checking mandatory. This means that site operators can now effectively restrict which CAs can issue for them, but just how many are doing so already?
Tracking usage in the wild
Many of you will already know that I crawl and analyse the Alexa Top 1 Million Sites every single day and publish the data. On top of that, every 6 months, I also publish a report on progress made since the last report with the most recent being Aug 2017. I recently made some changes to the crawler fleet I use to crawl, process and analyse all this data to make it a little more efficient and fault tolerant, so I also took the opportunity to add a DNS lookup for CAA records. If you've seen my scan reports before, you will probably recognise this trend!
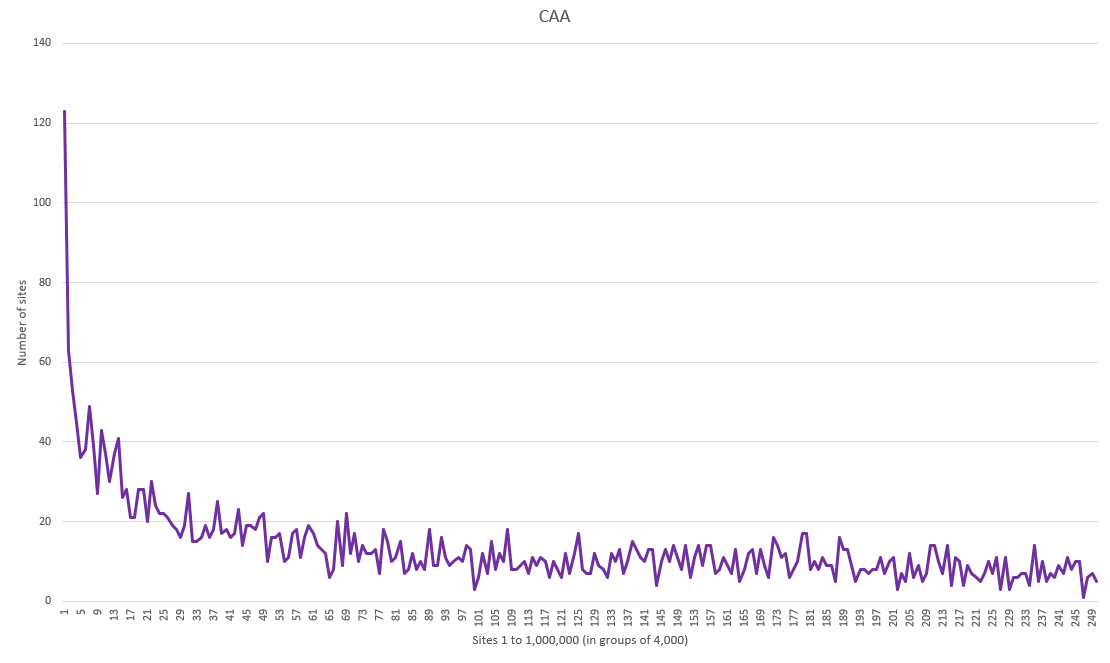
What you're seeing here are the Top 1 Million Sites in 250 groups of 4,000. On the left is the first group which is the top 4,000 sites, of which ~120 have a CAA record, and on the right is the last group of 4,000, of which only ~5 have a CAA record. As is fairly common with these scans the sites at the top end of ranking, the most popular sites, are much more likely to have a CAA record deployed and there is a sharp decline in usage in the top 12,000 sites alone. After that we hit the bottom pretty quickly in the first few groups the graph then slowly tapers off across the rest of the ranking. There's also some interesting data when looking at who is whitelisted to issue certificates with CAA too. Here are the top 20 policies deployed and remember, a policy can contain multiple DNS records to authorise multiple CAs:
CAA 0 issue "letsencrypt.org" x 470
CAA 128 issue "letsencrypt.org" x 175
CAA 0 issue "comodoca.com" x 132
CAA 0 issue "digicert.com" x 107
CAA 0 issue "globalsign.com" x 92
CAA 0 issue "comodoca.com"
CAA 0 issue "letsencrypt.org" x 60
CAA 0 issue "symantec.com" x 40
CAA 0 issue "letsencrypt.org"
CAA 0 issue "comodoca.com" x 37
CAA 0 issue "godaddy.com" x 35
CAA 0 issue "geotrust.com" x 34
CAA 0 issue "thawte.com" x 33
CAA 0 issue "pki.goog" x 26
CAA 0 issuewild "comodoca.com" x 26
CAA 0 issue "rapidssl.com" x 24
CAA 0 issue "letsencrypt.org"
CAA 0 issue "comodoca.com"
CAA 0 issue "digicert.com"
CAA 0 issue "globalsign.com"
CAA 0 issuewild "comodoca.com"
CAA 0 issuewild "digicert.com"
CAA 0 issuewild "globalsign.com" x 21
CAA 0 issue "letsencrypt.org"
CAA 0 issuewild ";" x 21
CAA 0 issuewild "digicert.com" x 20
CAA 0 issue "certum.pl" x 20
CAA 0 issuewild ";"
CAA 0 issue "letsencrypt.org" x 20
There are only a total of 3,404 sites with CAA deployed right now and the 2 most popular policies, and a couple of others further down that I checked manually, account for 772 sites (almost 23% of all sites deploying CAA) and only whitelist issuance from Let's Encrypt. LE do seem to have a disproportionately large share of the sites with CAA deployed and alongside those sites I just mentioned there are many others that allow issuance from LE alongside other CAs too. Another easy to spot deployment is Cloudflare's CAA which you can identify by the presence of their record set:
CAA 0 issue "comodoca.com"
CAA 0 issue "digicert.com"
CAA 0 issue "globalsign.com"
CAA 0 issuewild "comodoca.com"
CAA 0 issuewild "digicert.com"
CAA 0 issuewild "globalsign.com"
You can see in the top 20 policies above that the most common scenario for Cloudflare users is to set the Let's Encrypt CAA record which then prompts CLoudflare to set their records to allow Universal SSL to work. There are other interesting deployments too like HackerOne who have the Cloudflare CAA record set and their own record to allow Amazon to issue non-wildcard certs:
CAA 0 iodef "mailto:caa-reports@hackerone.com"
CAA 0 issuewild ";"
CAA 0 issue "amazonaws.com"
CAA 0 issue "comodoca.com"
CAA 0 issue "digicert.com"
CAA 0 issue "globalsign.com"
CAA 0 issuewild "comodoca.com"
CAA 0 issuewild "digicert.com"
CAA 0 issuewild "globalsign.com"
Every policy recorded is available in the raw data that I make available from my daily scans so if you want to dig through that and look at all configurations (and misconfigurations!) then please do feel free and share anything intersting you find.
Enabling CAA
If you want to enable CAA to protect your domain all you need to do is set the appropriate CAA record/s and you're all set. To make the process of generating your records super easy I'd recommend the SSLmate CAA Generator which is just point and click. That will provide all of the necessary values you need to set and then you set them with your DNS provider or whoever/wherever you manage your DNS. If like https://report-uri.com you're hosted behind Cloudflare then it's really easy to do this in their UI. One thing to note is that when you set your CAA record on Cloudflare they will also add their own records behind the scenes to make sure Universal SSL keeps working. This means if you only use Cloudflare issued certs on the front and a Cloudflare origin cert like we do, you can simply block all issuance by any other CA.
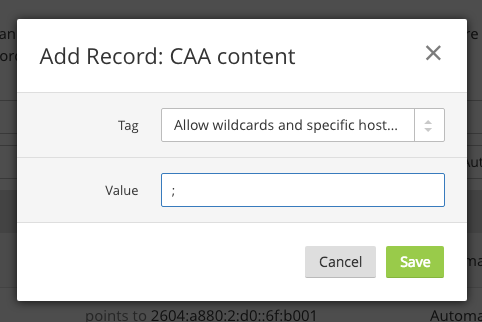
By setting the value to ; you're saying that you don't authorise any CA to issue certificates for your domain, but, as I said above, Cloudflare will automatically add their own values for their issuance processes to continue to work. You can see that in our DNS records if you take a look:
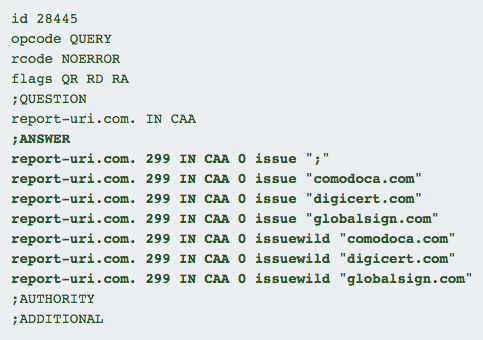
You can see the results here and there's the record I set alongside those set automagically by Cloudflare. This means that I now control who is authorised to issue certificates for my domain which is a really nice improvement in our security and a capability that all sites should exercise.
How many sites can we get to deploy CAA?
I've been tracking CAA for the better part of a week now and have a small insight into how many new sites are deploying CAA each day. That said, it'd be great to see if we can get a huge kickstart and maybe even double the number of sites deploying CAA in a very short period of time. If you do go and deploy CAA on your site then drop a link to your results on the Google Dig tool (here) in the comments below!
